Accelerating Business Success: The Importance of a Prompt IT Managed Service Provider Response
In today’s fast-paced business world, time is money. Every minute of downtime can translate into lost opportunities and revenue. That’s why businesses rely on their outsourced Information Technology (IT) Service Providers to keep their technology infrastructure up and running smoothly. However, simply having an IT service provider isn’t enough – businesses also need a fast […]
The Importance of Customer Experience with Managed IT Services and Cybersecurity
Get expert tips to improve customer experience with managed IT services and cybersecurity. Learn today with Great Lakes Computer! Customer experience is a crucial aspect of managed IT services and cybersecurity. It is not enough to provide a secure service; businesses must ensure that customers receive the best possible service when using their managed IT [...]
Great Lakes Computer Forms Partnership with BIXOLON to Offer Best in Class Printing Solutions
Supercharge Your Business with a Zero- Cost Premium Intranet Unlock the Power of Effective Communication with Our Easy, Free Guide, or Keep Scrolling To See The Video!*No Email Required, Get Access Immediately Download Your Free Guide and Transform Today The Power of SharePoint Intranet Revolutionize Your Business Operations for Free You already have the key [...]
Why Honesty is the Best Policy when Filling Out Cyber Insurance Forms
Get prepared for Cyber Insurance deadlines! Learn the importance of honesty when completing forms for your coverage. Tips for Completing Cyber Insurance Forms: Don’t Risk Your Coverage by Fudging the Truth The World Economic Forum (WEF) says that cyberattacks are among the top 10 risks in the world. To mitigate this risk, companies often purchase […]
Need Quick and Reliable Epson Printer Repair? Trust Our Experts!
The Importance of Epson Printers in Today’s Business World In today’s business world, printers have become an indispensable tool and Epson printers have gained widespread popularity among businesses of all sizes for their reliability, affordability and quality output. Epson printers are high-quality, but any machine can break down due to regular usage or malfunctioning components. […]
Cybercrime As A Service (CaaS): What Every Business Owner Needs to Know
If you're an entrepreneur, you know how cybercrime can impact your business. Read to learn more about Cybercrime-as-a-Service. Cybercrime-as-a-Service (CaaS) is an emerging trend that you should be aware of as a business owner. CaaS describes offering hacking tools, services, and expertise to criminals to execute cybercrimes. In 2022, this cybersecurity menace led to damages [...]
Enforcing Cybersecurity in the Age of Credential Phishing
The shift from office work to remote or hybrid models has evolved and frequented cyberattacks, phishing in particular. The pandemic necessitated operational changes in the office space to minimize the spread of COVID-19. However, the resulting office changes may remain long-term because of the benefits of working remotely and technological advancements. One pivotal factor that [...]
Establishing Effective Company Cybersecurity Policies
Are you looking to improve your cybersecurity protocols and policies? Read our latest blog post for best practices on establishing effective company cybersecurity protocols for protecting sensitive business data. As businesses increase reliance on digital technologies and services, having a solid foundation of company cybersecurity policies and protocols is paramount to keeping information secure and [...]
How AI Can Benefit Your Cybersecurity Strategy
Ensuring the safety of your digital assets is of utmost importance. As the risk of cybercrime increases, it is critical to employ the most up-to-date practices to protect your data and networks. Integrating Artificial intelligence (AI) into your cybersecurity strategy is a highly- efficient and contemporary way of doing this. Below, we’ll explain how AI […]
How to Ensure Your Data is Secure in Case of a Breach
Data security is a crucial part of running any business. Cybersecurity breaches can have a huge impact on an organization's reputation and revenue. This makes it essential to have a robust data breach response plan in place. The Cost of Cyberattacks Small businesses are particularly vulnerable to data breaches, with 43% of attacks targeting them. [...]
How to Plan Your 2023 Cyber Spend
A cybersecurity budget can seem like a daunting thing to calculate for any size organization, but it doesn’t have to be. As long as you and your executive team assess and understand the risks you face, and the solutions you need to protect against them, you can calculate your cost.
Why the Demand for Outsourced IT Services is Exploding
Every business looks for ways to save money, while still retaining the best possible quality for its own internal systems and for customer service. IT security and IT services are no exception to this. These factors are a key part of why the demand for managed outsourced IT services is exploding worldwide.
Nothing is More Important Than Data Backup
The underlying backbone of all digital and IT security for any individual, organization or business is data backup. The reason why boils down to this: Even if you lose everything else, suffer a massive hack, or lose your IT assets to some major physical disaster, a strong data backup will at least keep your core […]
Phishing Emails: Would You Take the Bait?
Spam email attacks (otherwise known as phishing) are one of the largest threats facing all businesses today. They are everywhere and affect everyone. Plus, they are continuing to grow in sophistication and number, so there is no end in sight. And what’s worse is that most people are aware of this large danger, and yet, […]
4 Key IT Vulnerabilities and How to Prevent Them
We currently face a growing IT security threat landscape. Therefore, organizations of all sizes need increasingly professional and threat-specific solutions for their IT security needs if they really want to stay protected. The cost of failing to do so can be enormous. As IBM’s 2022 Cost of Data Breach Report found, an average organization-level data breach this […]
Vulnerability Tops List of Cyber Security Scares
We always talk about the importance of being protected from cyberattacks and how smaller companies are often at risk of being a target for hackers. But it’s also very easy for a larger company to be breached.
Cybersecurity Post Pandemic
The COVID pandemic affected many things across the country, but the impact it had on the IT world was catastrophic–particularly when it comes to cybersecurity. Employees working from home opened many businesses up to cyberattacks since many used unsecure networks to keep business operations moving. At the same time, it gave many cybercriminals the time […]
Having Trouble Obtaining Cyber Insurance? You’re Not Alone
Learn How to secure & insure your organization, plus, get FREE pizza! IT has gone from being a minor part of most businesses (particularly smaller ones) to being one of the key aspects of their success and growth. An unfortunate side effect of this growth in importance has also been to turn an average company’s […]
Apple Operating System Vulnerability Leads to Critical Updates
It seems like there is constantly a new update for the Apple platform. Just last month (August 2022), Apple announced the 15.6.1 update which included some critical and necessary changes due to a recently discovered vulnerability in the operating systems, only to then be followed by an announcement this month that another update is coming […]
Cyber Insurance is Becoming Harder to Obtain
As the complexities and diverse risk profiles for protecting business IT security increase, cyber insurance coverage is becoming harder to obtain. Before IT security became as important as it is now, cyber insurance wasn’t something that many organizations thought much about. If they did feel a need for it, it could often be easily bought. […]
Why Cyber-Ready Now is Not Enough
We frequently discuss and stress the importance of protecting your digital assets today. Across the country, this is becoming more important to businesses. Case in point: According to Price Waterhouse Cooper’s June 2021 U.S. Digital Trust Insights Snapshot, “Cyber threats jumped to CEOs’ number-one concern in the U.S., and number-two globally.” The study PWC conducted […]
How to Protect Your Business Before It’s Too Late
IT security consists of multiple facets and is crucial in today’s deeply digitized world. As a business owner, your IT components—the sensitive data, software, and hardware—are the backbone of your company’s success. So, it’s crucial to protect them beyond just hack attacks. Other problems that can easily strike include data loss, customer data leaks that […]
Disaster Protection: Why Your Business Needs BCDR Now
Disasters sometimes strike. They can take on many forms (fire, hurricane, earthquake, theft, etc.) and either be localized or fully global. The COVID-19 Pandemic was one particular example on a global scale, but it’s far from the only kind of catastrophic event we can expect. That’s why it is important that your business has a […]
Be Ready! Your MS Office and Outlook Could Stop Working in October
If you use Microsoft Office and Outlook, it may be time for preparations to begin! Microsoft announced that starting on October 1st, 2022, early versions of Office and Outlook will stop working! It’s been in the media since last year. We at Great Lakes have reminded our customers through several emails. Now is the time […]
Essential Two-Factor Authentication Basics
One of the unvarying truths of the digital world in which all of us–business owners or consumers–operate is that cybercriminals constantly evolve their attacks. This means that the things we used to do for secure access to sensitive account systems like online banking, stock apps, or email accounts usually have to evolve too. One of these evolutionary methods has been two-factor authentication, also known as TFA or 2FA.
Simple Steps to Improve Your Company’s Cybersecurity
As a general rule, digital security—for companies and web-connected organizations of all types—is subject to all sorts of potential threats. These could come from online organized crime, hostile foreign governments, individual hackers, and fraudsters with a penchant for stealing data or funds.
Now In Sandusky! Broader Reach, Same Great Service.
Great Lakes Computer is opening a convenient new location! While the headquarters will remain in Avon, Ohio, we are adding a satellite office near downtown Sandusky. This prime spot will enable us to better serve our traditional business customers in Northwestern Ohio. This will also allow us to expand our new consumer offerings in the […]
GLC Partner, SentinelOne, Acquires Attivo Networks
It’s common knowledge that standard antivirus and firewalls are no longer enough to properly protect your business in today’s tech savvy world. As hackers and viruses become smarter, your protection needs to be stronger. So to bring our clients the best Endpoint Detection and Response program to protect their networks, we partner with SentinelOne. They are one of the best innovators when it comes cybersecurity solutions.
What to Look For in an IT Outsourcing Provider
Many small to medium sized businesses today at some point or another consider IT outsourcing. Gaining access to enterprise level IT support at SMB prices makes a lot of business sense. But, as with any vendor, it’s important to find the right Managed Services Provider for your business’ particular needs. Here are some criteria to […]
Transferring Cybersecurity Risk is About to Get Complicated
Many organizations have historically made decisions to transfer cybersecurity risk by purchasing a cybersecurity liability insurance policy from an insurance carrier. Transferring risk has become popular because the magnitude and variety of cybersecurity risk that organizations are attempting to manage is overwhelming and resources to mitigate or eliminate the risks are scarce. Obtaining insurance takes […]
Penetration Testing? What Is It and Why Do You Need It?
Risk associated with cybersecurity threats and exposures motivate organizations to implement protective controls intended to keep their digital assets safe from malicious computer hackers. Firewalls are installed at the network perimeter to keep unauthorized users from accessing the private network. Anti-virus software is installed on computers and servers to enhance overall endpoint security. Sensitive data […]
3 Reasons SMBs Need Managed Service Providers
Managed Service Providers (MSPs) are often brought in to handle specific IT tasks that small-and-medium-sized businesses no longer want their IT guy doing in-house, because they aren’t the best use of a salaried employee’s time. Projects like repetitive monitoring and maintenance tasks that can be automated are easy to hand off. But MSPs can completely […]
Why Business Cybersecurity is a Huge Problem for 2022
In an increasingly digitized world, cybersecurity is becoming an ever-growing, vitally necessary burden–and problem–for thousands of organizations. This applies to government bodies, institutions and businesses of all sizes. This isn’t just a flippant conclusion either. The World Economic Forum (WEF) recently released its “Global Risks Report 2022” and guess what subject ranked as one of […]
How to Expose (or Uncover) Your IT Security Risks
Conducting a vulnerability assessment is important because the exercise will identify security flaws that exist in your information technology environment before they are discovered by a malicious computer hacker. Once the vulnerabilities are discovered, you can correct them and lower your risk of becoming a victim of a successful cybersecurity attack.
Guest Wi-Fi – A Necessary Evil
The more windows and doors you put into a house, the more points of access a would-be intruder has. Your internet connection, your servers, your employees smartphones and laptops, and your WiFi controlled thermostat are all windows into your data infrastructure. You do your best to control who can access these and inform them of […]
Crucial Managed IT Services Benefits for Your Business
IT maintenance is fundamental for just about every business in today’s world. It’s important for the most basic reason that IT is an inescapable part of managing even a tiny company, and also for the sake of firm security. The security angle is especially vital due to the increasingly rampant expansion of cybercrime. In fact, […]
Why the NIST Cybersecurity Framework Matters for Your Business
Cybercrime is only increasing in today’s world. During the COVID-19 pandemic alone, the number of cyberattack cases has risen by a whopping 600%. The consequences of these hacks and data thefts especially affect small to medium-sized businesses since they often don’t have robust internal IT resources to fight off all possible threats. But despite internal […]
Proactive vs. Reactive IT Management
When it comes to small businesses, we see plenty of reactive IT management. There are obvious cost concerns when it comes to owning a small business, so owners wait until a problem arises before putting resources toward solving it. However, savvy business owners recognize that a proactive approach to IT maintenance can lead to greater […]
Your Essential Guide to Phishing Email Scams
Phishing is alive and kicking as one of the methods most widely used by cybercriminals for penetrating the IT networks of organizations and businesses both small and large. The reason why is simple: It works.
A Basic Guide to Cybersecurity Penetration Testing
We get asked this question all the time: What’s the best way to confirm that your business’ IT security is firmly protected? Sure, you can implement all kinds of security measures, or have someone else with plenty of professional experience do it for you. But to be even more certain, there’s another trick to try: […]
5 Ways Managed Print Benefits Your Business
When you have existing printers you’ve already bought and paid for, it’s tempting to think that maintaining your existing fleet will cost less than purchasing new printers or signing up with a managed print services (MPS) provider. Why replace them if it’s not absolutely necessary?
The Top 4 Cyberattacks of 2021 (So Far!)
Cybercrime evolves at least as rapidly as the wider digital landscapes it targets. Arguably, it’s sometimes even the faster, more agile player in the race. Key evidence of this is the simple fact that instead of shrinking, cyberattacks have only become larger and more brazen in recent years. Far from being an exception to these […]
SOC-as-a-Service: What You Need to Know
Today’s cyber criminals are clever, sophisticated, organized and typically determined to profit from the theft of sensitive data–by selling it on the dark web or by extorting organizations with ransomware and distributed denial-of-service bombardments.
Why Your Business Needs a Managed Services Provider
How secure is your business from cyber threats? Take a look at some of these latest cybersecurity statistics: As of late 2021, the number of malware infections against individual computers and business networks has increased by over 2000% since a decade ago. Roughly 93% of these are delivered via email, and neither of these stats […]
Build a Human Firewall for Your Business
Establishing a human firewall in your business is more important than you think. Consider your employees. On one hand, they are your single most important business asset. The diligence and know-how of your staff can make or break not only your bottom line, but also your company’s ability to serve its customers securely. On the […]
Simple Solutions to Productivity Blockers
Technology makes our lives easier… most of the time. But sometimes, getting that technology to work the way it should when it should takes more work than we’d like it to. How often have you been held up because your office printer is giving you error messages or failing to sync with your laptop? Ever […]
How to Protect From Threats While Using Microsoft Office 365
Microsoft Office 365 is used by thousands of organizations and individuals through its Consumer, Small Business and Enterprise versions, and cyber criminals have taken notice of this. Consequently, just as these hackers have attempted data breaches through other cloud services, they’ve done the same with Office 365 products. One example of this is the fact […]
15 Must-Dos to Protect Your Business from a Cyber Attack
Cybersecurity is more critical now than ever. Those seeking to access your information are constantly upping their game. Whether they slip in through the backdoor with a simple malware-laden phishing email or they quietly enter through your network and encrypt your data, you need to be prepared. What can you do to prevent data loss […]
The Ransomware Tide is Rising
Ransomware has been a problem for businesses, individuals and organizations for years, but it has reached endemic proportions in the last couple of years. According to U.N. Findings, since the COVID-19 pandemic, email-based malicious attempts on organizations have risen by a whopping 600% or more.
What are Managed IT Services?
Managed IT services are growing at a rapid rate, with a recent survey estimating that almost 69% of small to medium-sized businesses (SMBs) hire at least one type of IT service provider. So what are managed IT services, how do they work, and why would companies consider using them?
3 Tips to Circumnavigate a Skills Deficit and Improve Your Security
Despite the fact that cyberthreats have never been more prolific or problematic, the majority of organizations believe they lack the cybersecurity talent needed to stem the flow of cyberattacks. In fact, 70 percent of IT professionals think there is a shortage of cybersecurity expertise.
Focus on Business Development By Hiring a Managed Services Provider
Professional IT services definitely have a niche for themselves in the U.S. small business landscape: Of the roughly 3.7 million small businesses operating in the United States currently, over 57% of them feel a strong need to improve their existing IT infrastructure. This means improvements to the quality of their security infrastructure, IT staffing and […]
7 Tips to Keep Your IT Cool in the Heat
Don’t be fooled by brisk morning temperature drops–there are still many hot days to come this summer. Your IT hardware wants to stay as cool as you do and a spike in temps can lead to overheating, which can cause a lot of issues for your business network and data. We’ve put together seven simple […]
Reduce Costs With Managed Print Services
Saving money on budgetary expenses is something that any business needs to stay competitive and keep profitability as high as possible. This applies especially when cost savings can be achieved without biting into the quality of product or service that customers receive. There are many ways to pull this off, but one of the more […]
Simple Tips to Keep Your Business Data Safe
Business data is vital to keep safe given increasing threats in the marketplace, such as identity theft and various forms of financial fraud. Fortunately, there are simple controls you can implement to mitigate risks to your business and clients’ confidential information. Here are some tips to help you establish strong data security.
Should Your Business Outsource IT?
At least 83% of corporate IT leaders are either already outsourcing or planning to outsource their IT to professional external management services in 2021. There are more than a couple of good reasons for this. As the post-COVID economy increasingly moves towards the streamlined digitization of de-localized offices, companies worldwide are being forced to cut back […]
Small Business Security Tips
The dangers associated with email and web security continue to grow, even more so now due to the pandemic. According to one study, though 71% of Americans are still working from home today, when business returns to normal, 54% of them want to continue that. If you’re a small business considering allowing your employees to […]
The Increasingly Risky Web
It’s important for your business to have strong internet security in place, ensuring your employees are working safely and mitigating the risks.
Increase in Email Threats
Businesses face all kinds of threats every day—competitors, the economy, laws and regulations, and increasing employee benefit costs to name a few. But cyber threats are increasingly becoming one of the more common threats that companies regularly face. In fact, the FBI estimates that more than $5 billion has been lost worldwide to email scams. […]
Improving Work-From-Home Security
According to research from security software provider Malwarebytes, roughly 20% of organizations may have suffered a security breach caused by remote workers since the beginning of the COVID pandemic. This is a worrying but predictable statistic and one that could have been easily mitigated by improved security in these companies. Here are six key work […]
Email Security Event from Mimecast
We cannot stress enough the importance of protecting your company’s email accounts from spam, phishing attacks and malware. Cyber criminals continue to become more creative in their attacks, and so it’s crucial that you have proper email security measures in place to keep your business safe.
The Importance of Email Security
Email security is so crucial for businesses and organizations. It closes a gaping door to fraud, theft and network hijacking.
Phishing Email Attacks on the Rise
Since the COVID-19 pandemic heavily shifted work patterns for millions of people around the world, one of the biggest changes, particularly among white collar workers, has been a move towards working from home wherever possible. As a result, millions of employees are accessing sensitive corporate networks from outside secure office settings. Naturally enough, this creates […]
Cloud Computing in 2021
Though it launched in the late 1990s, the popularity in Cloud Computing has grown exponentially due to a little thing called COVID-19. With many employees working remotely, the need to access data and continue work operations from their homes was (and continues to be) critical to the survival of many businesses. In fact, research companies […]
Why Government Services are Turning to Managed IT Services
Today’s economic environment requires state and local government agencies to leverage IT resources if they intend to effectively control costs and streamline their services. Unfortunately, the government’s IT system faces many challenges. They include a lack of transparency due to the use of outdated technology solutions, insufficient staffing, and slow changes due to bureaucracy. To […]
The 6 Keys to an Effective SOC
Every 11 seconds. That is how often experts predict a ransomware attack on a business will occur by the end of 2021. With that in mind, businesses can no longer push cybersecurity to the side, or just put up a basic firewall. Protecting your business’s data is crucial for the safety of everyone involved, and […]
Benefits of a Managed Print Provider
Even with the digital revolution, printing is still a significant part of almost all businesses today. Nevertheless, many companies do not have a clear picture of their overall print costs. According to a white paper published by Xerox, most companies spend approximately 1 to 3% of their total annual revenue on printing. As such, print costs […]
Digital Risk: Protecting Your Most Important Asset Webinar
Data breaches are a real threat that should be taken seriously, and SMBs have a higher susceptibility of suffering a breach. It’s important to understand the potential threats, how they can affect your business, and what you can do to reduce the risks.
Understanding POS Cash Registers
Retailers handle various transactions daily, so it’s key for those businesses to be equipped with the necessary hardware and software to smoothly, seamlessly, and quickly handle large volumes of daily transactions. But which transaction-processing solution is best for your business?
Technology Preparations for an Office Move
Moving is stressful—especially when it comes to an office move. It requires careful planning and preparation, otherwise it can result in major work disruptions, sometimes halt productivity entirely for your business, resulting in income losses. Taking the time to specifically focus on, think through and plan out your company’s technology move can help avoid catastrophe.
The Changing State of Backup
Traditional backup tools have become obsolete and unable to offer reliable backup data security. Technological advancements have led to more efficient backup systems that protect businesses’ IT assets while supporting growth.
Disinfecting Your Workstation
As we continue to face the coronavirus pandemic, everyone’s safety remains a top priority. Therefore, washing our hands regularly, keeping a safe distance from one another and wearing masks is extremely important since the primary way COVID-19 spreads is through respiratory droplets in the air. However, the jury is still out in terms of if […]
Keeping Up with Your Office Printer
As the pandemic continues in this country, so does working from home for many Americans. In fact, one study shows that roughly 42% still work from home. For business owners, it presents multiple problems and required adjustments, but what many don’t think about is what does that mean for your office technology, just sitting there […]
Why IT Support Is More Critical with a Remote Workforce
According to a survey conducted by the Bureau of Labor Statistics, only around 7% of U.S. employees had access to remote work benefits as of 2019. Then the COVID-19 pandemic swept the world—and the nation. Suddenly, many companies were scrambling to support remote work forces as a way to remain economically viable during shutdowns. According to Statista, […]
2 Keys to Successful Team Collaboration Post-COVID
As the COVID-19 pandemic continues to impact the economy, companies across the globe have been forced to seek digital reforms to protect their employees and consumers. Businesses have no choice but to review and modify their operational strategies to find new ways to function.
Working from Home = Virtual Private Networking
With all that’s happening in the world right now, home is becoming the workplace for many of us. However, depending on your area of employment, that can present a number of problems.
2020 Technology Trends to Watch For
When it comes to computer technology, it’s important for business owners to stay on top of the trends—ahead even. Not only to make sure they’ve updated their software and replaced equipment with the latest releases, but to keep an eye on the bigger technology evolutions ahead to avoid being left behind.
The Trouble with People
A standard practice for businesses today is to invest in cybersecurity. However, data breaches still continue to happen daily, and compromised data is becoming more and more common. And unfortunately, it’s got very little to do with your security investment, and everything to do with the people that work for you. In fact, a recent […]
What Does EOSL Mean for Your Hardware?
End-of-service-life (EOSL) announcements can lead to concern for IT managers. Each year, IT hardware manufacturers decide they will no longer support certain models of storage, servers, or network hardware. In the wake of this, IT folks are left with some tough choices like whether they will be forced to upgrade or if they want to […]
Top 3 Ways MSPs Can Help Your Business
Old technology, backup issues, millions of cables…. The list goes on and on of all the common IT problems businesses face. And often, owners don’t have time to deal with them. They just need the problem quickly fixed so work can continue. For small businesses who don’t have an IT department, what’s the solution? A […]
Windows 7 End of Life is January 14th, 2020
On January 14, 2020, Windows 7 will reach end-of-life (EOL) and will no longer be supported by Microsoft. If you haven’t started mapping out your migration to Windows 10, it’s time to act. Once a product reaches its end-of-life, no new features or fixes are released for it – however Microsoft did announce in September it […]
The Newest Malware – Fake Windows 10 Update
Great Lakes Computer is always on top of the latest cyber attacks and there’s a new one to beware of – the fake Windows 10 update. Portrayed as a critical update, this ransomware will install an executable .NET file that will infect your computer and request that you make a payment to recover your data. […]
The Zero Trust Model for SMB IT Security
Protecting your business from cyberattacks is something to take seriously—especially for small businesses. With the speed of their growth and their often-limited budgets, small companies often have to prioritize items and sometimes, having a strong cybersecurity system can feel less important—but that kind of thinking couldn’t be more wrong. Smaller businesses make up almost half […]
Office Space: Modern Trends in Workplace Layout
There are many decisions to be made when running a business – branding, staffing, marketing and operations are all important. But you need a place to operate and you want to choose the office arrangement that best fits your requirements. Will you lease a traditional office space? Or perhaps it’s a shared office or a […]
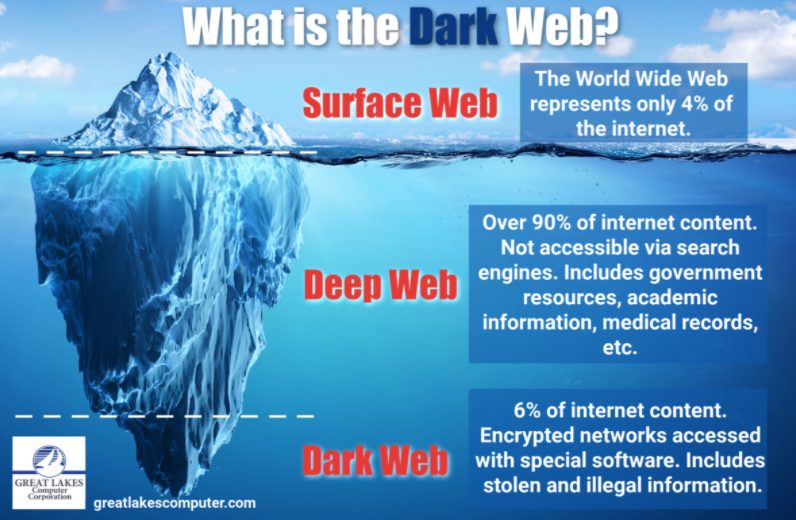
The Dark Web: What is it and why should you care?
When you hear about the Dark Web, you may think the very idea is based on fiction, innuendo and fear-mongering. After all, how could it be so bad? It’s as though the boogeyman joined forces with the worst cyber stalker and decided to let loose their evil machinations by deploying thousands of malicious attacks and […]
Break Fix or Managed Services – Which makes sense for you?
If you run a business, you probably use some variation of IT hardware to do it. To keep that equipment running smoothly, you’ll run across the need for maintenance, which can come in a couple forms. Managed IT Service contracts are proactive and include ongoing maintenance, monitoring and support, while the break fix model is […]
Small Businesses Looking for Security Use Managed Services
Robust security is no longer a “luxury” that only enterprises can afford. Small businesses are at greater risk for both their limited security resources as well as their reputation for being lax in valuing strong defenses. It’s a critical weakness that cyber criminals will exploit and they know SMBs are likely low hanging fruit. A […]
Learn How to Prevent Phishing by Spotting It [An Infographic]
It’s time to get serious about thwarting phishing attempts. While these attacks are increasing in frequency, we can decrease their success rate with just an ounce of prevention. It doesn’t matter how new the approach is, the trick is the same. It’s all about duping just that one person into clicking on a link or […]
Are Managed IT Services Right for You?
Technology plays a central role in business, making it a key component of almost every company. Staying on top of your business’s IT game can be a real challenge, as the technological environment is always changing. Overwhelmed with choices and a lack of expertise, many companies often overspend on IT without understanding which technology expenses […]
10 Questions Law Firms Should Ask Their MSP
Managed IT services for law firms has evolved from its early days of providing offshore support services, data center space and outsourced IT hardware. The strategy of managed IT services has now emerged as a valuable approach for law firms who choose to partner with an expert services provider.
Raising the Bar: How to Modernize Cybersecurity in the Legal Industry
Fifteen years ago, the Harvard Business Review asked its readers, “Can you trust your law firm?” The question then referred to whether corporate lawyers were providing sound advice to their clients. Today, it would also have to account for their approach to cybersecurity. The entire legal industry faces unique challenges in ensuring proper stewardship of […]
The Latest Ransomware Attack – SamSam
We keep abreast of the latest cyber attacks and here’s one that we’re seeing a lot of coverage on we think you should know about–SamSam.
You Hire a Mechanic for Your Car, Why not an MSP for Your IT?
For most people, owning a vehicle means you occasionally need to take your car to the shop for maintenance or repair because you simply lack the expertise–and most people don’t think twice about doing so. But, those same people are using the internet to operate their business and choosing to handle the complex management of […]
October is National Cybersecurity Awareness Month
October is National Cybersecurity Awareness Month (NCSAM). NCSAM is a collaborative effort between DHS and its public and private partners – including the National Cyber Security Alliance (NCSA) – to raise awareness about the vital role cybersecurity plays in the lives of U.S. citizens. At Great Lakes Computer, we understand the value of effective cybersecurity and […]
Hurricanes and Hackers – Are You Disaster Ready?
Threats to your business come in many forms, from Hurricane Florence threatening the East coast to Harvey in Accounting opening an infected email. While there are many steps you can take to reduce your exposure, it's almost impossible to prevent disaster completely. Your best move is to have a response plan in place to help [...]
What the Three Little Pigs Can Teach Us about Cybersecurity
Last night, as I was putting my kids to bed, I read them the classic children’s story, “The Three Little Pigs”. And you know what it got me thinking about—cybersecurity. Probably everyone in the audience is familiar with the tale, but I’ll lay out the basics just so that we’re all on the same page. [...]
Ohio Data Protection Act Just Passed. What Does It Mean for You?
Ohio legislatures just passed the Ohio Data Protection Act, which gives companies a safe harbor in the case of a data breach. Companies that adhere to the NIST Cybersecurity Framework will be entitled to an affirmative defense to any cause of action sounding in tort that is brought under the laws of Ohio or in [...]
Legal Industry Late to the Cloud, But They’re Coming.
In the early years, cloud computing was taken on by the innovators and early stage adopters. Then, as with any new tech, it spread to the mainstream. But, there are always the old guard. The ones distrustful of change. Those with the most to lose if adoption fails somehow. The legal, medical, and financial sectors [...]
How to Add a Second Monitor to Your PC
We are a world of multi-taskers. At any given time, you might have more than 10 windows open on a single screen. Maybe it's time to give your eyes a little breathing room. Here's how from an article on PC World: Step 1 The first part is easy. Simply connect your second monitor to a [...]
Beware the Costs of “Free” POS Systems
Everyone loves to get a deal, especially when you're a business owner. Money you're not spending is money that goes back into your business. However, some deals are too good to be true. Always be wary of "free" as it's rarely true. For example, the true cost of "free wifi". Free POS systems come at [...]
Valuable, and True, Lessons Learned During an Office Relocation
Moving offices can be a daunting, but energizing, undertaking. Planning is an integral part of success, as is hiring vendors that you trust to be there for you before, during, and after the move. During the transition, there are plenty of "wish we had done X earlier" moments that are realized too late. I recently [...]
Ready for a New Location? Set These Goals for a Successful Move.
Is 2017 the year you admitted you may need a bigger office? It's easy to ignore how tight or ill-fitting your current space is when faced with the daunting task of office relocation. Moving can be full of unseen expenses and headaches. But, it can also be vital to the health of your profit to [...]
Managed IT Service Trends We Expect in 2018
While there is no crystal ball we can find that can accurately predict the future, we've learned enough in 2017 to know what we can expect in 2018. Here we review some trends and issues we expect to arise for businesses and their Managed IT Service Providers. Cyber Attack Battlefront Moves to the SMBs The [...]
Is BYOD a Threat to Your I.T. Security?
Bring Your Own Device (BYOD) is jokingly referred to in some IT circles as “Bring Your Own Disaster”. While it offers a great opportunity to reduce costs and make employees happy, it’s still crucial to protect your organization’s data. GROWING IN POPULARITY BYOD had its genesis probably about 10 years ago with the advent of [...]
How to Get Back to the Core Strength of Your Business in 2018
You got into business to do a specific thing, but there are so many other tasks that go along with operations, it's easy to get dragged off course - IT management is a big one. Answer these questions about the last year: Did you experience downtime or data loss? Did you spend time tinkering with [...]
Holiday Travel Tip for Workers on the Go: Protect Your Data
Whether you're traveling for business or pleasure, it's likely you're logging in for work while on the move. Whether it's on your smartphone or laptop, you need to be extra cautious with your internet access during the holidays. Hackers know there are terminals full to the brim with potential targets. Don't be one of them [...]
5 Ways IT Managed Services Benefit Your Business
As a Managed Services Provider, we are clearly a little biased when it comes to IT outsourcing. We know we can help alleviate the stress and burden that IT management can create for business owners. But, in case you need a more convincing argument, we're sharing these five benefits from Tech Guru Daily. 1. Easier [...]
The Latest & Greatest in WiFi Routers for Your Home
Whether you’re dealing with slow speeds or WiFi dead zones, a new router can improve your internet experience. Reviews.com spoke with networking experts and WiFi geeks to get to the root of what matters.Their top picks come with the latest protocols and recommended frequencies, have been independently tested for speed and range, and boast a [...]
Heard of Fog Computing? You Will.
We've talked a lot about cloud computing in the past couple of years. It continues to become more prevalent in our daily lives. But, there's a new term being added to the mix when it comes to the cloud, "fog computing". Here's a quick run down of just what that term means. Where the cloud [...]
7 Reasons to Outsource Your IT and 3 Potential Risks
As a business owner, you've certainly considered outsourcing some of your business functions because you simply don't have bandwidth to handle them all. This is a simple call for things like accounting and contracts. But, your IT management can always be a little intimidating to release control over. Here are seven reasons you should consider [...]
Cloud Computing’s Most Important Benefit
There are many benefits that come with operating in the cloud - increased uptime, automated backup, automatically updated software - to name a few. But, the most important one is the hardest to actually quantify. Cloud computing's biggest boon to your business is productivity. It's the streamlining of your communications and data flow. Here are [...]
5 Characteristics of Best-in-Class IT Support
Smart SMB owners are learning a valuable lesson that is leading to increased productivity and cost savings. It is simply this - do what you have expertise doing, and allow others to do the same. You hire an accountant for your taxes. You hire an attorney for your contracts. Doesn't it make sense then to [...]
Evaluate Efficiency when Making Plans for 2018
We're almost to the halfway mark in the fourth quarter of our business year. This is a great time to assess your business operations and make plans for the upcoming year. Here are some tips on how you can become more efficient in the new year. Identifying wasteful or inefficient processes is a great place [...]
5 Must-Dos for an Easier Office Relocation
While reasons for office relocation can be exciting, the actual moving can be a major headache. But, there are plenty of ways you can make the whole process a little smoother. Here are five simple tips to help. 1. Label everything. Every box needs a label that outlines the contents and where it should go […]
Step One in Gaining Control of Your Print Expenses
You’ve identified that you are potentially pouring money down the drain when it comes to your printing, be it documents, labels, or any other ink to paper medium. You can’t just tell everyone to reduce what they print. You need a plan. Here is step one. Assess Your Current Print Environment. From BizTechMagazine.com: The first […]
The Seamless Future of Mobile POS Systems
There have been plenty of blockbuster movies that have shown us what the future of retail shopping could look like. In the Minority Report, eye scanners identified customers walking through the door and projected holograms of sales catered to the shopper. In Wall-E, shoppers never have to leave their hover chairs as they simply request [...]
Outsourcing Your Printing Makes Smart Business Sense
If your business is reliant on printers, for documents, labels, blueprints, or anything else, you know how much time and money can be wasted on print. You can potentially benefit from Managed Print Services (MPS). These services include a wide range of activity and supply management that can save you money. Here we make the [...]
How to Determine the Lifespan of Your Server
When you buy a car, you have a number in your head of the miles you expect to get out of it before the parts start to fail. You use that number to weigh the price of the vehicle. When investing in server equipment, you may be tempted to try a similar tact, replacing miles [...]
Create a Culture of Security in Your Office
Even with the most robust security measures available, one uninformed employee can open the door to catastrophic data loss with the click of a mouse. In our current threat environment, you need more than strong software, you need smart practices and trained people. Creating a culture that values data security in all aspects of your [...]
Choosing the Best POS System for Your Business
There are no shortage of options when it comes to Point-of-Sale systems, which is good because every business has its own needs. While there are many differences, there are some commonalities that any user should expect in today's market. We'll outline the features you should demand as well as share some top picks based on [...]
The Latest News in Ransomware
Ransomware is a hot topic these days. We're seeing it in the headlines far more than we'd like. The trick about digital attacks like this, and most malware attacks in general, is the ever-changing nature of them. The ransomware attacks we saw a year ago aren't the same as they are today. Here's an update [...]
Cyber Security Awareness Month: 7 Simple Steps to keep You Cyber Safe
Hooray! October is here and that means it's National Cyber Security Awareness Month. You may not be as excited as us, but you should still do your part and be aware of how you interact online. The more interconnected we become online, the more windows of opportunity created for cybercriminals. So let's do our part [...]
Hackers Build Backdoor into CCleaner App
A new hack has been announced and it's affecting over 2 million users. The infected application is called CCleaner and it's one that even we have mentioned in the past because it's free and works well to run file clean up to remove clutter from your hard drive. But, as with so many other breaches, [...]
The Why, What, When, & Who of Preventative Maintenance
We are all guilty of losing track of the last time we cleaned our printer jets or dusted our PC fans. Preventative maintenance is one of those tasks that quickly gets lost in the shuffle. When we get a new piece of hardware, we vow this time will be different, but it never is. Preventative [...]
The Obvious and Unseen Savings of Managed Print
If you leave kids alone in a kitchen to make themselves dinner, there is likely to be some unexpected use of food and utensils and plenty of unnecessary waste. When it comes to printing, if left unsupervised, your staff will do the exact same. It's easy to be wasteful when it's not you footing the bill, which [...]
Why the Manufacturing Industry Wins with Managed Services
Manufacturing operations rely on IT for just about everything. When you have machines doing your work, you rely on other machines to control them. IT is part of production, logisitics, supply chain, customer interaction, and more. If it's a large organization, as manufacturing companies tend to be, there will likely be multiple locations as well [...]
What to Do in the Wake of the Equifax Security Breach
The Equifax breach is a big one. The company holds the credit reports of over 143 million US consumers, and those reports have all our most valuable information. They are suggesting that you should not wait to determine if your information was breached to take action to prevent identity fraud. You should start with the [...]
5 Tips on How to Choose a Managed Print Provider
You give your business the most value by sticking with your core competencies. Eliminating some of the other business functions through outsourcing can be a great way to free up your schedule to focus on the important parts. One commonly identified bottleneck in any business owner's day is dealing with print-related issues. But, how do [...]
How to Make More Money While Doing Less
We've certainly got your attention with that headline, right? Too good to be true? Not at all. Entrepreneurs are known for having great ideas, but they are equally notorious for thinking they can do it all. Many SMB owners are the first to admit that they "wear many hats". They tend to hold the reigns, from [...]
Data Security Warning: Hurricanes Bring Out the Scammers
In the wake of Hurricane Harvey, and with the predictions for Irma, we want to remind our readers to keep vigilant about protecting their data. Hackers use the confusion and swell of donation requests as a window of opportunity to send phishing emails. Want to learn how to protect yourself from these attacks? Read our blog [...]
Lenovo Innovations Making Sci-Fi a Reality – An Augmented Reality
Lenovo makes computing equipment that is best-in-class. That’s why we are a certified supplier of their hardware. The Lenovo brand has the industries lowest failure rates, the best end-user experience, and a commitment to cutting edge technology and innovation. The latest out of Lenovo, using Augmented Reality (AR), may not be useful for your business, but it […]
Ransomware: A HIPAA Compliance Nightmare
We've written a lot about ransomware in the last year. It's a serious data security risk and can cause complete data loss, even if you pay the ransom. Dealing with any data loss takes a toll on a business in terms of customer trust, downtime, lost revenue, and security. But, combine that loss with personal [...]
HIPAA and the CLOUD
If you’re in the healthcare industry and thinking about the pros and cons of switching over to the cloud, then one of your top concerns is following HIPAA regulation, or ensuring the confidentiality of your patient information. So the question becomes: is it more secure switching to the cloud? This depends on a number of [...]
Free Your PC from Malware with These Simple Steps
Malware is a major problem these days. It just takes one click on the wrong link or email and your PC is infected with a virus, spyware, or even ransomware. The tricky part lies in the fact that these infections may sit undetected in your machine for over three months. Maybe you've noticed some funnky [...]
5 Things You Should Do to Your Laptop Once a Month
We have it easy. We carry supercomputers in our pockets and data processing powerhouses in our shoulder bags. We are no longer tethered to a desk, or an internet cable, or even a power cord. Our freedom has made us more productive, but too often we neglect the basic maintenance these high-powered machines need to [...]
Forget Everything You Know about “Strong” Passwords
How many passwords would you guess you have? In 2007, the average was 17. It's estimated that by 2020 we will have 207 unique logins... each!* As cybersecurity continues to be a growing concern, more password rules have been created. But, one of the men responsible for all those rules is telling us he was [...]
Top Criteria for Choosing an IT Managed Service Provider
Trust is hard, especially when it comes to business because everyone has their own skin in the game. Choosing to outsource functions of your business is never a decision to take lightly. You are granting access to an outsider under the assumption they will protect your interests as well as you would yourself. Some of [...]
The Upside of Office Moves
Office moves are a real glass half empty situation most of the time. There are plenty of articles on how hard relocating your offices can be. It certainly isn't a picnic, but it's not all schlepping and headaches. Here are a few ways to see your move as a glass half full. A Chance to [...]
Lenovo Included in Gartner’s Top 25 Supply Chain Leaders
As a licensed supplier of Lenovo IT hardware, we are always proud when they receive an award. This year they climbed from the 25 spot to the 24th in the Gartner Supply Chain Leaders. We support the Lenovo brand because it has the industries lowest failure rates, the best end user experience, and their commitment […]
A Modern Office and the Integration of the Cloud
Business IT is more interconnected than ever and it's certainly a boon to our productivity. We have talked about the many ways you can use the cloud to grow your business, but it's mostly been in reference to your computing power and data processing. There are several ways a business can integrate the cloud from [...]
5 Ways a POS System Can Enable You to Work Smarter
Retailers have it tough. They need to be open when customers aren't at work and that means weekends, nights, and holidays. They need to manage schedules, monitor inventory, analyze sales, and simultaneously meet and exceed the expectations of the customer. If they want any type of personal life, they need to do all these tasks [...]
6 Biggest Concerns of IT Experts Today
Security is one of the biggest issues IT professionals deal with. Regardless of how perfectly constructed your network architecture is, if your security is weak, it's all for naught. With all of the headlines about ransomware and major breaches, cybersecurity is certainly at the top of the list, but it's not our only concern. According [...]
Invasion of the IoT: Your Kid’s Toys Can Spy On You
The Internet of Things is intended to make life easier by getting all of our devices interacting and working as a team. Our devices even collect data to learn our preferences so they can better suit our needs. It's a wonderful, magical symbiotic interaction in a perfect world environment. But our world isn't perfect and [...]
Restaurant POS Terminal Business Continues to Boom Globally
Restaurant Point-of-Sale (POS) Systems are no longer the simple registers of days old. The new systems integrate mobile devices, assist with inventory and staff management, and operate in the cloud. McDonald's is even introducing a POS with a customer facing interface allowing customers to input their own orders. With the new trend towards quick service [...]
Move Over Ransomware, Wiperware Is Coming to Town
We've talked a lot about ransomware this year. The WannaCry attack was certainly the most notable, recently. Ransomware is a nasty piece of code that takes your system hostage until you pay the hacker whatever they demand. Then, most people assume, you get the pass key and regain control. However, it's often advised to not [...]
5 Principles of Protection for Your SMB
Small to Mid-Sized Businesses (SMBs) are natural targets for the criminally minded. SMBs have limited resources and are more likely to have gaps in their security because there just aren't enough funds to spread around. The flip side of that issue, though, is that these smaller operations often represent the entirety of the owner's assets, [...]
Digital Forensics Finds Criminal Evidence in Auto-Correct
We live in a world where almost everything we do leaves a digital footprint. We use our phones to help us find where we're going, pick a restaurant for dinner, find a doctor, read the news, shop online, and a million other things. Then we tell our friends about those things via text, email, and [...]
Ransomware Attacks on Hospitals becoming an Epidemic
Ransomware is not a new thing. The first newsworthy attack occured almost 30 years ago, shockingly. So why is it making headlines now? The greatest strength of hackers is their ability to evolve. Every time we figure out how to prevent a data breach, they come up with a new twist on an old scam. [...]
Hubs and Switches and Routers – Oh My!
The world of office IT can be a scary and intimidating one if you don't understand the terminology. There is no shortage of complex machinery involved in the simple act of connecting people to the internet and to each other. But don't be overwhelmed! Here's a simple explanation of what each is and what functions [...]
The Single Most Effective Deterrent to Ransomware
Are you tired of hearing the warning bells about ransomware yet? It's in the headlines everyday, it seems. But, this isn't just some internet hoax or overinflated issue gabbed about for the sake of news. It's a legitimate and growing problem that is proliferating, despite the fact that internet and email users should know better [...]
FBI Urges Businesses to Be Vigilant Against Cyber Threats
Ransomware and cybersecurity are big news right now, and not without cause. There have been several major breaches in the last few months that have set everyone on edge, and there's zero likelihood we've seen the worst of it. In response, major agencies are publishing articles to help educate businesses and citizens on what to [...]
How to Choose an Online Backup and Recovery Solution
Your company's data is your most valuable asset, and it is in constant peril. Whether the threat comes from malware or a negliglent employee, the resulting impact of data loss is the same: lost information, lost time, lost money, and lost customers. There are many ways to protect your data, but the most effective one [...]
Is Your Open Office Setup Hurting Your Productivity?
As the 90's ended and the internet (and tech startups) exploded, the limitations of the cubicle-filled office were decidedly outdated. The walls came down and the age of "open space" work environments was born. No more walls to separate us, no more doors to keep us out, now simply a community of employees working together, [...]
The 3 Most Common Plotter Problems
Plotters are complex pieces of machinery used for complicated jobs. The more complex a machine is, the more likely that issues will arise. While there are many models of plotters available, most wide-format printers run into the same main issues. Most require an expert to address, but some you may be able to take on [...]
Thermal Printer Maintenance Tips You Can Use
Thermal /TTR Printers are leading the growth of print in areas such as manufacturing, distribution, and retail sectors, mainly for labels, barcodes, and tags of all types. The healthcare industry, an industry that will only continue to grow as populations increase and people are living longer, have also found that thermal printers are a great [...]
Helpful Tips for Setting Up a Small Office Network
Whether you're starting a new business, or your current one is in a growth period, a well-constructed office network is going to be a boon to your productivity. Your computer network needs to be built with your particular requirements in mind. There isn't a great one-size-fits-all solution. Best practices for SMB network setup say you [...]
Affordable & Effective Data Backup Options for SMBs
In business, your data is just as valuable as your income. In small to medium-sized businesses, this is just as true for you as big business, if not more so. Customers are trusting you over larger operations that have more resources. But, just because you don't have a huge budget, doesn't mean you need to [...]
5 Tips for Buying Your Next Laser Printer
Buying office equipment is never fun or glamorous. But, it's an investment that needs careful consideration nonetheless. While electronic documents and email have greatly reduced the need for physical printers, they are still a necessary piece of hardware for most office environments. There are many options available in the laser printer category and you need [...]
3 Simple Reasons SMBs Need MSPs
Small-to-Mid-Sized Businesses (SMBs) are like the little engine that could. While they may be outgunned in terms of financial resources compared to larger competitors, they keep chugging along and making it work. SMB owners are, more often than not, jacks of all trades. If they want something done in their operation, they do it. That's [...]
FTC Publishes New Resource to Help SMBs with Cybersecurity
We're seeing increasing reports of data breaches on businesses of all size. Big businesses can afford to hire their own IT security professionals and dedicate resources to prevention, detection, and remediation. But, according to the National Small Business Association, more than half of SMBs are victims of cyber attacks. The Federal Trade Commission is seeing [...]
Outdated Windows Platforms at Risk for “WeCry” Ransomware
Last Friday, yet another large scale cyber attack made headlines. Known as "WeCry", "WannaCrypt", "WeCrypt0r", or "WannaCrypt0r", this latest attack was aimed primarily at enterprises, not the general public (like the Google Docs phishing attack a few weeks ago). How did the attack occur so quickly and what can be done to prevent it from [...]
VPNs – Are They the Natural Next Step in Cybersecurity?
Since the beginning of time, humans have sought out new ways to make their lives easier. Early man invented simple tools to help him survive. Modern man invented the internet. It is arguably one of the most useful tools ever created because it can be used for practically every aspect of our lives and we [...]
Death, Taxes, & Data Breaches? How to Manage Cybersecurity Risk.
There used to be two certainties in life: death and taxes. We think it's time to update the saying and include cybersecurity breaches. While computers and the internet have undoubtedly improved our productivity, they have also made us more vulnerable to data theft. Here are some suggestions on how to best mitigate those risks. AntiVirus [...]
Cybersecurity News: Google Doc Phishing Issue Follow Up
Yesterday was a bad day for some Google users. News spread quickly about a phishing attack within the Google system. Estimates now say only 0.1% of users were affected. But, at a billion users, that still equates to a million people that had their data security violated. Phishing attacks are nothing new, why is this [...]
May the Fourth Protect You – It’s World Password Day
The 4th of May has been celebrated by Star Wars geeks for several decades. When spoken, the date bears a strong resemblance to the saying, "May the Force be with you." This year, there's another holiday worth geeky celebration occuring on the same date - World Password Day. Cybersecurity is a global issue. One of [...]
What Is Cyber Liability Insurance? Do I Need It?
Cyber Liability Insurance is a service more and more insurers are offering, but is it just a waste of money? The word insurance makes people cringe. It presents the age old dilemma: Are you risk averse enough to pay for something you’re not sure you’ll ever actually need? Is it a scam? Or is it [...]
HIPAA Breach Leads to $400,000 Settlement
In the 2017 Experian Data Breach Industry Forecast*, healthcare is highlighted as one of the top 5 data breach trends for 2017. “Healthcare organizations will be the most targeted sector with new, sophisticated attacks emerging.” They emphasize the need to act: “Healthcare organizations of all sizes and types need to ensure they have proper, up to [...]
Earth Day 2017: Sustainability Tips for the Workplace
In honor of Earth Day, we'd like to share some tips on how to ensure your workplace is operating in an eco-friendly and sustainable way. We've taken a few of our favorite tips from our blog posts and the web and compiled them here for you. Use the "hibernate" feature on all PCs and turn [...]
Top 5 Questions About EMV Chip Cards Answered
EMV use in the US has finally taken over. We are behind many countries in adoption, but we're getting close to catching up. Almost every POS system now has a chip reader, although they aren't all functional yet. There has been a huge merchant and customer learning curve, but we're getting the hang of it. [...]
Fake Emails to Ignore to Protect Your Cybersecurity
Hackers can be very clever, there's no doubt. They prey on uninformed email and internet users in the hopes of getting their malware into your network. Savvy users can spot the majority of spam emails and pop-ups pretty easily. But, sometimes we all get tricked. Here is a sample of the most recent email scams we've [...]
4 Key Benefits of Remote Server Monitoring
As your business grows, it becomes harder to stay involved and active in every aspect of your operations. The functions that generate the most income will get the most attention. Unfortunately, if you neglect to monitor certain aspects of your business, like your server and network performance, they can fail unexpectedly and drain that income. Remote [...]
An Easter Malware Warning from Homeland Security
The United States Computer Emergency Readiness Team (US-CERT), a division of Homeland Security, published an important warning this morning regarding the upcoming holiday weekend and cybersecurity: As the Easter holiday approaches, US-CERT reminds users to stay aware of holiday scams and cyber campaigns, which may include: unsolicited shipping notifications that may actually be scams by [...]
EMV Adoption Leads to Surge in E-Commerce Fraud
EMV chip cards and readers were only introduced in the US in October of 2015. Yet, you already have chip cards in your wallet and use them daily. You also know, all too well, the growing pains associated with introducing this new POS technology. It has been plagued by slow processing and a slow learning [...]
The Key to Preventing Costly Network Downtime
The phrase "downtime" should bring one image to mind: a pile of money burning to ash. That's what network downtime does to your profits, destroys them. It's difficult to fully grasp the total cost of downtime because it's so muliti-faceted. In 2015, downtime was estimated to cost US businesses $700 Billion, that's with a B. [...]
The Ups and Downs of Contract Maintenance Agreements
If you run an office, school, lab or any other establishment that requires a sizable number of servers, computers and printers, you might be wondering about the best way to keep your equipment running smoothly for as long as possible. That equipment is no small investment! The two standard options are to sign a contract maintenance […]
6 Essential Server Maintenance Tips You Can’t Ignore
If you’re executing a good deal of programs from your server instead of the cloud, you’re going to have to provide extensive regular maintenance for your server. Even if you don’t have to use your server much, it’s still wise to provide consistent maintenance and oversight to keep it operating smoothly. A preventative approach always [...]
It’s Your Fault That Employees Are Largest Data Security Threat
Security breaches are becoming more of a promise than a threat. It is not a matter of if, it's a matter of when. According to the Identity Theft Resource report, there have already been 300+ breaches that involved a total of over 1.3 million records in 2017. Last year they reported 980 breaches, meaning we [...]
Do These BEFORE Getting Online with a New PC to Keep Data Secure
Getting a new PC or laptop is a blessing and a curse. It's a blessing in that you get a clean slate, a fresh start. None of the old junk cluttering up your shiny new hard drive. It works at its absolute best. The curse comes when you realize nothing is set up the way [...]
What Are Managed Print Services and Why Do I Need Them?
The business owner is notorious for being a "jack of all trades". When you decide to start a business, you may not feel comfortable outsourcing tasks that you can handle yourself. But, as business grows, demands on the owner grow as well. It starts to become necessary to hand off some of the everyday maintenance [...]
The High Cost of Mobility: Why Laptop Repair Costs More
It has been proven again and again, enabling a mobile workforce can be a boom to the success of all types of businesses. Business owners see increased productivity, efficiency, and employee satisfaction (and thus higher retention). All of these add up to cost savings. However, the lifeblood of a mobile workforce is the laptop and the [...]
4 Best Practices for Server Documentation
Servers are complex pieces of machinery that very few people in a business generally understand. Because of this, it's critical to have thorough server documentation in the event of an emergency. If a problem occurs with your server, you want to be able to act quickly and a well-organized manual is critical to reducing recovery [...]
Staff Must Be Included In HIPAA Risk Assessment, Not Just EHR
With the proliferation of mobile and cloud computing, data security threats are a constant state of things, especially in health care. Cloud storage of electronic health records (EHR) has helped to improve quality and efficiency of care by allowing all of your doctors and specialists to seamlessly access your records and medical history. It has [...]
Does Cloud Computing Violate HIPAA Compliance?
Every day more businesses are shifting some or all of their operations to the cloud, but what if your business requires HIPAA (Health Insurance Portability and Accountability Act ) compliance? Is using a cloud service provider (CSP) off the table for you because you're now transmitting data outside your walls? The U.S. Department of Health & [...]
[Infographic] The Beastly IT Security Threats – A MUST READ
Data and IT Security are at the forefront of everyone's concerns these days. The news is overrun with headlines about breaches of corporations that you'd imagine would have tremendous security measures in place, but still fall victim to cyberattack. Then there are the cautionary tales of identity theft you hear from friends and co-workers. We need [...]
5 Keys for DIY SMB Server Room Setup Success
With all the network security threats and potential government monitoring discussed in the news today, some business owners may prefer to take on their own computing management. Whether you have a small in-house IT staff or you alone represent the entirety of your IT team, setting up a server room is no easy task. Here [...]
Don’t Just Pitch Your Old Computer, Protect Your Data Security
There is a never ending, revolving door of new technology these days. In with the new and out with the old happens a lot quicker than it used to when it comes to IT hardware. When you get a new PC, do you just throw the old one in the trash? Absolutely not. It's bad for [...]
How Do You Know if the Cloud is Right for You?
Let's begin with this false statement, "Moving your IT functions to the cloud may not be right for you." I say it's false because moving to the cloud is inevitable. But, by adding one little word, we can make this statement true. "Moving your IT functions to the cloud may not be right for you, yet." Fail to [...]
4 Reasons You Need Managed IT Services in 2017
Maybe you've overlooked managed services in the past because you weren't ready... ready to pay someone to do what you felt you could... ready to outsource control of critical business functions... ready to trust anyone other than yourself to protect your business. But, now that you're running full-steam ahead with your 2017 plans, you realize [...]
Make the Most of Your Shadow… Shadow IT That Is
Today, shadows are very front of mind. Unfortunately, Punxsutawney Phil saw his, meaning six more weeks of winter. But there's another shadow that we'll be seeing a lot more of in 2017... Shadow IT. Shadow IT refers to IT systems and solutions that are managed outside of the IT department in an enterprise, and often [...]
Is Your Data Security Budget a Waste of Money?
When you look at your total IT budget, how much is dedicated to data security? Have you increased that budget in the last couple of years? Most companies have in response to the growing number of cybersecurity threats that have cropped up in the last few years. More threats should be fought - and won [...]
Data Security Tip: January 28th is National Data Privacy Day
In a very interconnected world, it's imperative that we remember to safeguard our data security. The National Cyber Security Alliance (NCSA), the organization that heads Cyber Security Awareness month each October, has been leading an effort to raise awareness to this issue since 2011, but the history of it goes back to 1981. Data Privacy Day [...]
5 Reasons You Need Contract Maintenance for Your Hardware
When we buy new electronics, we're faced with the decision: Do I buy the extended warranty or insurance plan? Plenty of people immediately think, "This is where they're trying to trick me." I get it. That extra expense wasn't what you intended to pay out of the gate. And it's possible you'll never need it, and [...]
Tips on Telling Your Clients You’re Moving Your Office
Making the decision to move your company is the first step in a very long and complicated process. It takes careful planning and organization to eliminate downtime and minimize impact on your business operations. Any time you are closed, you are losing money, and no one wants to do that! One of the crucial tasks […]
Ransomware: To Pay or Not To Pay?
We've talked a lot about ransomware in the last year. Frankly, the whole world has been talking about it as it becomes one of the leading global cybersecurity threats. The biggest problem with this type of malware is the urgency it creates. Because of an impending threat of data loss and being locked out of [...]
Digital Forensics Is the New Cybersecurity CSI
You've certainly heard the term 'cybersecurity' plenty in the last year. Between the high profile cyber attacks on big box retailers to the newsworthy ransomware attacks on hospitals, if you haven't heard it, you must be intentionally living off the grid, and we don't blame you. Getting in front of cybersecurity issues is front of [...]
Stay On Point with Proper Point-of-Sale System Maintenance
All types of businesses use Point-of-Sale systems, but each uses them a little differently. Where an automotive repair shop may just have a single, fixed terminal, a popular restaurant may have several fixed terminals as well as a series of handheld units that are constantly on the move. No matter what type of system you [...]
Cybersecurity Tip: Voice-Activated Smart Hubs Are Listening
Did you get an Amazon Echo or Google Home for Christmas? They may be really nifty gadgets that make hands-free operation fun, but they're listening to more than just your music requests. These devices have become increasingly popular for their ability to make to-do lists, play music, turn electric appliances on and off, and provide [...]
Is 2017 the Year to Replace Your Server?
Every IT Manager will need to face this costly decision at some point in their careers. Some see the warning signs and put in the due diligence to research their options. Some see the warning signs but wait to take action until there is a critical failure. Some are blind-sided and have to act on [...]
New Year’s Resolution: Grow Your Business with Managed Services
As we get ready to enter 2017, we think ahead to our plans for the new year. If you're a business owner, you are hoping and planning for growth. But how do you find time to focus on the where, when, why and how to get that growth happening? You need to free up some [...]
Prevent Laser Printer Jams With These 5 Tips
Paper jams can bring your productivity to a screeching halt. By taking some simple steps, you can significantly reduce the number of laser printer paper jams you experience on a regular basis. Depending on the printer, you might even go years at a time without having to fight another paper jam while processing print jobs. Use [...]
Malware Alert: Mobile Banking Trojan on Android Phones
Every day new cybersecurity threats are being found. Most recently, there's been an uptick in malware related to mobile banking. The trojan program clones your mobile banking login page and collects your login information when you enter it. And the newest variant includes a ransomware package that will then lock you out of your data as [...]
7 Reasons Managers Love Managed Print
Managed Services are becoming more prolific than ever. Smart business people understand that they are the most successful when they can focus on their strengths and leave the administrative work to others. The market is responding and we are seeing a huge spike in enterprise-related managed services being offered for every business function. This is [...]
Online Shoppers Beware of Malware in Fake Delivery Notifications
Online shopping is a great gift to those who prefer to skip the lines and the parking hunt, or even the need to leave home. We can get all of our holiday gifts from our smartphones. While it's great for shoppers, it's great for hackers too. They are constantly looking for new ways to get into [...]
Malware Tip: Protecting Yourself from Phishing Hacks
Phishing is one of the most prevalent cyber attacks currently. Phishing scams are generally fake email messages appearing to come from legitimate companies, like utility companies, a bank, or the IRS. They direct you to a fake website or ask for personal information, especially account related info. Phishing attacks tend to be panic-inducing in tone to catch [...]
POS Systems are Experiencing an Evolution in 2017
We've seen some major changes in the last couple of years to how consumers can pay for goods or services. We have moved to a credit-based society as less and less cash exchanges hands. Historically, we've used a credit card magnetic swipe to transmit payments. As a result of security breaches, we've moved to the [...]
5 Ransomware Stats That Will Scare You
We've talked about ransomware a lot in 2016. It's a growing, ever-evolving threat to your data security that you may not be paying enough attention to. Preventing this form of cybercrime takes a combination of robust security, in-depth education of staff, and thorough back up. If you need more convincing that it's a threat you [...]
Are You Still Afraid of the Cloud? It’s Time to Get Over It.
In the beginning of any major technology introduction, there are always plenty of hiccups. The first on board, the early adopters, tend to help weed out the kinks. As the mass market adopts the technology, they feel a greater comfort that there will be less bumps in the road. Cloud computing is proving to be an [...]
SMBs Struggle with Cyber Security During the Holidays
In retail environments, 4th quarter earnings can make or break you. Business owners focus on ensuring they have enough stock to cover the demand, without creating surplus inventory. But, are they taking stock of their cyber security measures too? A blogger from ITBusinessEdge doesn't think so. According to a study by IBM's Resilient and the Ponemon [...]
5 Common Laptop Problems and How to Repair Them
A huge chunk of the corporate world is mobile, and they need computing power that can accommodate that. Over the years laptops have gone from bulky and heavy to slim and lightweight. But, even with all the upgrades in power, size, capacity and memory, laptop problems still arise pretty regularly. Here is a quick list of five […]
Printer Problems After Windows 10 Upgrade? Let’s Fix It.
You finally made the switch to Windows 10. After the initial learning curve, you think you have a pretty good handle on it, then you try to print. Where is your printer? Why isn't it working? You're not the only one that's had this happen. Here are some troubleshooting tips to help get your printer [...]
Tech Tips to Reduce Energy Waste at the Office
Reducing energy waste in your office does not have to equate to a sacrifice in personal comfort or quality of workmanship. With the availability of cloud computing, many new options for minimizing energy consumption have opened up that will simultaneously increase the level of freedom enjoyed by team members. Minor changes translate into significant savings [...]
Top 5 Reasons SMBs are Hiring Managed Service Providers
The Managed Service industry is experiencing a major growth trend. More and more, SMBs are realizing that in order to stay competitive with the big guys, they may need to outsource some of their functions to experts, so they can focus on their own expertise. Here are 5 good reasons to consider Managed Services, from MSPblog: […]
Tech News: Microsoft Making It Easier to Get Windows 10 Updates
There are always bumps in the road when new operating systems launch. One of the biggest complaints about Windows 10 stems from trouble users are having with updates. They require too much processing, and thus eat up battery life and space on the hard drive; there is also no control on the timing of them. This could [...]
Insider Tips to Make Your Office Move Easy… Easier
Moving an office is a big job. Not only do you have to pack, move, and unpack all of of your furniture and equipment, but you have to do it fast enough to limit the downtime to your customers. Every minute you're not open, you're losing money. When preparing for an office move, you need [...]
3 Tips to Prevent Malware in Your POS System
We talk a lot about malware and protecting your computers and servers from intrusion. But, your Point-of-Sale systems are another window of weakness where cyber attacks can occur. We all remember the Target attack. More recently, Eddie Bauer found itself a victim as well. Think about it. POS Systems are ripe with valuable payment data [...]
8 Ways a Complete Cloud Solution Wins
Many businesses have already recognized the value of including cloud services within their IT setup, yet one of the newest developments in the world of hosted computing is the complete cloud solution. In this model, all servers, backups, updates and even PCs themselves are hosted on the cloud, freeing your company from the need to maintain [...]
Digital Ghosts Can Be a Nightmare For Data Security
As Halloween nears, we thought a ghost story would be a good idea. But, this isn't about Casper or ghosts in the traditional sense at all. This is a new kind of haunting, one that can linger long after death if not exorcised properly. But, before you run off to the nearest Holy Water supply, let me [...]
Why Law Firms Love Managed Print
Law firms are full of busy people who are heavily reliant on technology to accomplish their daily tasks. While laser printers, copy and fax machines and more are present in nearly every law office, most of these same offices lack a full-time printer technician or an IT specialist. This opens the door for potential downtime […]
Be Cyber Safe: October Is National Cyber Security Month
Since 2004, October has been observed as National Cyber Security Awareness Month (NCSAM) and was created in a collaborative manner between the U.S. government and industry in the hopes of increasing awareness regarding cyber security in general. Do you know how to protect your cyber security, and why it's important for everyone? President Obama has [...]
Ransomware Attacks Now Top Threat to Financial Industry
There have been plenty of reports of ransomware attacks over the last two years. It's clearly on the rise. New reports show that ransomware is now the top cyber security threat to the financial industry, which tends to be the most security conscience sector. Darknews tells us more with some alarming stats. Some 55% of [...]
US Gov’t Issues Malware Warning Tied to Hurricane Matthew
Weather isn't the only threat to fear in a hurricane. Cyber criminals are using the chaos and destruction following Hurricane Matthew to take advantage of unsuspecting web users using malware and phishing scams. The US Computer Emergency Readiness Team (US-CERT) issued a press release tuesday with six preventative measures to take. US-CERT warns users to remain [...]
Tips to Keep Your Thermal Printers Up & Running
Thermal printers are innovative, technological products that can provide amazing benefits for many businesses. Some companies rely heavily on their use, and extended downtime due to maintenance issues can prove very costly. In order to get the most out of your thermal printer and keep it in optimal condition for as long as possible, there [...]
Easier Office Moves: Tips for Relocating Office Technology
Planning for office moves involves much more than just calling a moving truck to haul out the furniture and desks. Relocating office technology includes moving computers and servers and is perhaps one of the most critical aspects of shifting locations, as your company is almost certainly dependent on technology. Minimizing downtime is the key to […]
Tech Tips: [Infographic] Tips & Tricks for Windows 10
At Great Lakes Computer Corporation, we want our customers to feel like they are getting the most out of their computers, printers, servers, and other office technology. In that spirit, we created this quick guide for new Windows 10 users, to help readers understand all the new platform offers. We also provide some quick tech [...]
5 Must Have Features of a Managed Service Provider
You’ve thought about the benefits of IT outsourcing and believe that it could be an excellent way to save money and help your business run smoothly. Great! However, did you realize that not every MSP (managed service provider) is alike? We’ve put together five must-have features of a managed provider to help you determine if [...]
GLC Announces New Partnership with Backup and Recovery Experts
News Release September 27, 2016 TITAN DATA SERVICES AND GREAT LAKES COMPUTER CORPORATION ANNOUNCE PARTNERSHIP TO DELIVER BEST-IN-CLASS IT SERVICES Firms Look to Deliver Unmatched, Comprehensive Managed, Backup, and Restore Services to Ohio Clients Cleveland, OH – Today Titan Data Services and Great Lakes Computer Corporation announced a strategic partnership. The arrangement capitalizes on […]
Printer Problems: HP Firmware Update Rejects Third-Party Ink
Printing can be costly. There have been theories that printer manufacturers don't utilize the full ink tank, and cause you to replace your ink prematurely. From this, stemmed a new business, ink cartridge production and refilling. People willing to risk using non-branded ink cartridges have been doing so for years, much to the printer companies [...]
Data Backup and Recovery Best Practices for SMBs
The amount of digital data that small and medium-sized businesses must process and store continues to increase exponentially, and the need for proper backup and recovery procedures is more pronounced than ever. In order to avoid expensive downtime and ruinous data loss in the event of an emergency, take some time to review your data […]
Tired of Juggling? More Businesses Shift to Managed Services
'Managed Services' as a term is often confused with the much aligned term 'outsourcing'. We're not talking about shifting your operations overseas just to cut costs or firing your trained, in-house staff for cheap labor. We're talking about hiring a specialist to help manage the many moving pieces of your IT infrastructure so you can [...]
Smartphone Malware Infections Rapidly Rising – Protect Your Network
You've heard about the Bring-Your-Own-Device (BYOD) revolution in the work place. It certainly has its benefits. We are on our smartphones at home and at work and use them everywhere else we go. It makes life so easy! All of our work and our play all in the palm of our hands. But there's major trouble [...]
Google Amps Up Internet Security For Everyone
There are lots of ways that hackers can get to you. They can find you on public wifi, access data through your smartphones, and send you infected emails. But the easiest route they can take is the internet, via simple web surfing. With one click of a mouse, you can end up on an infected [...]
EMV Everywhere: All About the Chip Card Revolution
All of the major credit card schemes and card issuing banks have been transitioning to payment by chip card, also known as EMV. It's an older but highly secure technology that is almost impossible to hack. The move to this type of credit card is in direct response to major database hacks of retailers and [...]
3 Ways Dear Aunt Sally is a Potential Data Security Victim
Most of our readers are computer savvy. They know the basics of how their IT works and are mindful of cyber threats and data security risks. But, we all have that relative or friend who is a late adopter of computers, networks, smartphones and the internet. They may not really understand the risks they create [...]
5 Signs It’s Time to Consider IT Outsourcing
Many business leaders assume that by handling Information Technology (IT) management in-house and having greater control over the process, they’ll be able to minimize costs and inefficiencies. It’s actually a fallacy, and here are five signs you need to watch out for. 1. Your IT spending budget is unpredictable, and you need to get it [...]
4 Ways Server Monitoring Can Save You Money
Monitoring your company's server is critical to the smooth day-to-day operations of your business as well as maintaining satisfied clients. Unfortunately, some companies only casually observe daily issues involving the server, often allowing small, correctable problems to develop into major ones. Outsourcing server monitoring, which can be completed remotely with the help of advanced software [...]
Tips to Transfer Files from an Old PC to a New One
Your old computer is outdated and it's time to upgrade. You spend time researching the right machine and finally, you find just the right one. You open up the box and breathe in the scent of unused hard drives, empty caches, and perfect processing speed. But, new computers don't stay without baggage very long. All [...]
Working in the Cloud: The Pros and Cons of Office 365
Lots of people still don't really understand cloud computing as a term. Whether you think you understand the cloud or not, you are already using it - Google, Twitter, Facebook, DropBox - all cloud software. One of the biggest cloud apps is Office 365. Many companies are singing its praises for giving their teams tremendous mobility, [...]
Red Flags Warning You It’s Time For Server Maintenance
After years of providing server monitoring services, we learned to spot some common red flags. Some signs might seem subtle, but others are fairly obvious. If your business relies upon your company's computer server for daily work, you might want to pay attention to what your machines are telling you. Consider these common signs that [...]
5 Ways Managed Print Services Can Save You Money
Can you imagine how much smoother your business could run if you never had to worry about printer trouble or printing costs again? Managed Print Services (MPS) help manage every aspect of business printing, from using printers more efficiently to ensuring that machines get proactively serviced and supplied. Consider five ways that Managed Print Services [...]
Cloud Covered: A Quick Guide to Cloud Computing Models
IT experts have predicted cloud computing will impact over $1 Trillion in IT spending in the next 4 years. Leading up to this announcement, you've undoubtedly heard a lot about cloud applications and companies that move their entire IT infrastructure to the cloud. But it's important to understand people use terms like cloud and cloud [...]
4 Tips for POS System Maintenance
Many businesses are heavily dependent upon the performance of their POS system, which makes it paramount for them to take all possible steps to ensure that it is always operating in good condition. When POS systems fail due to misuse or malfunction it often results in frustrated customers leaving without a purchase, employee productivity plummeting, [...]
How To Defend Your Network Security from 5 Wi-Fi Attacks
Network Security is serious business. There are many ways intruders can get into your network. Strong passwords are a great place to start defending your network, but you need to take it to the next level. Here are five ways Wi-Fi attacks occur and how to prevent them from NetworkWorld. 1. Lost or stolen device [...]
5 Tips for a Smoother Office Move
You’ve been successful in business and your company is growing. But with growth comes expansion. Increases in staff and equipment can quickly turn your current office space from roomy to congested. Once you find a new office space, you are faced with the daunting task of relocation. Moving is never easy, and there are bound […]
Which Printer Is Right For You?: A Printer Primer.
Although sophisticated mobile technology and the development of the cloud have reduced the need for printers in many situations, most companies still need high-quality printers to power their core business processes. Printers still occupy an important place in the corporate world, and many of the new models are incorporating helpful new features that would have [...]
5 Must-Have Features of Antivirus Software
Since consumers and businesses first started connecting their computers to the internet decades ago, antivirus software has been one of the most important segments of the tech industry. It’s become so ubiquitous in fact, that many people assume all antivirus software offers a similar level of protection and features, and they don’t actually pay much [...]
Network Security Tip: 3 Reasons to Update Your Internet Browser
In our fast-paced technological world, updates are a necessary evil. They take up time, and sometimes they can change things we like, or change the way our apps work. Those can all lead to frustration. Does that mean we should just keep ignoring update requests? Absolutely not! Developers make these updates to improve performance and [...]
6 Ways to Drastically Reduce Your Printing Costs
Printing costs can take a surprisingly heavy toll on a business, but there is much that can be done to drastically reduce the overall expense. The following six ideas will help reduce your company's printing expenses dramatically by implementing some simple changes in your daily activities. Six Ideas to Slash Printing Costs Utilize draft quality [...]
Top 4 Ways Cloud Computing Is Greener Than You Think
There are lots of benefits that come with the switch to cloud computing - reduced costs, increased data redundancy, scalability, and mobility to name just a few. But there is an often overlooked ecological benefit as well. The positive environmental effects of using the cloud can be one more reason to make the switch. Here [...]
The Beauty & the Beast in the Internet of Things – Part 2: The Beast
The Internet of Things (IoT) might sound like another useless buzz word, but it's a very real concept that is becoming a bigger part of your life every day. The interconnectivity between a huge range of objects has the power to change our society for the better, but it also presents many risks from connected [...]
The Beauty & the Beast in the Internet of Things – Part 1: The Beauty
Something funny happened to the internet as we transitioned into the 21st century. It untethered itself from our desktops and laptops and found a home in everyday objects, where it began to revolutionize the capabilities of formerly disconnected devices. In Part 1 of our 2 Part blog, we tell you about the beauty created by [...]
5 Ways SMBs Can Use the Cloud
Do you think cloud computing is too high tech for your small to medium sized business? If so, you are wrong. Cloud computing is useful for businesses of all sizes. It can reduce your IT costs, improve your Disaster Recovery, and be scaled to fit your needs. Here are a few ways you might consider [...]
Data Security Warning: The True Cost Of Free WiFi
When you’re out and about and running up against your cellular data limit, there’s nothing quite as inviting as a sign indicating that free WiFi is available. In the age of ubiquitous broadband internet everyone is expected to be constantly connected for both personal and business communications, and public WiFi can be exceedingly convenient when […]
2 Fundamentals of Small Business Disaster Recovery
Small businesses need to prepare for disaster as much as big ones. It may be even more crucial because the statistics on small business survival after a disaster are daunting. Only 35% of small businesses have a Disaster Recovery Plan (DRP). 90% of small businesses fail within 2 years after experiencing a disaster. The experts […]
Virtual Currency: A Primer and Security Warning
Bitcoin is now so ubiquitous that you’ll frequently hear stories about the world’s most popular virtual currency on the local evening news. Bitcoin and other virtual currencies have exploded in popularity in recent years, yet many people still don’t know much about their foundations and are unaware of the dangers involved in using them. Virtual [...]
7 Security Mistakes You’re Making in the Cloud
People fear what they don't understand, and cloud computing is no exception. You may understand the general concept but don't really understand if you need it and if it's secure. But you are already using the cloud whether you realize it or not - Facebook, Gmail, Instagram, LinkedIn - all data stored in the cloud. [...]
8 Helpful Tips to Increase Data Security in the IoT
The Internet of Things (IoT) is a marvelous idea, conceptually. All our personal and work devices talking to each other to enhance data collection and exchange, to improve how they respond to our needs and make our lives more streamlined and more efficient. Companies are looking for any way they can get their new product [...]
Data Security Tip: Don’t Just Delete Spam, Teach It to Go Away
Spammers rely on catchy headlines and enticing offers to get users to click their emails. While not all spam messages contain malicious content, many do. Most email users are aware of the data security dangers of spam, but don't give it much thought. Our email clients can generally detect most of it and automatically sweep [...]
Tech Tip: Your Likes Could Be Giving the Thumbs Up to Malware
Facebook has created a currency of 'Likes.' They are given and received by the millions every day. Some users are stingy with their likes, some give them freely to every post they see. But, be wary of those viral posts requesting you to 'copy and share' or type 'Amen!' Not all likes or re-posts are [...]
8 Network Security Practices Your Staff Needs To Know
Almost every business now stores at least some of its data digitally, with many organizations attempting to move entirely to paperless record keeping. This is allowing businesses to be leaner and more thorough in their data management, but this proliferation of digital data is also very appealing to cybercriminals. You can purchase the best available [...]
Network Security Tip: Quit Changing Your Password!
Passwords are incredibly important, which is why almost EVERYTHING you access requires them. They are the first line of defense to your data. Best practices for password creation tell us to include a combination of lower and upper case letters, numbers, and special symbols, and the more random, the better. If you value your company's [...]
6 Trends in Cloud Computing You Need to Know
Companies are now realizing that adopting cloud technologies can benefit any type of organization: small or large, traditional or tech-savvy, new or established. As more and more businesses become familiar with cloud services, there is naturally going to be more curiosity about the industry. 2016 is already shaping up to be another eventful year for […]
IT Insider Tip: Beware the Windows 10 Upgrade
More times than not, we readily click "OK" on any Windows related pop up just to get rid of it. However, there's a new pop up to be wary of. Our Help Desk Experts have gotten several calls regarding issues related to this "update" and want us to spread the word. Below are the details [...]
The Multiple Manifestations of Malware
Not all malware is created equal, and the security of your data may rest on being able to recognize the various types that can infect your network. Some of this malicious code does little more than cloud the screen with popups, while other types can result in data theft and severe damage to the operating [...]
6 Easy Ways to Prevent POS Touch Screen Damage
Touch screens are quickly becoming the interface of choice. They take up less space. They're more intuitive. They speed up your work. But, they have one great weakness - humans. We're messy, impatient, and tend to use force when we're frustrated. Here are 6 tips from a Florida POS repair company to help keep your touch [...]
Broken Pipe Leads to GLC’s Own Disaster Recovery
At Great Lakes Computer, we agree with Ben Franklin when he said "If you fail to plan, then you are planning to fail." A thorough plan is the cornerstone of effective Disaster Recovery. We write about it in our blog all the time. We offer Disaster Recovery backup, replication, and recovery services. We believe in [...]
7 Server Maintenance Tips Crucial to Effective Operation
Servers form a crucial backbone of your company, allowing you to serve clients, store data and run your business seamlessly. In order to keep your server working well, you’ve got to forge a reliable routine that minimizes potential error and breakdown and routinizes crucial maintenance tasks. After all, prevention of common issues through a good [...]
5 Simple Solutions to Your Biggest Printer Problems
Printers can be a real pain. They often don't work quite how you'd expect and fixing them can seem daunting. Before your frustration overwhelms your better judgement, read these 5 common printer problems and how to fix them from PCRepair.com. Problem: Printing is too slow. Solution: Rev up printer performance--and save ink in the process--by [...]
Top 5 Ways to Extend the Life of Your POS System
Your point-of-sale (POS) system is crucial. When it’s working well, life is easy, but without it, business comes to a grinding halt, and you can’t even perform the simplest tasks. Don’t let that happen to you by allowing your POS to break down earlier than it’s supposed to. Here are 5 tips for extending its [...]
POS Repair Tips: 5 Helpful Hints to Keep You Up and Running
POS systems are the lifeblood of many businesses, but with finicky parts such as touchscreens and printer ribbons, they are also prone to malfunctions. Having to break out the manual credit card imprint machines is the bane of both your customers and your employees, but some simple steps can help you get the most out [...]
Medium Sized Businesses Targeted Due to Poor Network Security
Hackers, like the viruses they create, adapt at alarming rates. The newest adaptation involves a focus shift to medium sized businesses for cyber attacks. Big companies have the budget to install top line security measures and full IT staffs to oversee them. Medium sized businesses have a hard time keeping up, and that weakness is [...]
**Data Security Alert** PC Users Told to Uninstall Quicktime ASAP
The Department of Homeland Security issued a warning to all PC owners on April 14th; Uninstall Quicktime immediately. There are known vulnerablilities in the software, and Apple has discontinued updates for it. This leaves your PC at risk to hackers. Forbes.com tells us more of the story: This alert stems from a recent call to [...]
BYOD Policies Attract Younger Talent, But At What Cost?
Today's graduates aren't seeking out the classic 9 to 5 cubicle gig. They are looking for a flexible schedule with a greater focus on work-life balance, but they understand the price of that may be working at sporadic hours and on weekends. In order to attract this fresh talent, companies need to consider a fresh [...]
Big Telecom Providers Dropping SMBs – Tech Concierge to the Rescue
In the past year, several major telecommunication providers have decided that SMBs just don't generate enough money to keep as clients. In December of 2015, Windstream announced it would be phasing out all its SMB clients that generate less than $1,500 in monthly revenue. The customers would either have to pay a rate almost double [...]
10 Items Your Disaster Recovery Plan is Worthless Without
Your disaster recovery plan is a crucial aspect of business risk management. If you want to ensure you can maintain business continuity in the face of disaster, you need a good plan in place to help see you through the rough times. Here are 10 items your disaster recovery plan needs to have, or else […]
Top 5 Best Practices for Network Security
The web we create with the introduction of newer, better technology is a tangled one. In a business setting, we not only have internal servers, but we operate on the cloud as well. We have BYOD (Bring Your Own Device) work environments where our staff are using their mobile phones and personal devices to conduct [...]
Printer Maintenance Tip: Spring Clean Your Plotter
Laser plotters can be indispensable to the types of companies that use them. They can also be quite costly to purchase. This is why proper plotter and printer maintenance is crucial. No CIO wants to be in the position of constantly calling for plotter service, let alone facing the need to replace a unit long [...]
IT Forecast: Cloud Covered
It’s no secret that the growth of cloud computing has been one of the most significant stories in the tech world for several years now. At this point, even the people who would consider themselves the opposite of early adopters have at least heard of the cloud, and have some idea of how businesses are […]
Disaster Recovery Planning: Where to Start?
There’s often a great deal of cognitive dissonance on the part of business owners when it comes to disaster recovery. They think they don’t need to plan for an emergency because they doubt it will ever happen to them, despite the fact that serious data losses occur relatively frequently. Network emergencies can result in lost [...]
Second Hospital Network Security Breach by Ransomware in Just Two Months
Data Backup and Recovery Saved this Hospital from Paying the Ransom A Hospital in Henderson, Kentucky is the second victim of a ransomware attack in the last two months. The first attack using the same ransomware, called Locky, took place in California several weeks ago. The hospital was locked out of its network for 7 [...]
Cloud Computing, Is it as Safe as You Think?
Cloud computing isn't just a buzz word anymore. It is where the majority of data processing and storage is headed, if it's not already there. The cloud offers many advantages over premise-based hosting, the most important of which is Agility. The cloud is scalable and adaptable and in a fast-paced business environment, that is key. [...]
4 Data Security Hacks that Hurt in 2015
The world is constantly becoming more interconnected. Modern broadband technology has brought cheap and reliable communication, increased the efficiency of many processes, and changed entrepreneurship as we know it. It has also opened the door for tech criminals to feast on the ever-expanding availability of sensitive data, and despite the many noteworthy hacking scandals that [...]
Printer Repair Tip: Spring Clean that Printer!
Even the highest quality printers suffer from wear and tear and experience the buildup of dirt and grime through repeated use. These conditions occur very slowly and they can cause your printer to experience diminished performance or even render it unusable. Regular printer maintenance and cleaning is the key to extending the life of your [...]
Computer Repair Tip: 10 Ways to Speed Up Your PC
There is nothing more agonizing than waiting for your computer to catch up with you. It gives bad flashbacks to using dial up modems. Are you willing to try your hand at some basic computer maintenance? The folks at Small Business Trends Magazine outline 10 ways to help you give that PC speed a little [...]
5 IT Solutions That Will Increase Business Productivity
Regardless of the industry, you are in the business of business. You have customers to answer to. You have data to store that is the lifeblood of your business. Are you taking advantage of the IT solutions available to you? They can save you both money and time. Our partners at Avatara share their top [...]
9 Ways to Protect Your Data Security BEFORE Connecting Your New PC
Whether you are managing your business, or your home, you probably use a computer. You use it for searching the internet, paying bills, and storing important records. Computers make our lives more efficient, but also very vulnerable. All of these invaluable pieces of information can be accessed through your network if you're not properly protected. [...]
DIY IT Support: 6 Tips To Troubleshoot Your WiFi
Ubiquitous WiFi connectivity is one of the true marvels of modern life, except when you can’t connect. Few things are more frustrating than computer problems like losing your WiFi connection, especially if you are in the middle of an important task. Instead of reaching for the phone to call IT Support immediately or waiting on hold […]
Hospital Pays Ransom to Hackers in Network Security Breach
Earlier this month, A California hospital's IT systems were taken hostage for an entire week. The hackers inserted ransomware into the hospital's network causing them to lose control of all of their IT systems and demanded $17,000 in bitcoin to release control. The hospital was forced to pay to regain control as quickly as possible. [...]
Managed Services: The Answer to Predicting Your IT TCO?
For small business owners, budgeting for IT expenditures often proves to be one of the most frustrating tasks of running the company. You know you have to spend on essential tech that will put you in a position to succeed, but you find that unforeseen costs can mount over time, busting your original budget and […]
Computer Maintenance Tip: Clean That Case!
Computer users fret about keeping a clean hard drive to keep things running smoothly. You clean out files, run de-frag, and empty your recycling bin faithfully. But there’s physical cleaning to be done in addition to all your digital cleaning. Your PC tower generates static electricity when it runs. This static sucks in dust and […]
POS Systems; Past, Present and the Future
Point-of-sale (POS) systems are one of the most common pieces of technology in modern life, yet we don’t often stop to think about just how thoroughly they changed the nature of business transactions. What once required detailed ledger entries and mountains of paper records quickly became a streamlined operation thanks to the introduction of cash [...]
3 IT Security Failings of the Internet of Things
The seamless synchronization of our multitude of network enabled devices is incredible. They "talk" to each other, sharing and gathering information to help us better understand and control the systems around us. It is the Internet of Things. To put it simply, The Internet of Things (IoT) is the network of physical objects—devices, vehicles, buildings [...]
The Blue Screen of Death! A Good Lesson in Data Backup.
Ack! There is nothing more frustrating, and scary, to a Windows user than the error to beat all errors—the Blue Screen of Death (BSoD for short). This error can cause major data loss for any application that hasn’t saved recently if you don’t actively use data backup. However, even though it is a major, system-wide […]
Terrorist Hackers Violate DHS Data Security, Releasing Staff Info
This week, the U.S. Department of Homeland Security suffered a major data security breach. A hacker released the names, contact info, and job titles of over 9,000 DHS employees. And they said they plan to release the same critical information of 20,000 FBI employees next. Here are the details according to an article published yesterday [...]
How to Save Money on POS Repair
As much as any technological system you rely on, your POS system is the lifeblood of your organization. By facilitating sales, logging crucial data, and communicating with the bank for credit card transactions, a functioning and versatile POS system is an integral part of almost every company’s success. Like any digital platform, eventually your POS [...]
8 Ways Your Computer Problems May Start With YOU!
We all complain about glitchy computers. It’s too old, it never worked right, it keeps crashing. Sometimes it is faulty or outdated machinery. But most of the times the source of our computer problems is good, old fashioned Operator Error. We found a great article from about.com sharing the many ways people screw up their […]
10 Undeniable Reasons People Hate Maintenance Contracts, But Shouldn’t
Service Maintenance contracts can feel like car insurance. You can’t say for sure when or if you’ll need the service and you mentally justify why you don’t want to waste money on what ifs. But this isn’t your car. This is your business, your livelihood. Any number of failures in your IT infrastructure can result […]
6 Tips to Make More Space in Your Hard Drive
Despite exponential growth in memory size and processing speed in computers, we still manage to fill up those hard drives faster than we’d like. The fuller your hard drive, the slower it runs. Here are 7 easy ways to free up space on your hard drive using Windows from HowtoGeek.com: Run Disk Cleanup Windows includes […]
How EMV Will Impact Your POS System
With the EMV Chargeback Liability Shift Regulations in full swing, many US merchants are still scrambling to figure out exactly how the introduction of EMV will affect their POS operations. Chargebacks have become an expensive problem for both the merchants and credit card providers, and these regulations represent an effort to reduce fraud and save [...]
Tech Talk: How to Describe Your Tech Issues to a Service Professional
“It’s making a weird thump.” Your mechanic looks at you and resists the urge to slap his forehead. He has to start at square one and figure out this problem without your help, and on your dime. He’ll figure it out eventually, repair it, and then hit you with a giant bill for the time […]
The Biggest Problems With Printer And PC Maintenance … And How You Can Fix Them
We often go through the work day without thinking about the thousands of ways that technology makes doing business easier, cheaper, and more productive. The times we do tend to notice the tech around us is when something fails, causing us to curse the hardware or software error that led to the shutdown. It’s tempting [...]
Questions to Ask When Choosing a Cloud Service Provider
Moving your business to the cloud can reduce costs, streamline your business' workflow and eliminate the need for an in-house IT support staff. The cloud also makes it easy for employees to work remotely and access information from anywhere with Internet access. Although moving to the cloud is a no-brainer, choosing the right cloud service provider for your [...]
Java: Innocent Plug-In or Data Security Risk
Java, a pre-installed plug-in on many pc's, is causing data security concerns for users. Like so many programs, Java requests to be updated on a regular basis; which many people ignore. As reported by the BBC, research by the FTC has found older versions had a flaw in the update tool that "allowed hackers to [...]
Common Computer Problems You Can Fix Yourself
Any time your computer breaks down, panic sets in and many different thoughts run through your head. And to make matters worse, computers always break down at the worst possible times. Before you get frustrated, the first question to ask yourself is, “can I fix this on my own?” Here’s an article from USA Today about common […]
5 Tips for Ensuring Your Data is Secure in the Cloud
Moving to the cloud is a big decision for any business, and security is an important factor to consider before making the switch. In fact, one of the biggest reasons businesses avoid making the switch is due to security concerns. However, it's important to remember that cloud security has improved dramatically over the past several [...]
Tips for Migrating to the Cloud
Migrating to the cloud is often overwhelming for business owners. Do I need to enlist outside help? What is the first step I need to take? Will my employees be on board? These are just some of the questions running through every business owner's head before making the leap to cloud computing. If you're wondering [...]
5 Benefits Of A Contract Maintenance Agreement
Modern businesses across all industries rely on IT infrastructure, whether it be servers, desktops, printers, etc. These systems are vital to your core processes, which is why an inopportune failure of any one of them is a cause for concern. Rather than being left to improvise when your critical support systems aren’t working when you need [...]
How to Effectively Work in the Cloud
Moving to the cloud is "the thing" to do in the business world, but that doesn't mean it's always easy. Migrating your business' operations to the cloud may seem like a daunting task. How do you get your employees on board? What programs do you use? Should I outsource to a third-party service provider? These are [...]
Up and Coming Trends in Cloud Computing
It often seems like trends in the cloud computing industry change overnight. As enterprises increasingly embrace the cloud for a variety of core processes, the industry is shaped by new entrants and forced to adapt to what clients are looking for. Here are some of the trends driving cloud computing right now. Renewed emphasis on [...]
How Managed Print Services Can Help Your Business
As a business owner, you try to do it all. But even the most successful business owners know when it's time to call in the experts. Something like printing may seem like an easy thing to do on your own, but when you rely heavily on paperwork to run your business, it can be overwhelming [...]
EMV And Your POS System: Repair It Or Replace It?
The recent legislation regarding Payment Networks Liability Shift and EMV microchips is designed to reduce credit card fraud, which has been a serious problem for many U.S. merchants for decades. While it remains to be seen what effects it will have on fraud rates, this policy shift has sent many businesses scrambling to update their [...]
Computer Repair: Are Music and Pictures Slowing Down Your Computer?
Every once in awhile, you notice your computer running slower than usual. Applications won't load, it takes forever to open a document, and programs close unexpectedly. When you have a large quantity of music and pictures on your computer, it's easy to think, "well, that must be the culprit!" But are music and pictures really [...]
The Pros and Cons of Contract Maintenance Agreements
If you run an office, school, lab or any other establishment that requires a sizable number of servers, computers and printers, you might be wondering about the best way to keep your equipment up and running. The two main approaches are to sign a contract maintenance agreement with a provider who will routinely service your [...]
Why EMV May Not be Reason Enough to Upgrade your POS System
Now that October 2015 is behind us, many merchants with POS systems who didn't jump on the EMV bandwagon are feeling the pressure to upgrade. Aging Point of Sale systems that cause constant headaches are not fun and could be a good reason to upgrade, aside from the other benefits of security and chargeback liability [...]
The Most Common Complaints About Cloud Computing (And The Truth Behind Them)
As cloud computing grows in popularity, many managers who are resistant to change are trotting out tired, old excuses for why they advocate sticking with the old ways of doing business. Adopting a cloud-based platform results in a period of change for an organization, as is true when any transition is undertaken. However, the numerous [...]
How to Choose the Right Cloud Service for Your Small Business
Cloud computing is arguably the fastest growing trend in the IT and technology industries. By now, you likely know the benefits of the cloud and how your business could benefit from the switch, but there's still a lot of confusion about how it works. If you still find yourself feeling a little bit confused, you're not [...]
8 Things Your Boss Wishes You Knew About Cloud Computing
Over the last decade, the way we do business has changed dramatically. So why are so many managers ties to the old methods of getting things done? People have been tied to the traditional server and PC methods of IT infrastructure for so long that sometimes it's difficult for them to see the benefits of [...]
Is Your Small Business Making These 5 Technology Mistakes?
As a small business owner, you wear many hats. From IT director to marketing coordinator to lead accountant, your job requires you to do it all. But when it comes to technology, a lack of experience can lead to pitfalls or setbacks in your day-to-day business operations, resulting in lost revenue, downtime, or even lost [...]
What’s Holding Back The IT Support Industry?
Few industries have experienced greater periods of rapid change than IT support. Even as recently as twenty years ago, most employees didn’t have access to a computer, and data security was seen as storing and destroying paper documents correctly. Now, almost every user has a mobile device, and terabytes of sensitive data need to be protected […]
5 Surprising Statistics About Thermal Printers
For many industries, thermal printing has ushered in a new wave of productivity and reliability. For sectors that rely on the mass printing of labels and barcodes, such as manufacturing, retail, and shipping, thermal printers have allowed them to print better quality images faster and more efficiently. Many companies are starting to take notice, as [...]
IT Support Question of the Day: Should You Shut Down Your PC at Night?
It used to be, many moons ago, that as you left for work, you shut down your big desktop computer as you were leaving, then allowed it to reboot as you waited for the coffee to brew. With the advent of such innovations as the laptop and the Keurig, your evening and morning work routines have [...]
Manufacturing IT Support: Why You Need to Embrace Technology
Today's Manufacturing IT Support guest blog is shared from our partner at Informs: One thing is becoming clear to the modern manufacturer: if they want to continue to succeed, they must develop and execute strategies that embrace technological innovations. Increasingly, manufacturers are leveraging digital technologies, the Internet of Things, and other advances to build better [...]
Considering Managed Print? 4 Things NOT To Do When Your Printer Breaks
These days, most people are moving much of their important data and documents to the cloud or other sources of secure, digital storage. It’s likely that you will still need to rely on your printer though for many crucial applications, so the frustration that comes when it's not working when you need it most can [...]
The 9 Most Commonly Misunderstood Facts About Cloud Computing
By now everyone has heard of “the cloud,” but most people tend to associate it with its namesake: i.e. a puffy white ball of nothingness that’s far away and impossible to grasp. Well, folks, the cloud is real, and it could be the answer to your computing frustrations. But not if you don’t understand it, [...]
Top 5 Ways A Move to the Cloud Makes Your Business More Productive
This is a shared post courtesy of our partner, Avatara, LLC and their CompleteCloud blog, and presents 5 ways to make your SMB more productive using new technology: 1. Move to the cloud - based infrastructure. Ok, so you saw this one coming. But don’t just take our word for it; every day, more and [...]
5 Fun Facts About Cloud Computing
Cloud computing is everywhere, but surprisingly few people understand exactly what it is, or the incredible power it has to continue to revolutionize our digital landscape. Whether or not you get the gist of cloud computing, there’s always more to learn. Here are five fun facts you probably don’t know, which may just make you [...]
SMB Best Practices: 7 Key Practices to Sales Success
According to Pipeline Deals, "If you're in a small or medium-sized business, you're always looking for an edge to maximize your sales success." No doubt for every SMB we encounter, especially when we are providing IT support to mission critical applications in the sales cycle. Pipeline recently hosted the Accelerate Sales Conference to bring together the top [...]
5 Things People Don’t Know about Thermal Printers
Unlike traditional printing mechanisms, which use a ribbon to apply ink to surfaces, direct thermal printing uses heat sensitive paper that produces an image when it is heated. The thermal print head heats parts of the paper selectively to produce symbols, images and barcodes. Thermal transfer printers, on the other hand, do use ink as [...]
Physical Security is Crucial to Your Data Security
We write about data security in our blog posts often as it is a topic that goes hand in hand with any IT Support discussion. One aspect that often is overlooked is the actual physical security of your serves and systems. Having a lock on a door to your office simply isn't enough. No amount of anti-virus [...]
Beginners Guide to Cloud Computing
It is imperative when transitioning to the cloud to know what questions to ask, as well as what information is necessary to share with your possible cloud computing service provider. Some businesses make the switch with some ambiguity and no clear understanding of data, business and budgetary needs. These few tips could possibly save you [...]
SMB Best Practices: Why Do You Procrastinate?
Today we share a post from our guest bloggers at Organizing4u.com as part of our Small Business Best Practices series. SMB owners have a lot on their plates, to say the least. Procrastination can harm the success of your organization. Do you find yourself frequently procrastinating? Here are 10 strategies that may be helpful for you: 1. [...]
Thermal Printers: Heating Up The Print Industry
Thermal printing is a process where images are generated digitally by applying heat to heat-sensitive thermal paper. The heat applied to the paper causes certain chemicals to change color, resulting in the desired images being transferred to the thermal paper. Due primarily to its relatively low cost and high speed of operation, thermal printing has [...]
3 Questions to Ask About Your BYOD policy
Nearly half of all companies have a BYOD policy, and more are making the switch every day. Allowing employees to use their personal devices (smartphones, tablets, laptops) for work responsibilities can result in increased productivity... and increased security concerns. We are sharing a post today from our partner at Informs, Inc. that presents 3 questions companies [...]
Unique Challenges Arise With Thermal Printer Repair
Businesses across many different sectors are increasingly turning to thermal printers for their printing needs. Companies are always looking for unique ways to reduce costs and increase productivity, and thermal printing manufacturers have aligned their value proposition with these goals, resulting in rapid sales growth that is forecasted to continue for many years. While managers, [...]
Is it Time For Your Business to Scrap the PC and look in the Cloud?
The PC has been a mainstay of the business world for decades, which is a rare feat in the frenetic world of technology hardware. Its form may have transitioned from towering desktops and chunky monitors to sleek, lightweight laptops, but the essence of the PC has remained intact for far longer than most pieces of [...]
Warn Employees Against Ashley Madison Phishing Scams Now
The following is a Phishing Scam Alert from the KnowBe4 blog regarding the Ashley Madison breach, and while it is making 35 million+ people very nervous, it is important as a business owner or IT admin to educate your network's users how the breach can cause some serious issues in IT environments (let alone marriages). Phishers [...]
How Thermal Printing is Changing The Print Industry
Where once you had to physically visit a store or call a salesperson in order to purchase anything, now you can seemingly buy everything with just a few taps on a smartphone screen. This massive increase in the online purchasing market has resulted in a proliferation of new manufacturing and retail businesses. It’s no secret [...]
Signs (and Labels) That Print is Not Dead
The global printing market is expected to top $980 Billion by the year 2018, according to a report by Smithers Group. This growth is despite the fact that many consider print to be dead, as we move towards an expanding paperless world. Consider, for example, the items and events in your life that are now [...]
The Most Innovative Developments In Cloud Computing
Managers across a diverse array of sectors are increasingly turning to the cloud to manage their IT infrastructure. Thanks to exponential leaps in technology such as bandwidth speed and data compression, cloud technology is now more accessible than ever and can provide tangible benefits for almost any company. Business leaders now realize that the days [...]
Don’t Make These Easily-Avoidable Mistakes With Your Disaster Recovery Plan
You may think your organization has implemented a foolproof and robust data backup plan, but it’s not until disaster strikes that the mettle of your efforts will truly be tested. Data recovery technology, like every other sector in the IT services field, continues to change at an intense pace, and as even legacy companies begin [...]
Important steps to getting started with cloud computing
The following is a guest post from Avatara LLC. Great Lakes Computer is proud to be a partner/reseller of their CompleteCloud product. When considering a transition to the cloud, it’s important to know what questions to ask and what information to convey to your potential hosting provider in order to make your move as seamless and smooth [...]
Census Bureau Data Breach Brings Up the Question of Downtime
Late last week, officials discovered the Census Bureau's Federal Audit Clearinghouse site experienced a data breach and was hacked. Details of the hack are shared below in an article from The Federal Times. The news of another hack is concerning, but by no means a shock. The biggest news in this recent release is that [...]
Protecting Yourself Against Cyberattacks
Today's post on IT security from cyber attacks is shared courtesy of Todd Pouliot of Gateway Financial, LLC: 25% of Americans were cyberhacked between March 2014 and March 2015. The American Institute of CPAs announced that alarming discovery in April, publishing the results of a survey conducted by Harris Poll. Disturbing? Certainly, but the instances of [...]
4 Cloud Computing Myths for SMB’s
The following is a guest post from Avatara LLC. Great Lakes Computer is proud to be a partner/reseller of their CompleteCloud product. Despite the rapid adoption of cloud computing in government, business and our social lives, there are so many misconceptions concerning what it is and what it does. When technology is understood, the benefits [...]
Ask Me about Anything: 10 Answers To Your Questions About Office 365
No matter what business you are in, the idea of not using technology is absolutely absurd. In today’s society technology is the way that businesses get into the public eye and become relevant to the audience they target. This is why having good software to help maintain your business is a great idea. A popular [...]
An Introduction to Office 365
When Microsoft initially released Office 365 home, university, business, and personal it was the company stepping up their technology game. The release of a program set that works on the new tile version of Microsoft and can be usable for Mac and mobile devices showed that Microsoft wasn’t resting on their past success, but trying [...]
Changes in Company Culture Accompany a Move to the Cloud
While there's a long list of technical tasks involved in a cloud migration, one of an organization's biggest hurdles to being in the cloud is its culture. As we discuss moving to the cloud for more and more of our clients and their applications, we are sharing this post from TechTarget entitled "Avoid culture shock in [...]
What Not to Do In Your Data Backup and Recovery Plan
Assuming your company is one of the many small business that has gotten better about data security and loss prevention, you are probably ahead of the curve. According to the Small Business Administration, most companies do attempt to backup critical data, but less than 40 percent of small companies have any formal plan at all. [...]
5 Costly Mistakes You Are Making With Your Backup and Recovery Plan
According to some insights from PropertyCasualty360, large businesses take disaster planning much more seriously than the majority of small businesses. However, as the Small Business Administration points out, 40 to 60 percent of small companies never reopen for business after a disaster. Since the "risk managers" in most small businesses are simply the owners or [...]
Data Security: Can Hackers Take Control of Your Products & Equipment?
Could you imagine what would happen to your manufacturing company if a hacker took over your control systems? It happened to a German manufacturer. The company could not shut down their blast furnace. The damage, according to a report by Wired, was massive. The hackers accomplished the feat by accessing the steel mill through its [...]
Beyond IT Support: A Guest Blog About Organizing your Home or Small Office
In today's Beyond IT Support blog post, we welcome guest bloggers again today from Muffy and JoEllen over at Organizing4u.com to blog about de-cluttering our work lives - even when your work life is at home. Here are Home Office Ideas: Do you have a home office that is in need of help? Clearing the clutter is one [...]
4 Features Of Office 365 That Will Help Jumpstart Your Small Business
As Microsoft prepares to end support and updates for its Small Business Server 2003, many professionals are exploring the cloud-based Office 365 as a potential replacement. The idea of switching from a platform with which you are intensely familiar to an unknown quantity can be a daunting task, but Office 365 offers several benefits over [...]
Keeping up with Employee Demand for BYOD
If you have not adopted a Bring Your Own Device (BYOD) policy for your business, you may no longer have the luxury of delaying. According to the article, Business trends for 2015: the mobile workforce and BYOD maturing, employee demand will be the main component of growth for BYOD: In 2015, technology, more than ever, will [...]
What Does the End of SBS 2003 Mean For Me?
If you've been relying on Windows Small Business Server 2003 to manage your company's IT infrastructure, it's time to begin investigating other options. Beginning on July 14, 2015, Microsoft will end support for the mainstay OS, and many users will be scrambling to update to a supported platform. There are several options available, but you need to [...]
Ransomware: To Pay or Not To Pay the Ransom?
The following post was featured on TechTarget SearchSecurity earlier this week and is being shared as we have many clients who have asked us this hypothetical question, in the hopes that the day doesn't come that they have to know the answer. Thankfully, they are working with us and have a sound Data Backup and [...]
The State of Healthcare IT Security in 2015
Have you had time to research IT security and how it can impact your healthcare company? If you haven’t, don’t worry, we’ve identified some of the risks and have listed some suggestions to help you get started: 1. Almost Half of All Healthcare Companies Have Had 1 Data Security Incident in the Past Year Did [...]
5 Astonishing Data Security Mistakes Law Firms of All Sizes Make
While law firms have made significant progress in closing data security gaps, they’re still far from perfect. Take a look at some of these common mistakes many make: 1) Not Knowing Where Your Cloud Computing Services Provider Stores Your Data: Every cloud company stores data in multiple physical locations in or outside of the United [...]
Rombertik Identified by Cisco as a New Suicide Virus
Rombertik is a new malware that is making data security headlines, as it collects everyday data you may enter into websites. It specifically targets collecting the data that users type in fields on websites, such as usernames, passwords, addresses, phone numbers, etc. It is spread through phishing emails. Below is the information to be aware [...]
BYOD: Companies are inviting staff to bring their own computer to work
What is BYOD? Bring Your Own Device (BYOD) is a growing trend that is helping many businesses to expand their worktime coverage and reduce costs. The concept is simple: rather than employees only using business owned computers and mobile phones, they configure their own devices to enable them to access business documents and resources. The [...]
2015 Data Security: The Rise of Hacking Campaigns
Even though technology makes it harder for criminals to do their work, it’s not bullet-proof. In fact, there are many criminals equally as innovative as their private industry counterparts. So they’re fast at developing new methods for attacking your business.Take a look at some ways they might do that in 2015: 1) State-Sponsored Hacking will Continue [...]
‘Ransomware’ a Growing Threat to Small Businesses
I came across an interesting article in the Wall Street Journal regarding recent advancements by cybercriminals to attack small businesses with ransomware, and essentially use malware in bogus emails to freeze SMB computer files, and demand a ransom to unlock them. You may recall we have reported on this before, dating back to 2013, but [...]
5 Data Backup Myths to Ignore
The AT&T Small Business Technology poll found 9 out of 10 small businesses backup their data daily. But, you still hear stories all the time about SMBs that lose their data or don’t comply with given standards. So mistakes still happen. Don’t let yourself be a victim! Ignore these common data backup myths: 1. Onsite [...]
3 Myths About Cloud IT that May Hold You Back From Its Benefits
Companies (especially law firms) of all sizes are adopting cloud computing on a greater scale than ever. But some firms have fears that are still holding them back. Take a look at them, they may be familiar to you: 1. The Cloud Costs More Than Our Budget will Allow: Most cloud apps charge an annual [...]
7 Ways Cloud Computing Can Revolutionize Your Manufacturing Company
As a manufacturer, you are under constant and intense pressure to produce with speed and accuracy. On top of that, every customer interaction counts. How do you keep up with it all, running a solid business that continues to grow in reputation? 1. Add Convenience for Your Customers with Added Services: With the cloud, you [...]
5 Antivirus Mistakes You’re Making Right Now
Once you get an antivirus program, you can totally forget about it, right? You don’t have to do a single thing more because the program does all the work for you…Well, yes and no. Antivirus does protect you so you don’t have to guess which links and downloads are safe, and which aren’t. But, you [...]
5 Signs You’re Not Ready for Disaster Recovery
You’ve got a great disaster recovery plan in place…so you think. You’ve spent hours testing and bulletproofing it from top to bottom. To you, it doesn’t look like there’s a thing wrong. Everything on the surface looks great, but there are things you’ve forgotten to check. Even as you create your disaster recovery plan, your [...]
Do I Really Need to Scrap SBS 2003 When It Works So Well?
Nobody wants to spend money on upgrading a server or moving to another solution when the one they use works so well. But with the End Of Support for SBS 2003 looming, it is, sadly, not really a choice. I believe that this conversation on Microsoft's TechNet sums up perfectly what many SMB's are asking right now [...]
6 Biggest IT Needs Companies Should Outsource
Your company, whether a law firm, manufacturing plant, or an SMB of any sort, has many IT issues that need to be addressed. But how do you decide which are the most important and whether you should outsource them? Take a look at this list of commonly outsourced IT problems: Computer/printer repair – If you’re […]
10 Things to Know Before Moving to Office 365
With Microsoft's Small Business Server 2003 making its grand departure from the world of support and updates in July 2015, it is time to consider your options if you have not done so already. One option many companies are considering is Office 365, and with good reason. It is a convenient solution, great for remote [...]
Top 7 Disaster Recovery Questions & Answers
What are the top questions your organization should be able to answer about disaster recovery? They might be these: 1. Has Your Senior Leadership Bought into the Need for a Disaster Recovery Plan? If not, it’s time to start talking about one. Yes, it’s unlikely your physical location will ever be destroyed by a natural [...]
6 Tips for Choosing the Best Antivirus for Your Business
If there is one good thing about viruses, it would be that they stimulate competition in the marketplace to make the best antivirus software. As a result, there are many great options to choose from. But you shouldn’t choose on brand name alone. After all, marketing can make an ineffective data protection program appear to [...]
The 5 Largest Healthcare Data Security Breaches of All Time
Did you know healthcare data breaches make up 44% of all data security breaches? That makes them the most frequent data breach of all. Criminals use this information to: Buy prescription drugs and sell them on the street File false tax returns under your patient’s names Use other medical services in their name Open credit [...]
Small Business Best Practice: Think Spring and Organize!
Today's blog post is from our guest bloggers at Organizing 4 U and encourages you to "Think Spring Cleaning" with these SMB office organizational tips: Another snowy day in Northeast Ohio causes some doubt that Spring is almost here. But it really is March and it is good to know that things will be warming [...]
The Complete Guide to Managed IT Services for Law Firms
How new are you to managed services for law firms? It sounds like a generic term at first, so you might not know exactly what it means. What it means in reality depends on the company too. But, it should refer to the proactive monitoring and maintenance of your IT architecture. So, your network issues [...]
SBS 2003 End of Support: The Pros and Cons of Outlook 365
September 21, 2004: Windows Small Business Server’s success and soaring adoption rate are notable and is selling itself. In less than 1 year of deployment, Windows Small Business Server 2003 has outsold its predecessor Windows Small Business Server 2000 by 200 percent. July 5, 2012: Microsoft end-of-life for the SBS family, with extended support available. July [...]
The Scary Malware you Probably Don’t Need to Worry About – YET
An article in pcworld.com this week entitled “Destroying your hard drive is the only way to stop this super-advanced malware” caught my attention. And with good reason. Upon reading the article two things stood out to me. The world of cyber espionage is a scary place and capabilities are getting too advanced that I really fear for [...]
5 Tips for Creating Disaster Recovery Plans
57% of all small businesses do not have a disaster recovery plan ( yes 57% - you are not misreading). Now it’s true that most small businesses like yours will not experience a natural disaster that threatens your physical premises. However, it’s kind of like buying home owner’s insurance. You probably will never need it. [...]
Advice on Anthem Data Breach: Monitor Your Children!
The news of the Anthem BC/BS data breach spread fast. Faster than Anthem seems to be responding to clients about it, unfortunately. But not as fast as the attackers have started to use the information stolen. Reports have already surfaced of phishing emails from the attackers to victims. There is a lot of advice being offered [...]
5 (More) Deadly IT Support Sins SMB’s Commit
Most small businesses experience IT problems that are totally preventable had they taken the correct action in the first place. Who knows how many millions (billions?) of dollars get wasted each year because of this? Yet not taking wise action jeopardizes your entire business. Here are some of the most common IT support and security mistakes [...]
When’s the next big data breach going to happen?
Notice that we didn’t use the word “if.” It’s the unfortunate reality we live in. The web connects people from around the globe. And for the most part, that’s a good thing. But a certain percentage of people will always misuse it for their own best interests. And you have to protect your healthcare company [...]
5 of the Most Established Cloud IT Solutions of the 21st Century
Over the years, cloud-based tools have gone from something of a niche to being used on a daily basis by some of the biggest organizations in the world. What are they though, and what makes them so hugely appealing to businesses? Cloud IT solutions and based services, or cloudware, are delivered online rather than ‘on [...]
3 Law Firm Data Security Breaches
“Most major U.S. law firms have been victims of security breaches, and the unwelcome threats likely operated covertly for up to nine months before they were discovered,” says the American Bar Association Journal. Sounds scary, doesn’t it? Let’s take a look at some of those breaches, and what happened: 1. Alabama Law Firm McCutcheon & [...]
Top 5 Data Security Challenges You May Not Know About
Did you know hackers are not afraid to take control of your business's equipment remotely? The US Department of Homeland Security, for example, recently investigated medical devices for exactly that flaw. In fact, a Russian hacking group, "Energetic Bear," has made no secret of some of their attacks on US industrial control system equipment manufacturers. [...]
5 Disaster Recovery Best Practices Your SMB Must Have
Can you imagine all of your business, or most of it, getting completely destroyed in a natural disaster? What would you do? To many, it seems that having a disaster recovery plan in place is not necessary. But according to Symantec, 74% of SMBs have none in place, while a dismal 21% are “extremely confident” they [...]
New Report Predicts 10.1% Market Growth For Managed Print Services
A report released yesterday on CNBC indicates the Managed Print Services market is expected to grow at a compound annual growth rate of 10.1% over the period of 2015-2019. The factors driving this growth are: Eco-friendly print solutions and carbon footprint awareness Total Cost of Ownership (TCO) Increasing need for document security Here is the [...]
Data Protection: 4 Best Ways to Protect Healthcare Companies from Cyber Crime
Do you want your healthcare company to be like Jersey City Medical Center, which lost the private data, including social security numbers, of many of its patients? It happened because someone lost a CD with all this data on it. And the data was unencrypted, so cyber thieves didn’t need any skill to get away [...]
15 Data Backup and Protection Vows You Should Make for 2015
Happy new year from Great Lakes Computer! I am sure your minds are a little foggy from the past 2 weeks of holiday celebrations, so I am going to get right to the point and keep my blog this week simple about data backup. Here are 15 promises for 2015 you should make to yourself [...]
Have You Heard about the Nasty “Bash” Bug Computer Virus?
Do you remember Heartbleed and all the chaos it caused? No one seems to have accurate estimates of the total damage it caused, but one cloud vendor found that it cost them around $400,000 in lost network bandwidth. It seems like you hear of a new virus that’s going to destroy the Internet almost every [...]
IT Security: 4 Signs Your Manufacturing Company’s Network Has a Virus
Viruses slip by anti-virus and anti-malware protection all the time. Your users often allow them through by clicking on something they shouldn’t. Sometimes, they’re so cleverly designed that they sneak right through, regardless of how good your protection is. And if a certain cybercriminal is determined enough, they can get through with enough time and [...]
The 5 Most Destructive Viruses of 2014 and Why You Need IT Support
In 2014, these bad guys have turned some companies absolutely upside-down. What are they, what did they do, and are you prepared for them? Many companies weren’t – and still aren’t. Take a look at the worst viruses of 2014 – and make sure you have great Managed IT Services in place to protect you: [...]
Disaster Recovery Statistics that will Silence Your Lambs
Quid Pro Quo, Clarice: In exchange for a few minutes of your time reading this blog post, I will provide some disaster recovery statistics for your business: 43% of companies were immediately put out of business by a “major loss” of computer records. 51% permanently closed their doors within two years. That means that only [...]
4 Computer Virus Items Your Company’s Users Shouldn’t Click On
Quick: what’s one of the leading causes for all viruses any computer network gets? User error! And unfortunately, no matter how good any antivirus program is, it can’t possibly make up for every possible computer virus your users could click on. They could easily thwart your entire data protection plan with a single click! Some [...]
SECURITY ALERT: Fastest Moving Computer Virus Hits Millions Worldwide
On December 6th millions were hit by what experts are calling the fastest moving computer virus ever. The data security attack hit the UK very hard, but in the world of cyber crime, it doesn't take long to spread worldwide. Here are the details that you need to know to avoid the bug and protect your [...]
5 IT Support Tips to Keep Your IT Equipment Fast and Current
Your small business absolutely needs these tips. When time and financial resources are scarce, they help you stay competitive versus other bootstrapping SMBs. What can you do to make sure your IT infrastructure serves your client’s needs, while also not driving your own costs through the roof? Here are some tips: 1. Upgrade Hardware in [...]
Small Business IT Support: Ten Tips for A More Efficient Work Day
Thanks to our friends at Organizing 4 U, here are some tips that will make you a more efficient worker, and get all you need done in this shortened week of Thanksgiving. Because even though the work week is shorter, there is no shortage of work! Ten Tips for A More Efficient Work Day: Start [...]
Do You Get 100% Uptime from Your IT Support Team?
Wouldn’t 100% uptime be your ideal vision? Is it even possible to achieve in any given year? Maybe and maybe not. But you should be at least at 99.8% uptime. Get any less than that, and your healthcare business (or any business for that matter) loses a ton of capacity to serve, grow, and profit. […]
5 Consequences for Law Firms Without Disaster Recovery Plans
According to FEMA reports, 40% of businesses (or more) are affected by serious superstorms. For example, think of Hurricane Sandy. And unfortunately, many businesses, including law firms, find they are not prepared when a disaster like this strikes. In the case of Sandy, 31% of affected businesses still couldn’t operate – even 6 months after […]
Your Manufacturing Company Isn’t Safe from Data Security Breaches
You would think that, as our world grows and advances technologically, the cyber world would get even safer. But the reality is that it only becomes more difficult (not impossible) for cyber criminals to do their work. And they work just as hard at disobeying the law as the good guys do at obeying it. […]
Are You Making These 5 Deadly Managed IT Services Mistakes?
When you go out to find an IT support team, they’re supposed to be the expert, right? Well, yes and no. You have to be careful because not every third party puts your best interests first. Regardless of the type of small (or large) business you run, here are some IT mistakes you must avoid: […]
10.5 Secrets to Reduce Your Technology Costs
We welcome back fellow Northeast Ohio blogger, Brett Harney, of Corporate Technologies Group, to share their whitepaper with our IT Support blog subscribers on ten and a half secrets you can use to reduce your technology costs when it comes to your network bandwidth and connections: 10.5 Secrets to Reduce Your Technology Costs Posted on [...]
4 Top Data Protection Tips for Healthcare Companies
Fact: did you know that more than 260 healthcare data breaches have affected more than 10 million patients? And did you know this happened in the span of just 2 years, from 2009-2011? This is according to the US Department of Health and Human Services. You can check the entire list of data breaches here. […]
The difference between disaster recovery and business continuity
We have been talking a lot about Data Protection, Disaster Recovery and Business Continuity. People tend to use these terms interchangeably. I came across this great article on Dell’s Tech Page One that describes the importance of each and the differences. Here is the article: The terms business continuity and disaster recovery are often mistakenly […]
Warning: Your Law Firm’s Data Security Measures Aren’t Secure at All!
We’re not saying this just to scare you – it’s the truth. Even the highly conservative financial industry has already adapted to the cloud. The Legal industry as a whole, however, still lags somewhat behind. Joseph M. Burton, who writes for LawPracticeToday.org said: “The need for better cyber security, along with the responsibility to safeguard […]
3 Glaring Reasons Your Manufacturing Company Needs Managed IT Services
You hear almost every day about big companies that have millions of customer’s information hacked and stolen. There’s Target, Home Depot, and many others. But what about companies that focus on manufacturing? Well, they’re no exception to the rule. Take a look at some of the largest manufacturers and what happened: 1. Microsoft: You don’t […]
Business Decisions: When To Invest In IT Support
Running a business is no easy task. From operations to finance, it all comes down to your final decisions at the end of the day. In this ever-growing IT based world, deciding when to invest in IT outsourcing for your business is critical. And don’t worry, by the end of this you will be enlightened […]
4 Data Recovery Best Practices Your SMB Needs to Use
You love technology – until it fails. And fail it will! It’s not a matter of if, but when your data storage devices fail. Hard drives all have a certain life, and some time or another, they will fail. You know it’s important to have a data backup plan in place, and the same goes […]
Does Your IT Support Company Comply With HIPAA?
When you store and protect data regarding patient health information, you have to do so according with HIPAA’s strict standards. If you don’t, you could cost yourself $1.5 million per year in fines! At a very general level, HIPAA requires you to take appropriate measures to safeguard private health information. And if you have an [...]
IT Support and Social Media – Personal and Professional Legal Advice
Today’s IT Support guest blog post is from the law office of Slater & Zurz, and is good advice for not only social media usage in SMB’s, but in our personal life. Even when not involved in a legal dispute, it is always wise to BE CAREFUL. EVERYONE INVOLVED IN AN OHIO LEGAL PROCEEDING SHOULD […]
2 Data Security Measures Every Law Firm Must Take
As long as 5 years ago, the FBI started warning law firms that hackers specifically target them. At the time, they cited the most common hacking attempt was to use e-mails to access computer networks and steal data. The report also continued on to note these attempts had begun as early as 2007. Now in [...]
Prevent a Breakdown with Routine Printer Maintenance
This is a guest blog from our friends and fellow bloggers at Market Point. When it comes to protecting the investment in your printer fleet and safe-guarding the reliable printer performance your business depends on, the importance of routine printer maintenance cannot be overstated. Poor print quality and printer downtime negatively affects your users and your [...]
5 Awful Data Security Mistakes Manufacturers Make after a Breach
I’m sure by now you’ve heard of the Home Depot security breach. If you haven’t, it could be one of the largest of all time, as it may have affected up to 60 million customers (possibly more). Estimates suggest up to $2 - $3 billion in fraud may affect these accounts. When it’s all said [...]
Rising Costs A Growing IT Security Concern With Data Breaches
The following is a data protection guest post article from Manmohan Hebbar at LockLizard PDF IT Security: Whenever a data breach takes place in an organization, it serves as a cautionary note for other enterprises. IT administrators gather information from such events in order to prevent similar attacks in their organizations that can severely damage […]
4 IT Support Keys for Manufacturers
One of the main reasons for the existence of the manufacturing industry is to make components that make things easier for other people and businesses, right? So it logically follows then that IT support for you should make your own internal operations easier too. Take a look at a few important ways IT support should […]
8 Quick Data Recovery Tips for Manufacturing Companies
Do you have the perfect disaster recovery plan? Let’s say a massive fire completely destroys your business… How soon would you be able to get it up and operating again? If you have a good disaster recovery plan in place, you should experience almost no downtime at all. If you’re not already doing these, this [...]
Beyond IT Support: A Guest Blog About Organizing Your SMB (and Life)
We welcome guest bloggers again today from Muffy and JoEllen over at Organizing4u.com to blog about problems all Small business owners, make that everyone, faces. Because no matter how reliant we have become on email, standard paper mail still exists, and not just to clutter our lives. Here are Keys to Staying on Top of [...]
What is the ideal life span for your printers?
This is a guest blog from our friends and fellow bloggers at Market Point. Historically, businesses have purchased printers and used them until they expire, which can take 10 years or more in some cases (we know some of you still have Optra S devices from 1997 out there!). Yet, these same businesses are leasing [...]
Special Edition: 4-Tips on Data Protection for Manufacturers
Your major competitive advantage versus other manufacturers could be a super-secret proprietary process. Maybe you have customer service methods that are so efficient and pleasing to your customers that you don’t want anyone else finding out. And of course, you don’t want someone to steal your client’s information. Data protection breaches happen all the time, […]
Importance of a Law Firm Disaster Planning in IT Support
This article was written by attorney James W. Slater of the Ohio law firm Slater & Zurz LLP Although it seems quite remarkable that a business would not back up computer files in a more sophisticated way than duplicating data to the “C” drive or having an external tape device, some businesses have rather primitive […]
5 Reasons Why Laptop Repairs Are More Difficult And Expensive
Laptops have become thinner, lighter, faster and their screens more brilliant than ever before. However, packing all this technology in an increasingly shrinking form factor has made it increasingly difficult to repair when the time comes. Unlike with laptops that were sold a few years ago, today the latest Ultrabooks are a lot thinner but [...]
5 Printer Repair Problems that Show It’s Time for a New Printer
Has your printer reached the end of its life? If you’re experiencing a need for one of these repairs, it has in most cases. Check out some printer repair problems that show it’s more worth your time and money to buy a new printer instead: 1. Ink Systems that Clog too Frequently:Some printers are known […]
Data Security Challenges Law Firms Face with Younger Attorneys
Not long ago I wrote an article for this blog entitled "Why Law Firms Need an IT Policy for Data Security" and it discussed young employees' (specifically, millenials) computer behavior and how it is impacting Law Firm IT Support and data security. Check out these stats: Seven out of ten (70%) young employees break their [...]
5 Ways to Convince Your IT Support Team Outsourcing’s Okay
Imagine this: You’ve been an employee working loyally for your company for years. Now, after all this hard work, you hear that your company is going to start looking at outsourcing options. Your personal position at work may not be impacted at all by outsourcing. However, your employee’s minds will be flooded with fears. Primarily, […]
DRPs and BCPs Should Not Be MIA in your IT
Disaster Recovery Plans (DRP) and Business Continuity Plans (BCP) are important for organizations to have in place, but for some businesses, they are a requirement. Healthcare, Financial Industries (such as banks and credit unions), and Legal Practices are just a few examples where there are requirements, even laws, mandating that these are in place and […]
Here is Why Your IT Support Cannot Ignore Tablets
Tech Target recently published this blog post entitled "Why IT can't ignore tablet computers" that provides some useful insight into the whole BYOD and BYOx debate. View our post "Mobile Data Security: Forget BYOD - Now the Buzz is BYOx! Here is the post: Can tablet computers really replace desktops? No! Does that mean you [...]
Does Free Antivirus Software Do the Job?
When you run a small business, you spend money on the bare essentials – and that’s it. Sometimes, that means cutting some corners. Others, it’s hard to tell what really is essential to running your business. So does antivirus fall into the category as something essential that you should spend money on? Let’s take a [...]
Should You Do Any of Your Managed IT Services Yourself?
For SMB’S of any size, it’s always difficult to understand when you should take something on yourself by hiring more staff, or outsourcing it. The true answer is, it all depends on your circumstances. At every stage of growth, however, whether you are a startup or rapidly growing up-and-comer, there are tasks to outsource and […]
Do Cyber Criminals Have Your Law Firm In Their Cross Hairs?
This Guest Post article was written for Great Lakes Computer’s Tips on Tech Blog by attorney James W. Slater of the Ohio law firm Slater & Zurz LLP: With maintenance of confidentiality actually a requirement for lawyers dealing with clients due to professional ethics regulations, protection of data is a very important aspect of an […]
If a Law Firm’s Printer Falls in the Woods, Does it Make a Sound?
Why Your Law Firm Needs to Look at Managed Print Services Now When your law firm’s printers jam or break, who gets called on to repair it? If you are a large enough firm to have an IT person on staff, the answer is obvious. But for those firms who cannot afford that luxury, or […]
Printer Repair: What are the Pros & Cons of the Best Brands?
Having printer problems? Do you need to make a printer repair? It may be time to buy a new printer instead! Printers are one of the most complicated pieces of technological equipment to buy. If you’ve been reading our blog, you know that the real cost of any printer is in the ink. And in [...]
New Guest Blog Series: SMB Best Practices for Organization
This is the first in a monthly series of guest blogs from Organizing 4 U, a fellow Northeast Ohio Company and CMBA Partner. They are professional organizers for business and residential, who will share with our readers some insights into organizing your business – and your life! Today, they discuss organizing your computer files. This […]
Heartbleed Bug Still Able To Compromise Data Security on 300K Servers
Like a flash in the pan, the Heartbleed Bug has faded away from mainstream news to only be whispered by those data security experts assigned to address server security issues for companies. With the lack of any current information to the public at large, many Internet users will be led to believe that servers are [...]
Are You Doing These 4 Simple Network & Server Repair Operations?
Are you the do-it-yourself type? This works for and against you. On the one hand, you can teach yourself how to tackle virtually any problem business or life throws at you. On the other, you can end up taking on too much and stressing and burning yourself out. If you’re doing your computer, IT support, […]
760 Data Security Reasons to Switch to a New Operating System
According to TechTarget's recently posted article "6 Benefits of Migrating to Modern OS's," The Dell SecureWorks Counter Threat Unit (CTU) has catalogued more than 760 vulnerabilities in Windows XP, and predicts “continued discovery and disclosure of new software vulnerabilities linked to Windows XP well beyond the end-of-support date." So, it could be said there are [...]
5 Data Protection Questions (And Answers)
What do you know about data protection? Even if you’re just a newbie, that’s okay. Today, we’re going to cover a few common questions small business owners often ask. Here they are in random order: 1. What makes data security so important for your business? You know the obvious one – to protect the confidential [...]
4 Budget Busting IT Support Mistakes When Moving your Office
‘Tis the season to move offices, it seems. We get a great deal of calls in the heat of summer and around the holidays from companies relocating to different office space, and requiring assistance with their IT equipment. It could be that with vacations, business is slower and summer is a good time to make […]
Top 5 Benefits to Look for When Hiring Managed IT Services
When you hire managed IT services, not all companies are the same. There’s what they say they do – and then what they actually do. At Great Lakes Computer, we want you to get the very best service from your provider when you sign the contract. Before you actually do that, here’s what you should […]
IT Support Guest Blog: Perfecting Network’s Performance
It is time for our monthly guest blog post from guest blogger, Brett Harney, principal at Corporate Technologies Group in Hudson, Ohio. Today Brett is sharing with the readers of our IT Support blog excerpts from his eBook, available for free download, on perfecting your network’s performance: “Businesses are increasingly more aware of the quality […]
Printer Repair: 4 Tips on Buying the Printer Your Office Needs
So your printer just broke down, and you’re tired of having it repaired. Or maybe it’s old, and you know it’s time for a new one. You can buy a cheap one that just gets you by, or you can get the deluxe powerhouse version that prints 20-50 pages per minute. How do you know […]
How Secure is that Coffee Shop Connection? A Data Security Discussion
We have all done it. Some time between meetings, stop at Starbucks and get some work done. Check email while you are waiting for your flight at the airport. Or even shelling out the $30 to connect on the plane during that cross country flight for a sales meeting to finish that presentation or send [...]
5 Telltale Signs It’s Time to Hire an IT Support Company
If you’re a small business owner, you have to constantly evaluate whether to do it yourself or hire someone else. How do you know when you’ve crossed the threshold from being able to do it yourself to having to hire an outside vendor to do the work? When it comes to IT support, you should […]
Mobile Data Security: Forget BYOD – Now the Buzz is BYOx!
We have been discussing BYOD (Bring Your Own Device) for a while now and its impact to your company's data security plans. BYOD is employee-owned devices being brought into a business. Smartphones, tablets, laptops and USB drives are all examples. Bring your own everything (BYOx) is an all-encompassing term that covers various BYO-related trends in [...]
Top 5 Viruses and How They Have Impacted Data Security
You know what the most amazing part about Heartbleed is? It was around for two years before any news came out about. And it also affected about 2/3 of all internet servers. Doesn’t it seem amazing something like this could happen in the internet of 2014? It just goes to show you anything can happen [...]
Exploring The Safety Of Info In The Cloud
Cloud storage has become one of the most popular tools in recent years. Instead of taking up room on our hard drives, we can simply access a kind of ‘virtual hard drive’ located on the web, and just transfer our files to this online storage location. But many doubt the safety of this new tool. […]
5 Best Managed IT Services to Outsource
Should you do it yourself, or should you let a managed network services provider do it? It’s a tough call, and a lot of the decision depends on the budget and IT needs your business has. Here are some of the top services you should consider in general, regardless of your business: Data Security: Data […]
7 Reasons Why You Should Consider Cloud Services For Your Business
Otherwise known as ‘cloudware’, cloud technology is being exploited by more and more businesses owners because it can enable them to dramatically reduce their IT Support and overall IT costs, and improve their flexibility. Your employees can work from home: Because employees don’t need to log in to a work computer to access files and […]
Printer Repair Problems: 7 Signs It’s Time for a New Printer
Should you keep repairing your printer, paying a little at a time? Or is it time to purchase a newer model? That’s hard to figure out on your own if you’re not an experienced IT pro. But if you do use the professionals, here’s what they look at to decide if it’s time for a [...]
3 Challenges in Voice over IP SIP Trunking Implementations
In today’s blog post, we welcome again our guest blogger, Brett Harney, to continue his discussion from his last guest post with us: A Buying Guide for Small Business: VoIP vs. Hosted VoIP. Brett is a principal at Corporate Technologies Group in Hudson, Ohio, and today he is sharing with us 3 Challenges in SIP […]
The Complete Newbie’s Guide to Computer Hardware Repair
What do you do when you need a hardware repair made? Do you call a professional? Should you have a contract set up with an outsourced option so they can perform the service for you? Or should you just do it yourself? DIY works out okay in some situations. For more complex repairs, though, you [...]
5 Simple Data Backup Tips You Can Use Today
Since the takeoff of the Information Age in the 1990s, you’ve probably heard the words “data backup” preached at you time and again. And for good reason. You don’t want to lose all your valuable data that you spent years developing and accumulating in an unexpected disaster. Today, backing up your data is a little […]
Data Protection: Is Changing My Password(s) Enough When My Email Or Social Media Account Has Been Hacked?
Today we welcome +Katrina Matthews, a product specialist and blogger for RackSolutions, manufacturer of custom racking solutions for businesses. When you lose control of an account because a person stole your password or a hacker used a computer program to generate a password and accessed your email, financial, social media or other account, it can […]
Top 3 Mistakes Made When Searching for an MSP
As with any vendor-provided service, some companies do a better job than others even though you might pay exactly the same price. You’ll have to talk with multiple managed network services providers before you find one that meets your needs at a price that works for you. As you go through the process, though, make […]
Internet Explorer Vulnerability Causing Major Data Security Concerns
This article on the latest data security vulnerability is being shared with our blog subscribers from ABC NEWS: "Clicking on one malicious link in Internet Explorer may be all it takes for hackers to hijack your computer, according to warnings issued today by Microsoft and the Department of Homeland Security. Federal officials advised that people [...]
Reduce Print Costs by Printing Less: 6 Critical Things to Do Now
Isn’t a bit ironic that you have a high-speed office printer, but that nowadays everyone’s primary concern is helping the environment and printing less? The cost of paper becomes a concern once you have multiple employees and no printing policy. And the more you print, the more you use your printer, and the sooner you’ll […]
Arguing the Case: 3 Reasons for Law Firms to Use Managed Services
It is easy to make the case that law firms should seek out a managed services provider in order to save money on IT operations. Hiring a dedicated IT Solutions vendor can provide services and produce tremendous cost savings over a model in which the law firm must maintain and support an in-house IT department. […]
4 Simple DIY Computer Repair and Maintenance Tips
Instead of calling in your IT support team, sometimes it’s quicker to fix your own issues. However, this only goes for a few minor repairs. In most cases, if something goes wrong, it’s better to contact the professionals. Here are some easy computer repair tasks you can perform on your own: 1. Remove Unwanted and [...]
4 Plan Ahead Steps in Dealing with Plotter Repair
Large plotters are critical to businesses such as civil engineering, scientific companies, city building departments, design firms and more. Today’s laser plotters are robust and reliable machines that provide businesses with the ability to produce their own large-scale documents such as banners, posters, blueprints and marketing materials in-house. Any businesss relying on a laser plotter [...]
Data Security: What to do About Heartbleed
First thing’s first: make sure you understand what Heartbleed is and is not. It is not a virus – your antivirus software is completely unable to do anything about it. It is no doubt one of the most serious and widespread problems on the internet. What Heartbleed really happens to be is a security vulnerability [...]
“Basic Tech Tips” Blog Series: Remote Monitoring
Today in our Basic Tech Tips blog series, where we look at some of the terminology we use daily and get back to the basics, we examine Remote Monitoring. We found a great definition from Techopedia: "Remote monitoring and management (RMM) is a collection of information technology tools that are loaded to client workstations and [...]
5 Features Your IT Support Service Must Have
If you’ve finally made the decision to outsource your IT support services, then you’re going to start evaluating a number of different companies. You’ll learn a lot during the process. But before you even start, you should at least have an idea of some of the best features on which to compare your future IT […]
5 Preventative Printer Repair & Maintenance Tips
“An ounce of prevention is worth a pound of cure,” is a wise and true saying. But, it’s difficult to pull off in business because you have so much on your plate at any given time, that it’s hard to keep up with every last detail. So, hopefully this post saves you some time by [...]
Steps to Take When You Have an IP Address but No Internet Connection
A common help desk call for any user is when their internet connection is not working. After the obvious is ruled out (DSL line is down?? Did you remember to pay the cable bill this month??), and you realize that you actually have an IP address but no internet, you pick up the phone for […]
A Buying Guide for Small Business: VoIP vs. Hosted VoIP
Today, we introduce fellow Northeast Ohio blogger Brett Harney, Principal at Corporate Technologies Group in Hudson, Ohio to share with us his buyer’s guide for SMB’s on Voice over IP technology: A Buying Guide for Small Business: VoIP vs. Hosted VoIP We came across a great article on the basics of VoIP that explains the […]
How to Minimize Computer and Network Maintenance Costs
You don’t have to be a technological genius to keep your maintenance costs down. That helps, but there are some simple things you can do to reduce the frequency your computer needs to be repaired: Use Antivirus: Antivirus isn’t foolproof, but it helps prevent many catastrophic problems from occurring. And, it can be incredibly difficult […]
“Basic Tech Tips” Blog Series: Managed Print Services
This is our first installment in an ongoing series of blog articles where we take a step back and re-introduce some basic concepts in today's office technology. Today, we will be discussing Managed Print Services. What is Managed Print Services? I looked to the Gartner IT Glossary for a definition: "Managed print services (MPS) are [...]
Are You Making These 2 Deadly IT Security Mistakes?
Technology takes much of the threat of viruses away. But, it can only go so far. For example, if you visit a website, an ad pops up, and you click the ad, you can still download a virus that wreaks havoc on your computer network. The repair for that virus can cost thousands of dollars [...]
Easing the Pain of Varied Print Environments With Managed Print
Dental Services Group, a network of over 30 North American laboratories, provides dentists with the personal relationship and care of a local laboratory, combined with the technical expertise and full suite of offerings of a national laboratory. With 100+ geographically dispersed laser printers of various types and conditions, help desk support and supply management became [...]
Top 5 Benefits of Managed IT Services (And One Surprise Benefit…)
Just why would you outsource various IT processes? There are actually a number of reasons that make sense for any business. So today, we’re going to share some with you, and make sure you read to the end to get a special surprise benefit. Here are the top benefits your firm can experience when you […]
The Not-So Dreaded Office Move
Planning an Office Move? The key to any successful move is PLANNING. We found a great template offered by Microsoft to help. This Microsoft Project template will help you plan and manage your office move. The template has planning milestones for 2-6 months before moving day, 1-2 months before moving day, 2-4 weeks before moving […]
6 Ways to Help Your Printer Ink Last a Long, Long Time
Printer Maintenance Tips to Lower Your TCO Printer ink is one of the biggest costs of operating a printer for the long term. You might wonder why then, since Great Lakes Computer sells replacement ink cartridges, that we’d find ways to help you use less of it…and that’s because we value putting you first each [...]
Minimize your Risks for a Security Breach with a Data Protection Plan
Dell Secure Works has a great guide to minimize the impact of a security breach. Their first tip is regarding having a plan in place should a disaster strike. We are sharing this tip and their recommendations with our blog audience as it is a conversation we have with out clients frequently. No matter what [...]
6 Essential Computer Server Maintenance Tips You Can’t Ignore
If you’re executing a good deal of programs from your server instead of the cloud, you’re going to have to provide extensive regular maintenance for your server. Even if you don’t have to use your server much, it’s still wise to provide consistent maintenance to keep it operating smoothly. A preventative approach always reduces more [...]
Microsoft Continuing Support of Anti-Malware Beyond April XP Deadline
If you are a frequent reader and subscriber to our IT support blog, you will know by now that Microsoft will end support of Microsoft XP and their data security tool, Security Essentials, on April 8, 2014. For those of you wondering why this is such a big deal, consider that it is etimated that [...]
6 Essential Data Security Practices Every Business Should Use
Minimum requirements for SMB's to protect their data More than 110 million consumers had their credit card and personal data exposed in the Target data security breach. The whole process traces itself back to an e-mail phishing attack sent to employees of an HVAC firm doing business with Target. You can’t control how other [...]
3% of Expenditures on Printing, and Other Fun Managed Print Facts
80% of the Total Cost of Ownership of a Printer is from costs incurred after the purchase. Unauthorized or unnecessary printing can be the silent killer of profitability. Do you REALLY know how much these print costs are cutting into your bottom line? Some things to consider about your printing costs: Gartner Group found that [...]
Why Should Your Law Firm Use Managed Print Services?
Cutting Law Firm Expenses through your Printer Did you know that more than 80% of the cost of printing occurs after you’ve actually purchased the printer? Companies that produce printers and ink all know this. So if you’re a law firm looking to cut your expenses, one of the first places you should look is [...]
Great Lakes IT Support Employee In the Spotlight
Congratulations to Chris Toney, Great Lakes IT Support Employee, as featured in a recent ad for Cuyahoga Community College. We are always proud to hire great local talent (especially those with green shoes)!
IT Support Question: Can Managed Network Services Help Your Business?
So today, we’re going to take a broader look at managed IT services and what they can do for your business. First of all, what is meant by managed network services? Basically, Managed Network Services involve outsourcing various IT processes that you routinely engage in, and the benefit is that you have someone with experience […]
New Study Identifies Top 4 Reasons for IT Outsourcing
Managed Services monitor your IT with an expert eye IT staff regularly find that a lack of time or financial resources are the biggest barriers to productivity that they face. This is according to a new survey carried out by JDL Technologies; the study found that in response to these issues, 36% of those asked [...]
10 Dead-Simple Printer, POS, and Plotter Repair Tips
Printer, Plotter and POS Troubleshooting Tips Alright, so maybe not everyone can do printer, POS, and plotter repair, but hopefully these tips will make your life easier if you absolutely have to. Check out these tips, and hopefully they help you when you’re in a pinch: Printer problems - printing goes way too slow. If [...]
Why You Need Remote Monitoring for Less than $1 a Day
Give your business the edge with remote monitoring support If your business relies on its information technology to function, and most do, downtime can be a major cause for concern. Hardware failures that occur repeatedly will impact on the image of your brand, create problems for clients and drive down productivity. SMBs tend to be [...]
6 Amazing Computer Repair Tips for Struggling Small Businesses
Desktop Computer Repair Tips for Every SMB Recent research conducted by Intel found the average small business employee loses approximately one work week per year because they work on an out-of-date PC. Additionally, the study also noted: Repairing a PC older than 4 years costs 1.3 times more than repairing PCs younger than 4 years [...]
Microsoft Making a Statement by Extending Antivirus Protection
20-30% of Internet Users Still Use XP It's pretty well publicized and known now that Microsoft will be ending support for Windows XP on 4/8/14. However, an article by Tom's Guide / Elizabeth Palermo found here yesterday on Yahoo News reports that Microsoft will end support for their Windows XP Anti-virus application as well on [...]
Cyber Security Issues can “Target” Small Businesses
Protecting your SMB from the threat of cyber exposure Even if you have a current anti-virus and antimalware solution, your company could still be at risk of cyber fraud. Just ask some of the big box retailers! Unfortunately, online crime is not going away any time soon, in fact, if this past holiday's recent events [...]
9 Steps to a Successful Office Relocation
Office Moves are the Perfect Excuse to Upgrade your IT Systems Stressed out about the though of moving your office? You are not alone. Whether downsizing, upsizing, implementing a more robust remote work environment, or taking on new employees due to a successful merger, companies are finding that an office move is not an easy [...]
2014 Predictions for the Managed Print Services Sector
Competition will have managed print providers demonstrating real cost savings In the tech-heavy world of a modern office, there has been a gradual progression toward a paper free working environment. However, with each passing year, it is becoming clearer that the workplaces of the future will not feel compelled to make a choice between paper [...]
Three Quick Tips for Your IT Support Infrastructure in 2014
Housekeeping IT procedures for the coming year This slower end-of-year period is the ideal time to go over the finer details of your company’s software and make sure your IT systems are as productive as possible. The festive season gives business owners a unique chance to monitor and review their operation, without disrupting colleagues or [...]
Happy New Year From Great Lakes Computer
Here’s to another successful year! We have been proud to be one of Cleveland’s leading IT Support, Computer & Printer Repair, and Managed Print Services companies, and we look forward to continued success in 2014. Happy New Year!
Data Backup: A Chore or Hassel Free and Automated?
Selecting the right backup option for your company Every SMB owner is aware of the need for server/data backup, the problem is that getting the right service for your organization can be a minefield. However, do not let this confusion hold you back from finding the ideal set up, as delays can be costly. Jennifer [...]
Happy “IT Support” Holidays from Great Lakes Computer
Great Lakes Computer would like to wish all of our clients, employees, prospects and partners a very Merry Christmas and Happy Holiday Season. May your holiday season be “Computer Maintenance” Free! But remember, we are here should you need IT Support for your critical business systems.
Two IT Security Threats in 2014 You Can Avoid
Preparing your network security for 2014 The best kind of IT Support has a network security product suite that is able to tackle a number of diverse threats and prevent hacks or bugs from entering your company’s software system. One of the major components of any safeguarding software is a robust anti-virus and antimalware solution, [...]
IT Security Viewed as Second Largest Trend for IT in 2014
IT Security second only to Big Data in 2014 IT trends It is no surprise that threats to data security are on the rise. We are constantly hearing from security companies of new threats and attacks on company's networks and data. What we are hearing, though, is from those who stand to make a profit [...]
3 of the Most Important Questions to Ask a Potential MSP Vendor
For start-ups and SMEs alike, the right MSP is essential A Managed Service Provider (MSP) will perform far more tasks for the benefit of your company than simply outsourcing your IT will ever do. Whatever sector your company specializes in, you’ll need your technology to be up to date and capable, enabling you to compete […]
Data Backup is a Core Component of Computer Network Support
Safeguarding your company’s data with a reliable backup plan If you need to protect the information you store on your system, enabling it to be retrieved in the event of a partial or complete wipe out, data protection services are vital. Although there are many low-cost, or even completely free-of-charge options available, these are unlikely [...]
Convenience and Cost Drives Companies to Managed Print Services
Managed Print Services have a solid hold in market It is clear that the managed print services industry is maintaining a solid position in the market, assisting each customer in gaining a more technologically advanced and economically sound printing system. According to the October presentation of the International Data Corporation (IDC), the quality of MPS [...]
Five Things Great Lakes Computer is Thankful For
Happy Thanksgiving from your friends at Great Lakes Computer! We would like to share with you five things we here at GRLakes are grateful for this year: 1. Our Blog Subscribers! Without you, we would be writing this wonderful content that nobody would read. And while we all know blogs are great for SEO, ours [...]
Data Protection is Really All About Data Recovery
Managed IT Services Providing True Data Protection This article is shared with you from Asigra, written by Ashar Baig with Asigra. Great Lakes Computer is a proud partner and provider of Asigra Agentless Cloud Backup. We strongly support their message: What good is a Data Backup Solution if I can't get to my data in [...]
With Great (Data) Power Comes Great (Data Protection) Responsibility
Data growth means companies need to increase their data backup and recovery plans In a recently published blog post by Asigra, "Enterprise Backup Challenges Lie Ahead are you Prepared?" a new infographic takes a look at ever increasing trends in data growth within enterprises and the corresponding impact this growth is having on data backup [...]
POS System Options and Repair Services Reviewed
Getting the right point of sale system for your business There are many reliable points of sale (POS) business software packages available and these enable companies to add useful devices to their sales desks. It may be card readers, barcode scanners, invoice printers or computerized cash draws. Often, POS equipment comes pre-programmed with accounting capabilities, [...]
Why Law Firms Need an IT Policy for Data Security
Young Employees impact IT Support Policies at Law Firms A recent article on Legal Loudspeaker discusses why young employees at law firms are posing problems in data security due to their internet and computer usage. The article in its entirety can be found here. However, we believe some of the points are worth noting for [...]
If Your IT System Succumbs, Can you Afford the Ransomware?
Your IT Support must include robust data protection The latest threat to your company’s online security is a form of malware known as ransomware, a particularly unpleasant virus that holds your files hostage, and charges you for their release. Although we have come to appreciate the benefits of encryption, the Cryptolocker virus, as it is [...]
SMB’s Turning to Outsourced IT in Greater Numbers
SMBs turn to managed IT services to cut IT costs In these trying economic times, small- and medium-sized businesses are turning to an outsourced IT solution (Managed IT Services) in ever greater numbers. This kind of service gives companies the freedom to enjoy technologies that were previously the exclusive domain of their larger competitors. They […]
An Easy Way SMB’s Can Use the Cloud to Save Money
Cloud IT Support to Save Capital Expenditures It is invariably true that no single business strategy is appropriate for all firms. When it comes to cloud computing, however, the vast majority of businesses do find that it lives up to its central promise of reducing IT expenditures by reducing costs associated with on-premises infrastructure. Earlier [...]
Recent Cyber Crime Attacks and The Importance of AntiVirus Updates
Stay alert and protect your business from virus infiltration At a recent cyber security summit, the Attorney General of Nebraska, Jon Bruning admitted that even he had fallen victim to the crime of identity theft, underlining the very real possibility that anyone could be next. A second, possibly even less likely target was Schrock Innovations, [...]
AppAssure: End-to-End Data Protection
AppAssure is a unique backup software product In this white board video you’ll see how we’ve captured the capabilities of our product in a straight-forward yet interesting way. When you eliminate the data protection gaps found in most backup and recovery solutions, your organization can have even more assurance that it can access critical data [...]
How to Determine the Hidden Costs of Printing
MPS Providers more financially beneficial in terms of TCO Whether your business houses just a couple of printers, or an entire roomful, it’s likely that the running costs are a drain on your resources that you’d rather avoid. When you take the time to add up exactly what you are spending in terms of the [...]
200,000 New Cyber Attacks DAILY
War against cyber attacks thunders on According to research carried out by antivirus and antimalware experts Kaspersky, unfamiliar types of cyber attack are on the increase, with 200,000 now being reported on a daily basis, in comparison to just 25 per day in 1994. The problem of safeguarding an IT system is now twofold; not [...]
Unified Backup: Virtual & Physical
Dell AppAssure 5 vs. Symantec Backup WebBuyer’s Guide recently posted this independent whitepaper by openBench Labs: If you’re currently using or considering either Symantec Backup Exec or Dell AppAssure software to protect your Windows environment, you may already be aware that both products were reintroduced this year in significantly enhanced forms. This openBench Labs analysis […]
What to do with your Legacy PBX
Is it time to switch to VoIP? We get a number of clients asking us when is the right time to throwout their PBX and transition to VoIP. Whether they have grown as a company, or simply need the advanced features SIP brings, there are many compelling reasons to switch. And now, with the Mobile [...]
MSP’s Can Provide Remote Monitoring for Less than $1/day
Why choose an MSP to manage your IT network? Remote hardware monitoring is an increasingly convenient and economical way for businesses to enjoy the benefits of the latest technology, without having to employ the highly qualified IT staff required to administrate it. The services are provided through your network, rather than the more traditional route [...]
Dell AppAssure Whitepaper: Business Continuity
How Will Data Loss Affect your Organization? Losing your data or critical systems can mean: Revenue loss from the inability to conduct business Lost customer trust or confidence Financial penalties for violated SLAs Legal or financial penalties for compliance lapses Excessive recovery and repair costs for lost systems and data Organizations that would have absorbed [...]
Compare Data BackUp Software Before You Buy
SMB’s Benefit from Solid Computer Backup Plans Although most SMB’s are content to save their files to a computer hard drive, this may not be the most sensible way of storing the valuable information that goes to make up your company records. A number of factors could leave this information at risk of loss, and […]
SMB Alert: Google Announces Encryption of All Keyword Searches
Google to Encrypt ALL Keyword Searches: Say Goodbye to Keyword Data This blog is courtesy of Pamela Vaughan's Blog Post on Hubspot.com. You can read the full post here. However, we have pulled out bits and pieces that we feel are pertinent to our blog subscribers: many of whom are SMB's engaging in Search Engine [...]
Nearly 50% of Companies Had a Data Security Breach in Past 12 Months
Is malware getting past your company’s safeguards? Many companies assume their IT infrastructure is safe if they install recognized antivirus and antimalware software. Unfortunately, cyber criminals are both innovative and persistent, when one aspect of their fraudulent activity becomes blocked, they invariably seek out a new opportunity. Information gathered by Bit9 and the Information Security […]
Law Firm IT Support: Using Technology to Build a Virtual Law Firm
Video Chat on Creating a Virtual Law Firm I recently listened to a web conference by Attorney Stuart Price on TotalAttorney.com, and I thought I would post it for the legal followers of our blog interested in IT Support for Law Firms. He shared his experience using cutting edge technology to build a multi-office, multi-state [...]
Manufacturers Balance Tech Budgets with Managed Services Providers
Managed Services can support your business for less Over time we have become used to technology, such as smartphones and wireless devices, greasing the wheels of our everyday interactions, so we naturally expect the same of our work-based IT solutions. If a component of the system is not working, however, there needs to be a [...]
Managed Print Services Saves Companies 28% on Print Costs
Counting the costs of your printing Have you ever stopped to wonder what the true cost of your current printing solution could be? A new survey carried out by the technology and research company Gartner suggests that most companies are spending around 3% of their total annual costs on their printing system. This figure includes [...]
Norton releases upgrades to computer protection software
A Good Time to Ensure Your Data Protection Plan is Up to Date In the ever changing world of Anti-virus and Malware protection, it is not unusual to see a multitude of announcements from Anti-virus firms announcing upgrades. It is always important to pay close attention to your chosen provider's upgrades, as it usually indicates [...]
City Protects Mission-Critical Services with Dell AppAssure
Case Study for using AppAssure for City Government's Data Backup *The Following is a case study from Dell AppAssure. Great Lakes Computer is an Authorized Partner for AppAssure Software and Solutions. Just five miles from the Texas border with a population of approximately 38,000 folks, many who work in the oil industry, Hobbs, NM is [...]
Avoiding the Black Swan – a Guide to Disaster Recovery
The Black Swan Event - ready to take down your IT Systems According to our good friends on Wikipedia, a Black Swan Event is a metaphor that describes an event that comes as a surprise, has a major effect, and is often inappropriately rationalized after the fact with the benefit of hindsight. And in iTRACs [...]
Law Practices – Making the Case for Servers and Managed IT Support
Dell Whitepaper “How a Server Can Deliver for Your Business” Provides Examples for Law Firms Dell recently produced the whitepaper “How a Server Can Deliver for Your Business”, and there are a few areas to share with SMB’s, and especially law firms. The whitepaper provides 4 examples in the following industries: Consultants, Medical Practices, Restaurants, […]
Taking a Proactive Stance on Cybercrime with the Right Antivirus
Why SMB's need to go beyond pre-installed antivirus In a climate where cyber attacks are becoming a reality for every level of business, choosing the right antivirus and antimalware is a vital part of maintaining consumer confidence and safeguarding a company’s financial security. According to online security providers Symantec, in 2012, one in every 291 [...]
Moving? We Have the IT Support Moving Guide For You!
Are you moving your office? How are you moving your network? A move is the PERFECT time to reevaluate your Information Technology system and setup. BUT you need to ask the right questions. We offer a complete checklist for your big office move when it comes to moving your technology in our FREE Office Technology [...]
New Research: 40% Cost Savings with Managed IT Solutions
New study shows huge growth in MSP market and big savings for SMB's A study carried out recently by custom research company "MarketsandMarkets" appears to suggest a huge leap will take place in the managed service provider (MSP) industry by 2018. From its current position at $142.75 billion, the market looks set to grow to [...]
SMB Guide to Social Media – Shared by your Favorite IT Support Firm
Because we like to share more than just Computer Repair and Technology Advice... This Free guide from Offerpop we could not pass up sharing. Small-to-Medium business owners are always discussing the pros and cons of social media, and how to get it to really work for their business. I loved this workbook, as it not [...]
Why Cloud Computing is Generating Popularity for Managed Print
Print services boosted by mobile and cloud usage As every experienced observer knows, print services are in the throes of a major transformation. Along with other factors, the fall in popularity of desktop computers, has been widely felt in the industry. However, it is possible that the recent downturn in productivity will soon be a [...]
6 Reasons to Outsource Your IT Support Help Desk
6 Reasons You Should Outsource Your IT Support Helpdesk Having a professional IT Support infrastructure in place is essential for the modern business. The first point of contact for support is the IT helpdesk, yet for many businesses the cost of maintaining a full-time helpdesk team is prohibitive. Here are the most common reasons for [...]
BBB Offering Scam Alerts – Like an AntiVirus Software for your Life
BBB Launches Scam Alert Text Service As a proud member of the Greater Cleveland Better Business Bureau, I was exciteed to see the announcement earlier this month about a new service for consumers and business owners in which they will deliver scam alerts to you via text message. You can read the full article here, [...]
Managed Print Services Becoming the Norm
Managed print services gaining acceptance Managed print services have been around for over a decade now and they are currently reaching the point where they will become the norm for commercial enterprises. More companies are choosing to monitor their document management and print services remotely in an attempt to control costs and maximize efficiency. According [...]
Cloud Computing Data Security for your Smartphones and Tablets
Date Security on Mobile Devices: SaaS and Cloud Computing Smart phones and tablet computers have changed the way mobile computing works–and with it, they’ve raised data security issues across devices. Small business owners need to consider mobile device data security and tablet PC security to keep their computer data safe. Mobile Device and Tablet Data […]
Warning: New Malware Threatening Data Security
New kid on the malware block teaches SMBs old lesson Stealing account numbers and access passwords to financial resources is almost par for the course for today's malware, but according to Trend Micro, there really is something new under the sun: a malware program that also dedicates itself to harvesting FTP credentials. Businesses in this [...]
Free eBook: Technology in Today’s Law Firm
Making the Case for Managed Print and Managed IT Support Services There are several ways in which a law firm might consider organizing its IT services, but many of them have the drawback of throwing piecemeal solutions at a challenge that might be best addressed through an integrated approach. For an increasing number of law […]
Moving Your Office? Moving Your Computer Network With IT Support
How to Prepare for Office Technology Moves An office relocation can be a daunting task for any business, especially when zero downtime is a requirement. While most companies hire movers to move the big furniture and desks, what is often the most painful part of a move is ensuring all your technology and IT infrastructure [...]
Printer Repair Facts You Need to Know
Important facts about laser printer maintenance and repair One of the challenging aspects of dealing with a laser printer is the huge proliferation of brands and models, each one of which can feature its own quirks and idiosyncrasies. In the line of Hewlett Packard LaserJet printers alone, for example, models may appear to be very [...]
New IT Security Threat Tactics Proliferate During First Half of 2013
US is most prevalent spam producing nation in 2013 The midpoint of the calendar year provides businesses with a chance to evaluate their progress so far so that they can make more accurate predictions about the six months to come, adjusting to changing conditions on the fly. The anti-malware industry is no different, and since [...]
On Demand Webinar Discusses Cloud Computing and IT Infrastructure
Delivering on IT Transformation: Converged Infrastructure Drives Cost Down and Efficiency Up Just listened to this 60 minute webinar. It is a good one to share as I found it to be a conversation every organization must have – companies are spending way too much time and money dealing with the burdens of increasing IT […]
Cyber Criminals Targeting SMB Websites – IT Support More Critical
Data Backup and Disaster Recovery Growing in Importance to Small Business Survival I am continually getting phone calls and emails from colleagues and customers with stories of how they know an SMB whose website was targetted by cyber criminals. The stories are scary for any Small Business owner, who rely on their computer systems to [...]
Were You Surprised About The NSA?
M. Ursula Herrmann is Great Lakes Computer’s guest blogger on Government IT Security. You may also recognize her from her work on Crain’s Cleveland Business as a guest blogger on Network Security. Ms. Herrmann is a Network Security Analyst living in Juneau, Alaska. Network Security is not only her career but also her hobby as […]
Plotter Repair Services: What You Need to Know
What to know about plotter repair services Today’s modern laser plotters are robust and reliable machines that provide small businesses with the ability to produce their own large-scale documents such as banners, posters, blueprints and marketing materials in-house. Every business that comes to depend on running its own print shop, however, would be well-advised to [...]
GRLakes SMB Report: Small Businesses Got Me Off My Parent’s Couch
Monday kicked off National Small Business Week, and we at Great Lakes Computer found this blog post written by Corey Eridon with HubSpot to be a very informative piece for SMB's. You can read the original article here. How Small Businesses Saved Me From Living in My Parents' Basement Today kicks off National Small Business [...]
Why Instituting Data Backup Regulations Will Pay Off in the End
SMB's should avoid being penny wise and pound foolish on data security and IT support According to one of the latest studies in the data security field, businesses that decry the cost of following new regulations may well be putting the cart before the horse. Larry Poneman of the renowned Ponemon Institute has reviewed the [...]
A Lesson on IT Security – We are Under Attack!
Proper IT Security is the way to fight off attack. Came across this article on ComputerWorld.com and found it compelling for a number of reasons. Firstly, the message is on target. We are under attack. As the article states, last year, Symantec blocked a total of over 5.5 billion malware attacks, an 81% increase over 2010, [...]
IT Outsourcing Proves Invaluable for Law Firms
Keeping IT needs in-house can lead to a number of unfortunate situations It’s a well-known axiom of business that nobody is an expert at everything, a principle that applies not just to individual employees but also to entire firms. Why then, do businesses whose core competencies have nothing to do with information technology so often opt [...]
BYOD Forcing Creative Ways to Tackle Network Security
BYOD has company IT departments on edge about network security Bring Your Own Device, or BYOD, is increasingly becoming a common issue when companies address their network security needs. Whether it is laptops, smartphones, or tablets, IT departments need to establish a policy on what can be used on their internal networks, and how they [...]
“Managed IT services or cloud?” THAT is the question.
A little-touted advantage of Managed Services: the brand question Discussions about the benefits that come from working with a managed services provider very rarely focus on the issue of brand consistency. This is a bit curious, since it is one of the most important aspects of MSP use, at least from a marketing point of [...]
Professional Plotter Repair in High Demand
The need for professional plotter repair services The last few years of the computer revolution have seen a remarkable transformation in the world of printing, with the price of personal laser printers falling to radically low levels. Prices, in fact, have fallen so low that some small- and medium-sized businesses are beginning to take a [...]
Free Assessments for IT Support to First 15 Responders
Great Lakes: Allowing IT Support to Take a Vacation As your company's IT support lifeline, you are responsible for so much of the daily operations. And the last thing you want on your time off or vacation is phone calls from the office asking what to do about the server going down or the printer [...]
Can You Ban Vacation for your IT Support
Great Lakes Computer Preparedness Package Imagine this scenario: You're preparing for a meeting, and your PC starts acting up. You get a call from a coworker who notices your server is down. You immediately pick up the phone to call your IT guy, only to remember he is in Cancun on the beach enjoying a [...]
IT Security: You Can Teach an Old Dog New Tricks
IT Security and cyber threats surpass terrorism as top national security concern Providing small businesses with adequate data protection is like chasing a quickly moving target, and in the past few years, the pace of that chase has only been increasing. In March of this year, the state of computer safety reached a watershed moment; […]
Significant Savings of Managed IT Services
Powerful SMB solutions: managed IT services Small- and medium-sized businesses in search of an improved bottom line can save a significant amount of money by transitioning their tech service and support needs to a managed IT services model. Even better, unlike some types of business shifts that require months or even years to generate pay [...]
New Dell AppAssure Whitepaper on Disaster Recovery
Download the latest Dell AppAssure Whitepaper to ensure you are disaster ready Most disasters strike when you least expect them. Some – like hurricanes – give you more warning. But in either case, it’s a real problem if disaster brings your business to a grinding halt. Forces of nature, malicious acts, or even a simple [...]
Regulations Complicate Data Backup Practices
Cloud backup adoption in today's regulatory environment In the 21st century marketplace, information is the lifeblood of a growing number of businesses both large and small. Although this has made the need for adequate data backup increasingly obvious, there is a world of difference between on-site data duplication and cloud storage of essential data resources. [...]
Remote Monitoring is No Longer a Luxury
Remote Server Monitoring for less than $1/day - It is possible! Organizations, whether large, medium or small, need insight into the operations of their servers. However, unless they are a large company, many believe they cannot afford a robust, remote monitoring solution. Historically, SMB's have a hard time justifying the costs in their yearly budgets. [...]
Free eBook Explains the Key Elements of Disaster Recovery
Why you should update your data recovery plans Organizations have had decades of experience in planning for disaster recovery. • We know where the tapes are kept. • We have spare server hardware on hand. • We’ve protected installation media in a fire safe. • We have off-site copies of key backups. • And – […]
Cloud IT Solutions – The New Normal for Businesses
NIST fellow endorses cloud IT solutions Cloud IT solutions are increasingly coming into their own, becoming a standard business paradigm rather than being considered cutting edge technology, as was still the case several years ago. The situation is roughly parallel to what happened more than a generation ago with another game changer in the business [...]
When IT Support Takes a Vacation
IT Support in Business is the vital support system that all else depends upon As small and medium sized companies and organizations become increasingly reliant on their IT networks for maintaining nearly all aspects of their business, a great deal of emphasis has been put on finding the right IT person for the job. Once [...]
The Importance of IT Support in Business
We found this article by George Pettit that stresses the importance of having a robust IT Support System in place, and why it is imperative to have a backup plan in place when your IT Department is not available: The Importance of IT Support in Business By George Pettit Virtually every company depends on its […]
Data Protection Case Study for Educators and Government Agencies
Great Lakes Computer is proud to call ourselves a member of Dell’s PartnerAssure Program. Dell AppAssure is the industry’s leading software for backup and replication for voicemail, physical and cloud comuting environments. We also have a number of government agencies and School Boards we work with and provide services, from our managed print to our […]
Beware: “Changeup” Malware Threatening Data Security
"Changeup" Worm infecting SMB's and large businesses worldwide Few businesses want worms invading the premises, but night crawlers are probably preferable to what office supply retailer Staples has had to contend with during the past week. The company, based out of Framingham, Massachusetts, was forced to lock down its computer systems after it realized that [...]
Online data backup: no longer discretionary
SMB's recognize online data backup as a necessity A growing number of small- and medium-sized businesses around the nation are beginning to recognize online data backup as necessary rather than discretionary expenses. Increasingly, such businesses see data recovery as a critical need of the organization and regard online backup and recovery options as the most [...]
The Verdict is in on Cloud Computing
SMB's find that Cloud Computing significantly reduces cost It is invariably true that no single business strategy is appropriate for all firms. When it comes to cloud computing, however, recent data indicates that the vast majority of businesses do find that it lives up to its central promise of reducing IT expenditures by reducing costs [...]
IT Security Guest Blog: What the Government Needs vs. How the Government Thinks
M. Ursula Herrmann is Great Lakes Computer's guest blogger on Government IT Security. You may also recognize her from her work on Crain's Cleveland Business as a guest blogger on Network Security. Ms. Herrmann is a Network Security Analyst living in Juneau, Alaska. Network Security is not only her career but also her hobby as [...]
Government Data Security Organization Hacked
Irony of ironies: anti-hacking website hacked As anyone in business likely knows, government websites are far from ideal, often making it difficult to find information that should be readily available. The federal government's online presence, however, hit a new low this month when it was revealed that the very website designed to collect and distribute [...]
Best practices for network security and server backup
Network server backup for complicated, special cases Backing up the servers on a network is most often a straightforward process, particularly if the SMB involved has invested in a high-quality network server backup software suite. However, some businesses are using a data security arrangement that involves clustered servers. This can complicate matters somewhat. What are [...]
SMBs in Saudi Arabia waking up to cloud IT potential
SMB's worldwide embracing Cloud Computing Small and medium sized businesses around the world are increasingly investigating the potential that cloud infrastructure offers for streamlining and simplifying their business operations. A strong example of this trend is currently being seen in Saudi Arabia. This large Middle Eastern nation is generally classified as being in the earliest [...]
Malware Attack on NBC.com & more Data Security Threats
Malware: a cautionary tale for SMBs without a companywide policy The news of late has been filled with reports about widespread hacking of United States businesses by official branches of the Chinese government. Amid the hubbub, however, a hacking report of more potential interest to SMBs may have been overlooked. The National Broadcasting Network announced […]
50 Million Evernote Users Effected by Huge Data Security Hacking
Fifty million users should pay close attention to data loss prevention In one of the most extensive hacking events in recent years, an estimated 50 million individuals are being urged to reset their passwords on the Evernote service. The cloud-based Evernote platform is popular with a variety of end users ranging from college students to [...]
Data Backup and Security is One Place NOT to Cut Costs
The importance of server backup – Plus a Free eBook It is exceptionally important to ensure that a business server is backed up on a regular basis. It should be a task scheduled as regularly as brushing the teeth or any other essential ablutionary tasks. There are two methods with which data can be backed […]
Remote Monitoring Will Save You Money
Understanding remote hardware monitoring Given the ongoing global financial situation, and the fact that “cost saving” and “restructuring” have been phrases used around many boardroom tables, it should come as little surprise that remote hardware monitoring is on the increase. Unlike traditional “in-house” IT management solutions, a remote system for monitoring the performance and maintenance [...]
Hacking of Federal Reserve Heightens Emphasis on Data Protection
Attack by "Anonymous" of Federal Reserve provides key lesson in data protection Businesses, both large and small, need to sit up and take notice: none other than the Federal Reserve system of the United States has admitted that its networks have been breached. The incident has led experts to emphasize the essential nature of best [...]
Computer Repair Video: “Can I smash my printer with a sledgehammer?”
Great Lakes Computer’s new Computer Repair Video on 5 Steps to Resolve Printer Problems Did your printer get jammed again? What do the lights mean when I plug my ethernet cable into my printer? When is it appropriate to smash my printer with a sledgehammer? Get answers to these questions and follow these 5 steps […]
Cloud Computing: “Are we in the Cloud Right Now?”
Understanding the Benefits of Cloud Computing (Amy Poehler Should Read this…) When the term “cloud computing” appeared around the middle part of the last decade, many people were both drawn to the idea and repelled by potential risks at the same time. Most of the risks stemmed around the security of data when held in […]
Data Backup: Your Server Fail Like the Lights at the SuperBowl?
Make Sure your Backup Game Plan is Set! One of the things that make a disaster so catastrophic is the lack of notice before it occurs. If a server fails catastrophically and its data becomes unreadable, it is unlikely to send out a reminder before data is lost into the abyss. For these reasons, ensuring […]
New Computer Repair Video Shows Steps to Take When Hit with a Virus
Great Lakes Computer’s new video shows you steps to take should you contract a computer virus Should I close my browser right away if I get a virus? Should I click on any of the pop-ups prompting me to run a virus scan? Why does my browser keep taking me to sites that are not […]
SMB Best Practices: IT Security Policies Evolve with IT Systems
From Crain’s Cleveland Business Guest Blogger M. Ursula Hermann IT Security and Systems Evolve Over Time In the past, I’ve written about the cyclical nature of a security system of policies and procedures. Specifically, I wrote that security strategy is more like a spiral than like a wheel, because even though you come back to […]
Managed Print Services offer Savings up to 30%
Using managed print services When considering whether to use managed print services, there are a number of factors that will need to be analyzed. Through looking in detail at business printing needs, the scale of benefits in cost and time will become clear. It is widely believed that use of managed print services can save [...]
IT Security Guest Blog “Continuous Monitoring: You’re Doing It Wrong”
Great Lakes Computer would like to welcome M. Ursula Herrmann as our new guest blogger on Government IT Security. You may recognize her from her work on Crain’s Cleveland Business as a guest blogger on Network Security. Ms. Herrmann is a Network Security Analyst living in Juneau, Alaska. Network Security is not only her career […]
Avoid Costly Computer Repair with Legacy Systems Maintenance Plans
Companies sticking with legacy systems are far from alone The common perception of business IT systems is that firms both large and small generally strive to be on the cutting edge of technology – adopting flat-screen panel monitors, for example, long before such items became a common item for use with home PCs. The reality [...]
What Does the Better Business Bureau Actually Do?
Great Lakes Computer is a proud member of the Better Business Bureau. There are many misconceptions about what the BBB does for consumers and for businesses, and we found this blog article on their consumer blog very interesting and helpful: Consumer Misconceptions about the Better Business Bureau: “A big part of what we do is […]
Legacy Systems & Computer Repair – Third Party Maintenance
Legacy systems repair and maintenance: the IBM AS/400 The dawn of the information age has brought with it a number of new challenges to small businesses for computer repair and system maintenance. One of these is the legacy system, a phrase that applies to hardware as well as software. As technology advances, systems that were [...]
Cloud Computing Strategies for SMB’s
Is cloud computing right for your business? In recent years, the move from traditional IT networks to a system where applications and files are stored in the cloud has been rapid. When considering a move to such a system, it is wise to consider a range of factors such as cost, storage and security. Cloud […]
Data Protection Must Include Malware Prevention
Malware prevention: avoiding system vulnerabilities When it comes to malware, it is usually true that the best defense is a good offense. A company-wide coordinated anti-malware software suite will perform key functions such as alerting users to malicious websites before the browser actually loads them, and blocking incoming connections until they have been verified as […]
Third Party Computer Repair & Maintenance Key for Legacy Systems
Key reasons to maintain legacy systems The world of IT is in a state of constant flux. According to technology research company Gartner, the years to come will continue to bring innovations such as hybrid cloud IT solutions, in-memory computing, and even personal cloud computing. All of these have the potential to greatly impact how [...]
Trimming Excess SMB Costs: The Need for Managed Services
SMB’s realize the cost savings of Managed IT Solutions In this tough economic climate, small- and medium-sized businesses need to take advantage of all the cost savings they can find. Sometimes this involves difficult choices, but not when it comes to the issue of managed services. Unlike some cost-cutting moves, adopting a managed services model […]
SMB New Year’s Eve IT Solutions Resolutions
Consider these regrettable quotes as you plan for the new year in your Small Business: “Everything that can be invented has been invented.” Charles H. Duell, Office of Patents, 1899 “There will never be a bigger plane built.” A Boeing Engineer, after the first flight of the 247, a twin engine plane that carried ten […]
Top 7 Benefits of an IP Based Phone System
How SMB’s can cut costs with an IP Based Phone system Internet-based phone service has changed the telephony landscape. Businesses have realized huge savings by switching to Internet Protocol (IP)-based phone systems. Yet an IP-based system offers much more than just plugging a few new phones into your network. It can transform your phone system […]
POS Systems: Keeping your critical business equipment healthy
Extending the life of a POS system Small- and medium-sized businesses often operate under profit margins that mean they need to make every penny count – twice, if possible. Certainly, they need to be certain that they take the steps necessary to extend the life of their POS systems for as long as possible. This […]
How to Decide Which Data Backup Option is Right for Your SMB
Backup options for the truly small business Many computing options for small- and medium-sized businesses appear to be aimed at companies that have 50 or even 100 computers running on an integrated network complete with a server. For some SMBs, however, such a company would not appear to be a “small” business at all. Firms […]
Why Maintenance is Critical for SMB’s Printer Services
Printer services: periodic maintenance a must In some ways, the average office laser printer isn't so very different from a motor vehicle. Both need regular maintenance if they are to perform at their best. Moreover, both laser printers and cars are now equipped with sophisticated electronics that allow them to announce when the time has [...]
Why I Believe Printers Were Sent from Hell
We found this rant at The Oatmeal. Not only did we find it comical, but we think it is time to make a sales call there and tell them about the benefits of Great Lakes Managed Print Services! Here are a few of our favorites, but be sure to visit the full rant here for [...]
New Malware, Shylock, Intelligent and Very Dangerous
Smart malware takes computer safety concerns to new levels Modern forms of malware have long used a variety of strategies that help them hide from antivirus and antimalware programs, but a malicious program known as Shylock actually makes efforts to keep researchers from studying it. Such study is, of course, essential in order to develop [...]
SMBs Still Favor Face-to-Face Marketing Tactics
Content Marketing is most popular non-face-to-face marketing technique used by SMB’s Traditional, face-to-face tactics are still fundamental for SMB marketers: Personal relationships and networking (95%), tradeshows and industry events (89%), and in-person events (86%) rank as the most popular marketing tactics for finding new customers, according to a survey of small and midsized businesses conducted by Forrester Consulting for Act-On […]
New WhitePaper from AppAssure about Disaster Recovery
New WhitePaper Focuses on Virtual Environment Data Security In this whitepaper, Eric Siebert, VMware vExpert at Dell AppAssure, dispells the most common myths about Backup and Disaster Recovery in virtual environments.
Dell Computers standing solidly behind AppAssure Software
AppAssure named the superior product by Dell Dell Computers made network server backup news this week in none other than Paris, France when the company announced robust support for AppAssure, which Dell purchased in July 2012. The fate of other backup appliances in the Dell lineup has been in question ever since that time. Now, [...]
Symantec Warns About “Information Sprawl’s” Impact on Data Security
Information sprawl requires a robust malware solution Symantec’s recent 2012 State of Information Report is jam-packed with warnings and advice for the small- or medium-sized business, but perhaps the most important of these is the news that almost half of all business data is currently being stored outside company firewalls. This renders it far more […]
Data Backup & Recovery – Speed and Accuracy DO Matter
AppAssure offers disaster recovery in diverse SMB computing environments Some network server backup solutions specialize in providing excellent disaster recovery only for a single computing environment. While this might have been adequate in previous generations when the same technological paradigm tended to prevail at most small- and medium-sized businesses, it is no longer a satisfactory […]
Cloud Security Named in “Emerging Cyber Threats Report for 2013”
Cloud security a pressing issue for 2013 The Georgia Tech Information Security Center published information this week about the most serious threats to computer safety expected during 2013. The evolution of software and systems unfortunately brings with it a type of parallel evolution as hackers and cyber criminals seek to leverage new technologies in malicious […]
Managed Print Services – Something to be Thankful For
On this eve of Thanksgiving, Great Lakes Computer is thankful for our customers, avid blog readers, and for the excitement of the ever changing world of technology. But as technology advances, we are grateful that print is NOT dead. We have a new brochure that discusses the many benefits of our Managed Print Services. We […]
Symantec Warnings Stress Need for Increased Data Protection
Malware going mainstream, warns Symantec According to a recent computer safety survey by specialist company Symantec, malware may be lurking in places that users least expect. In previous years, hackers tended to focus their efforts on adult websites and other niche locations that regular business users were unlikely to frequent – including forums discussing methods […]
New eBook – 10 Backup & Restore Questions Every Admin Must Ask
This new eBook provides you with 10 important questions to ask yourself as you review your current data backup strategy along with 10 action items you can take to effectively protect your data. by Greg Shields, Microsoft MVP and VMware vExpert
The Hidden Benefits of Remote Monitoring
Business advantages of remote hardware monitoring Remote hardware monitoring is a fairly new technology, one that has truly become feasible to implement only since the advent of a strong, nationwide internet infrastructure able to operate at broadband speeds. Many small- and medium-sized businesses have already begun to harness the natural efficiencies of the internet for [...]
Is it a good thing that your employees can work with mobile devices?
The following is a blog about the security issues with mobile hotspots and other devices common in today's workplace, from Crain's Cleveland Business Information Security Blog, written by M URSULA HERRMANN. We have posted her blog posts before and they have been met with great reviews. This one should be no exception. When employees bring [...]
Print Driver Errors – The Need for Affordable Printer Repair
Laser printer repair issues: printer driver problems Most owners and managers of small- and medium-sized businesses probably think of a laser printer /maintenance-and-repair/printers---plotters/primarily as a piece of hardware, but in actual fact, modern printers and plotters need to have their software correctly configured in order to operate at peak efficiency – and sometimes, in [...]
An Industry Leader in Disaster Recovery for Many Reasons
AppAssure: advantages for business data backup Most businesses are well-aware of the need for regular network server backup. This awareness, however, does not necessarily mean that such businesses have hit upon the best method for meeting this need. There are, of course, a large number of possible IT solutions that can assist with backing up […]
Making the Case for Managed Services in Law Firms
Managed services: non-cost reasons for law firms to make a change There is a great deal to be said for the argument that law firms should seek out a managed services provider in order to save money on their IT operations. Handing IT functions to a dedicated vendor who can provide services remotely can produce […]
83% of SMB’s Do Not Have a Data Security Plan
SMBs need to take cyber security more seriously, study shows According to a new study, a large proportion of small business owners in the United States are laboring under a misapprehension regarding the true state of cyber security. More than three-fourths of respondents indicated on the survey that their own business can be classified as [...]
How “New” is Cloud Computing
Oracle’s Larry Ellison Bashes the Cloud Computing Hype We enjoyed how “humorous” this spirited discussion on cloud computing became, when CEO of Oracle Larry Ellison shares his insights into the technology.
How SMB’s can measure the impact of Social Media
How effective is your Social Media Strategy? Check out this new white paper by the industry analysts at Altimeter – The Social Media ROI Cookbook. 75% of organizations that have implements some sort of social media into their marketing strategy lack a holistic approach to measuring how impactful it is for their business. This report […]
6 Ways to Tell if Cloud Computing is Right for Your Business
Look to the Cloud for IT Support About the Author: Ramon Ray is an author, speaker, technology writer and former small business technology consultant. He publishes Smallbiztechnology.com, a website that helps small and medium-sized businesses strategically use technology as a tool to grow their businesses. Ramon recently joined the Manta team of industry experts. Get […]
Why a Firewall Isn’t Enough Anymore
Antimalware efforts: the importance of early detection Small- and medium-sized businesses utilize a variety of methods to promote computer protection. From firewalls to carefully assigning permissions only to users who actually need them, data loss prevention usually consists of a multi-tiered approach. Ideally, this type of layered approach will completely prevent the intrusion of malware […]
Reduce IT Support Costs with Remote Hardware Monitoring
What is remote hardware monitoring? Many businesses have become accustomed to a managed services approach to tech support as far as software monitoring and maintenance is concerned. To some, however, it may come as a surprise that the internet can also be used as a conduit for hardware-based information as well. Remote hardware monitoring is [...]
Free Tuition for Goldman Sachs’ Small Business Management Education
Everything Your Small Business Needs to Grow Goldman Sachs 10,000 Small Businesses at Cuyahoga Community College is a practical business management education program that helps you develop the skills you need to grow your company. If you are selected to participate, you also will receive a series of one-on-one business advising sessions from dedicated professionals […]
Antivirus and antimalware: the importance of a company-wide strategy
Admin Rights Can BackFire on You! Many employees who use computers routinely as a part of their daily workflow prefer to have administrator privileges over their machines so that they can install software as needed without having to wait for an IT department to provide them with services. While this strategy can provide some benefits […]
Outsourced IT services best for law firms, small and large
Law firms specific needs make a compelling argument for Managed IT Services Law firms have highly specific needs when it comes to IT support. Even in the modern age of computers and mobile communications, the practice of law remains an industry that is paperwork heavy. Unlike in some other industries, following precise formatting requirements is […]
How Managed Print Services Improve Efficiency
Improving company efficiency with managed print services Not so very long ago, the computer revolution was holding out the promise of a truly paperless office. All the information individuals needed, the conventional wisdom went, would be held in data systems and could be instantly called up onto video screens when needed, while sophisticated spreadsheet and [...]
Data Security MUST Include Regular Backup
The importance of regular data backup A robust data security policy must address several issues related to server and data backup. One of the most important involves the frequency of backups. It is in the company’s best interests to be sure that in the event of an interrupting factor such as a natural disaster or […]
51% Think Storms Affect Cloud Computing
Does severe weather impact cloud computing? As seasoned IT Professionals, we may chuckle at the question posed above. However, a recent survey from Citrix shows that many are still confused about what cloud computing is, if they ever use it, and if the National Weather Service is involved. Read the full article here for some […]
Professional Printer Repair – Facts you need to know about printers
Professional Printer Repair for your Business Equipment Small businesses and “one man shops” often avoid the need for printer repair completely by purchasing small, cheap printers that can be thrown away and replaced when they start acting up. This is not a realistic option for larger businesses and most SMB's, however. As most owners and [...]
Cloud Computing – Is it Time to Make the Move?
Is the cloud right for your industry? One of the most pressing questions facing small businesses across the board these days is whether or not software located in the cloud can provide cost savings great enough to justify a transition to cloud IT solutions. As more and more companies and even entire industries make the […]
Symantec Issues Data Security warning about Shamoon Malware
Another malware wreaking havoc on company networks Symantec is currently warning computer users that a new variation of the Shamoon malware has been detected. This most recent variant performs several different actions on infected systems. In addition to wiping data and destroying entire files by replacing sectors with random data, the new version of Shamoon […]
Just When You Thought Your Data Protection was Strong Enough…
How Hackers Erased a Digital Life in an Hour... When tech writer Mat Honan of Gadget Lab, a regular to the Wired blog, lost all of his digital life in the span of an hour, it should be a wake up call to everyone to increase their data security to new heights. Check out Mat's [...]
Understanding the Effects of Malware on Data Protection
Understanding the Impact of Malware The term “malware” is a shortcut way of referring to malicious software installed on a system without the owner's permission or knowledge. Malware tends to produce two major effects, both of them negative. Some malware is engineered specifically to interfere with a system's data security, altering, damaging, or even wiping [...]
How Small to Medium Businesses Can Use Social Media to Build Trust
One of the reasons we created the Great Lakes Computer Blog is to share information to further build the reader’s trust in us as a knowledge resource. We found that the recent article “How to use Social Media to Establish Trust” by Lisa Baron reinforced our practices. “Life as a small business owner is all […]
Download the Buyer’s Guide to Virtual & Physical Data Protection
This new eBook, courtesy of Dell AppAssure, will help you sort through the new as well as the more traditional data protection approaches, providing the background you need to select the right approach for your environment. About the Author: Greg Shields Microsoft MVP and VMware vExpert, is an independent author, speaker, and IT consultant, as […]
Differences in Cloud IT Solutions: Public vs. Private
Public vs. private cloud: essential differences When a small business decides to streamline operations and save money by moving resources or transactions into the cloud, one of the very first issues that must be faced is which type of cloud will best suit the company’s needs. Two principal types of cloud IT solutions exist: public […]
A Guide to Malicious Software and Their Threat to Data Security
A Basic Understanding of Viruses Trojans, and Worms Most small business owners have probably seen news reporting on viruses, worms, and Trojans, but they may not have a terribly clear understanding of how these forms of malware operate and present a threat to a company's data security. This is unfortunate, since knowledge is power. Business [...]
AppAssure Data Backup Video: Recovery via Remote Mount of SQL Data
AppAssure Data Backup Software Video Series: Recovery via Remote Mount of SQL Data AppAssure Product Demo
Improved Data Security Against New Threats
SSL or TLS Promote Improved Data Security Against New Threats In today's business world, there is virtually no company that can operate completely without computers and related technology. Large businesses and corporations usually have an entire IT department dedicated to providing for their needs and keeping company operations safe online, but those who run and [...]
Proper Care and Maintenance- POS Point of Sale Equipment
Proper Care and Maintenance of POS Equipment: Practical Considerations One of the lesser-understood issues when it comes to the proper care of point of sale equipment is the need for a restaurant or other small business to supply POS systems with clean electrical power. In fact, challenges related to a stable and steady electrical supply […]
AppAssure Data Backup Video: Restore a Volume(s)/ Live Replay
AppAssure Data Backup Software Video Series: Restore a Volume(s)/ Live Replay AppAssure Product Demo
Printer Plotter Routine Maintenance: The Importance of Cleaning
Most businesses that routinely use a laser plotter find it to be indispensable to normal operations. This is only one reason why a plotter should be kept in good repair, however; another is that professional plotters tend to be quite expensive. No CIO wants to be in the position of constantly calling for plotter service, [...]
Managing Risk – Data Security Strategy
Posted by M. Ursula Herrmann Crain’s Cleveland Business Guest Blog Post of 7-27-12 In managing risk, a line to walk in finding acceptable levels Mary Ursula Herrmann is a Network Security Analyst living in Juneau, AK. She has worked in Information Security for over 15 years, and obtained her CISSP in 2005. When discussing risk, […]
AppAssure Data Backup Video: Recover a File
AppAssure Data Backup Software Video Series: Recover a File AppAssure Product Demo
Webinar: Colocation- A Smart Choice for Media
Join Savvis colocation and media industry experts for a live discussion on the challenges and opportunities related to data center colocation for customers in the media industry. Our speakers will discuss the latest developments in IT managed services and provide use cases on colocation and related cloud computing services for media enterprises where safe guarding […]
CompTIA Releases Cloud IT Research
CompTIA Releases Research Regarding Cloud IT Solutions A recent study by the association for the IT vendor industry, CompTIA, explored the most common funding arrangements for the adoption of cloud IT solutions. Nearly 1,000 respondents consisting of both companies that rely on IT and business professionals heavily involved in IT issues, weighed in on the […]
Data Backup Government Regulations
Data Backup: A Matter of Both Necessity and Regulations The most obvious reason for any small business to contract with a provider for data backup and recovery is to ensure that mission-critical information remains available for ongoing use. This is far from the only reason to arrange in advance for data recovery services, however. In recent [...]
AppAssure Data Backup Video: Attachability Check for SQL
AppAssure Data Backup Software Video Series: Attachability Check for SQL AppAssure Product Demo
Point of Sale System Care: Fingerprint Readers
POS Peripheral Care: Fingerprint Readers Once a business decides to take the leap into the efficiencies offered by a point of sale system, the issue of POS peripherals is likely to arise. Many different devices can function as POS peripherals; the category is so broad that it encompasses items such as cash drawers, receipt printers, […]
Free Webinar- Eye on ROI
Webinar- Eye on ROI: Increase Visibility to Increase Your ROI As IT environments become more complex, and the role of the enterprise network grows, smart organizations recognize the need to monitor their network to ensure their ROI. Implementing an application-aware network performance management solution helps provide seamless communication, identifying challenges before they become problematic and maintaining […]
Data Protection Webinar
Free Webinar- Trends in Hyper-V Data Protection Imagine push-button recovery for Hyper-V virtual machines. Click… Done. In the old world of tape backups and file-based agents, that kind of speed wasn’t possible. Join Greg Shields of Concentrated Technology and Joe Hand of Dell AppAssure and learn how to be done with Hyper-V data protection. When: […]
Prompt Laser Printer Repair Pays Dividends
Prompt Laser Printer Repairs Pay Dividends in Rescued Productivity The common saying that “an ounce of prevention is worth a pound of cure” is definitely true when it comes to repair issues with the types of large, professional printers that are in common use in small- and medium-sized businesses. One example of this principal in […]
Free Webinar – Trends in Hyper-V Data Protection
Imagine push-button recovery for Hyper-V virtual machines. Click… Done. In the old world of tape backups and file-based agents, that kind of speed wasn’t possible. Join Greg Shields of Concentrated Technology and Joe Hand of Dell AppAssure and learn how to be done with Hyper-V data protection. The solutions that give you push-button recovery – […]
AppAssure Data Backup Video: Mountability Check for Exchange
AppAssure Data Backup Software Video Series: Mountability Check for Exchange AppAssure Product Demo
New Technology Guide Helps You Calculate Cloud IT TCO
You know you're moving to Cloud computing to save costs and enable your business to be more flexible. But do you really know how to calculate the TCO involved with moving your IT infrastructure and applications to the Cloud? Discover how to plan for—and minimize—the costs of your strategic investments in Cloud computing with this informative technology [...]
Cloud IT Solutions Moving into the Mainstream
The Movement into the Cloud Not so very long ago, running applications or using storage in the cloud was still a highly experimental activity. This may have caused some small- and medium-sized businesses to back away from the technology, preferring to wait for the time when it had been thoroughly tested and could be considered […]
POS System Maintenance
POS Systems Maintenance: Barcode Scanner Batteries One of the most important maintenance issues when it comes to POS systems concerns the batteries that are a part of many barcode scanners systems. Business managers and owners who take certain precautions with regard to batteries will find that their system stays operational for longer before new batteries […]
The New World of DLP: Cloud Data Loss Prevention
The New World of DLP: Cloud Computing Security Most tech departments have experienced the familiar issue of an employee becoming frustrated with his or her privileges on the company network. Workers want to be able to install and run the programs they feel they need, and they do not always react well to having to [...]
Laser Printer and Plotter Printer Repair: Key Considerations
Important Considerations Regarding Laser Printer and Plotter Printer Repair The computer revolution has changed the world of business in enormous ways, many of which improve efficiency even as they significantly lower costs. From a small business perspective, heavy use of information technology can be the best of both worlds, except when something goes wrong with the [...]
Data Protection Webinar- Dell AppAssure 5
Free Webinar: Introducing AppAssure 5 Beyond Backup Date & Time: Wednesday July, 18 @1:00 PM – 2:00 PM EDT (10:00 AM – 11:00 AM PDT) Join Joe Hand, AppAssure's Senior Director of Product Strategy, as he unravels the performance myths and realities surrounding data protection in virtual environments and provides a live demonstration of AppAssure [...]
AppAssure Data Backup Software Video: Recovery Point
AppAssure Data Backup Software Video Series: What is a Recovery Point? In this video, we walk you through the mechanics of a Recovery Point. What is a Recovery Point? What does it correlate to in the file system? And how to use and manage them.
The Need for Online Backup: A Business Analysis
Data Security-The need for online backup Ever since computers first revolutionized the business world, the need for data security has been paramount. Businesses invest huge amounts of their resources in creating essential data including such items as plans for the future and their database of current customers and their past orders. The nightmare scenario of [...]
FREE Webinar: Data Protection Midyear Review
Data Protection Midyear Review: Your 2012-and-1/2 Essential Checklist It’s the 2012 midpoint – time to look at what’s changed in backup and recovery and to take stock of how your backup and disaster recovery processes and solutions stack up. Join Greg Shields of Concentrated Technology and Joe Hand of Dell AppAssure as they guide you […]
Proper Care of POS Equipment
Proper Care of Point of Sale Equipment In many respects, point of sale systems are like any other kind of electronic equipment; they require periodic professional maintenance to remain functioning at their full efficiency. In some situations, a point of sale system will need to be repaired by a qualified technician. Like other types of hardware, [...]
AppAssure Data Backup Software Video: Deploying Agents
AppAssure Data Backup Software Video Series: Deploying Agents/ Protecting Servers Getting ready to deploy? This video will show you how to push the agent software from your Core server to the servers you want to protect using a simple wizard and the process of adding the server for protection. Our data protection services will ensure […]
Data Loss, Cloud Storage, and Redundancy
Data Loss, Cloud Storage, and Redundancy Everybody at one point or another in their life has gotten some very valuable advice from someone that really was intending to help them, save them, or just make them more wise. It’s also safe to say that everyone having received that advice multiple times in their life, has […]
Cloud Computing eSeminar
Cloud Computing eSeminar- The Need for Speed: Can Your Application Delivery Infratstructure Compete? June 28, 2012 2:00 pm ET / 11:00 am PT Duration: 60 minutes As IT environments evolve with the adoption of cloud computing, the need for flexibility and scalability becomes essential in managing IT infrastructure. Slow website performance can have a severely [...]
AppAssure Data Backup Software: Product Demo Video Series
AppAssure Data Backup Video Series- Intro to the User Interface Dell AppAssure Backup, Replication & Recovery from Dell AppAssure is incredibly easy to setup, use and manage. In this short video, you will see the basics for navigating in the product to get you started on your installation of testing of Dell AppAssure Backup, Replication […]
Video: Dell AppAssure Data Backup, Replication & Data Recovery
Dell AppAssure Overview- Data Backup, Replication & Data Recovery This video gives a quick overview of what Dell’s AppAssure software can offer your business in terms of data protection and recovery. AppAssure is the #1 unified backup and replication product that offers data protection for VM, physical and cloud IT environments.
Free Webinar: Quick-Start Guide to Virtualization
Quick-Start Guide to Virtualization- Getting it Done Right, Getting it Done Fast June 19th, 2012 12:00 PM Eastern - 60 minutes A Ziff Davis Enterprise eSeminar, sponsored by Dell and Microsoft. Unrelenting competitive pressures have SMBs looking to virtualization for the same reasons enterprises have for years: to reap cost-savings, efficiency and manageability benefits. Most [...]
Don’t Let This Happen to You! – The Importance of Managed Print
Printer Problems Plagued Local Government for Years Cleveland,OH- The Cuyahoga County government has suddenly realized their true print cost. A recent floor-by-floor census through dozens of buildings of Cuyahoga County’s office space revealed some shocking statistics. A staggering two thousand printers will be removed by the end of the year. You will be amazed by the amount of money […]
5 Misperceptions of Agentless VMware Data Backup
5 Misperceptions of Agentless VMware Data Backup Agents are small applications that are installed on a server to perform a particular function. Common examples are the agents that a backup application will install on a server to back up that server and provide specific support for the applications that run on it. Over the years […]
Data Backup and Recovery: Restore Terabyte-Sized Server in 5 Minutes
FREE Webinar: How to Restore a Terabyte-Sized Server in 5 Minutes...Guaranteed! Tuesday, June 5, 1:30 PM – 2:30 PM EDT (10:30 AM – 11:30 AM PDT) Five minutes? A terabyte-sized server? Ridiculous! Or, merely ridiculous with the data backup and recovery solution you’re currently using: A different approach to achieve 5-minute recovery of 1TB The right tools [...]
The Advantages and Disadvantages of Cloud Hosting
Have Concerns About Cloud Hosting? Take a Look at the Advantages and Disadvantages of Cloud Computing When it comes to hosting a website there are many different types of host servers to choose from. One of the newest and most popular methods is cloud hosting. Many people with both large and small websites are now [...]
Translating Technical Capabilities into Business Advantage
Communicating IT Solutions and Their Benefits to Management Technical people and business people don’t always speak the same language. IT managers and administrators who understand the business goals and realities of their company are able to evaluate and select technology that will help meet goals while staying within budget. In best case scenarios, the technology [...]
Free Webinar: Integrating IT & Facilities Management
June 5th, 3:00 PMEST: This free, 60 minute webinar shows you how to integrate IT facilities and management for a sustainable, optimized & managed data center. For years, data center professionals have debated strategies to provide a common program between facilities and IT. As data centers become more complex and increasingly resource-intensive, the need for [...]
Windows Server Disaster Recovery
Want to minimize the impact of disasters on Microsoft Windows Server applications? Windows Server applications are often mission critical. The impact of natural, random and man-made disasters on these applications, especially email, and their subsequent disruption can cripple an organization. This white paper from Dell AppAssure Software offers advice for protecting your existing Windows Server […]
7 Expert Tips on VMware Data Backup
7 Expert Tips on VMware Backup At small companies or in brand-new virtual infrastructures, backup appears easy. You may be able to use a free tool that came with your hypervisor that makes VMware backup deceivingly simple. However, over time, your infrastructure will grow, the virtual machine quantities will grow, and so will the virtual [...]
Top 10 Best Practices of Data Backup & Recovery for VMware & Hyper-V
Top 10 Best Practices of Backup, Replication & Recovery for VMware and Hyper-V Virtualization changes everything for IT infrastructure administration and management. One of the many traditional, and most critical, infrastructure management processes that server virtualization breaks is backup and recovery. Once server virtualization is in place, backup and recovery systems, as well as admins, […]
Compare Backup and Disaster Recovery Software Programs
New Whitepaper: "Performance Analysis for Backup and Disaster Recovery Software." An independent assessment of backup and disaster recovery software solutions performed by David Bourgeois, President of My IT, LLC. In this first hand account, the author evaluates performance limitations of Acronis imaging software, ARCserve tape software, MS SQL Backup for SQL, and MIMS offsite. The [...]
Free Webinar: Server Virtualization Savings Through Power and Cooling
MAY 22nd, 3:00 PM EST: This free, 60 minute webinar shows you how to maximize the ROI you can realize through power and cooling cost reductions when you virtualize your server. Server virtualization in the data center is a proven way to reduce the number of physical servers and reduce energy consumption. But is it [...]
8 Tips for Preventing Laser Printer Paper Jams
Your business can be completely disrupted if your laser printer is down, particularly if you find you’re in need of printer repair. These 8 tips can help you avoid a major cause of printer repair calls – paper jams. Paper jams occur in laser printers for a number of reasons, depending partly on the printer […]
Computer Repair: How to Troubleshoot a Wireless Router
By Lysis A Linksys wireless router is a popular brand used in the home for networking several machines. The routers provide Internet access for several home machines, including wireless computers such as laptops. Whether it’s your first time setting up the machine or you suddenly lose connection, there are some basic steps used to troubleshoot […]
Cloud Computing: 7 Myths About System Backup and Disaster Recovery
Understanding Backup and Disaster Recovery in Virtual Environments Means Knowing Fact from Fiction. In this whitepaper, Eric Siebert, VMware vExpert, dispells the most common myths about Backup and Disaster Recovery in virtual environments. How certain are you that you know the real facts? Data backup, server backup, and disaster recovery are necessary areas that all […]
Cloud Computing: Meeting Compliance and Security Standards
Compliance and the Cloud Posted by M. Ursula Herrmann Crain's Cleveland Business Guest Blog Post of 4-20-12 Cloud Computing presents some great cost saving and efficiency benefits to most businesses, but we continually advise clients to exercise care when moving their data and applications to the Cloud. A good example - compliance and adherance to [...]
Cloud Computing: What to Consider When Moving to The Cloud
Head into the Cloud Posted by M. Ursula Herrmann Crain's Cleveland Business Guest Blog Post of 4-13-12 Cloud Computing can make sense for many businesses, even those formerly communicating with remote workers via VPN. But as mobile workforces become more prevanlent, mobile security and cloud security need to be carefully addressed. This blog post is [...]
MicroSoft Exchange Server Support: Best Practices to Reduce Downtime
Are you the one everyone looks to when your MicroSoft Exchange server goes down? This whitepaper with forward by MicroSoft Exchange MVP Mark Arnold will give you three best practices to help you bring Exchange server downtime to a minimum. Does your backup plan take the entire Exchange environment into account? And is backup enough? [...]
How Data Deduplication Keeps Data Backup Costs from Multiplying
Are you paying double or triple for data backup due to duplicate data? This whitepaper explains the hidden “multiplier effect” of not taking data deduplication seriously. Find out how duplicate data can be pushing your data backup costs sky high. What is the real cost of duplicate data backup? The cost of continually backing up […]
Server Support: Top 5 “Musts” for Physical & Virtual Server Backup
Find out the top 5 “Must-Have” requirements you need to know about Server Backup. This Server Support whitepaper is a basic roadmap for IT managers to ensure that both your physical and vitual servers are secure. and downtime is reduced to a matter of minutes, not days. Facts About Server Virtualization: Server virtualization use continues […]
IT Support: The Benefits of a Free IT Assessment for Your Business
What is an IT Assessment? By Darryl Brooks This article will answer the question, “What is an IT assessment?” An IT assessment is a comprehensive and thorough review of a company’s technology systems and environment and will result in a written evaluation and recommendation. The assessment will appraise how your technology helps or hinders your [...]
Be Your Own IT Consulting Expert: Evaluating Cloud Computing Options
Be smart about evaluating emerging technology for your business. This article helps you become your own IT Consulting Expert by creating a process to evaluate technology for business use. Learn how to confidently evaluate new technology options like cloud computing, or SaaS (Software as a Service) to ensure your business leverages the technologies that make [...]
Mobile Data Security: Backing Up Your iPad Mobile Devices
Is your workforce going mobile, anxious to take their new Apple iPad's out on sales calls and other activities outside the office? Don't let your company data be at risk. Data security for your workforce's mobile devices begins with proper backup. How to Back Up Your iPad by Greg Hanson If you have ever suffered [...]
Server Virtualization for High Availability and Lower Cost
Server Virtualization Technology In default mode, a server will only function at a fraction of its available capacity leaving computer processing, memory, storage and networking resources redundant. Virtualization can put these expensive resources to work without significantly increased cost. The IT concept of virtualization is gaining in popularity. According to Gartner Research, "nearly 30% of [...]
Tap the Full Potential of Your Server With Server Virtualization
A Rundown of Server Virtualization Technology By Jen Kelly Computers have come a long way over the years, but this isn’t always so obvious when it comes to servers. Servers are computers that host information for other computers on a network. They have a lot of processing potential. A lot of power. And yet most [...]
Laser Printer Repair: How to Fix Blank Pages on a Laser Printer
by beconrad When the print quality on your laser printer begins to deteriorate, you should check the condition of the print cartridges. When the amount of ink in the print cartridge drops, the quality of the output will suffer and continue to deteriorate until the cartridge is changed. Sometimes, however, changing the print cartridge will [...]
Essential Server Repair and Maintenance Tips
It's no mystery that a server is considered to be the most important business machine for offices. Even though servers have multiple configurations and functions, the most common feature among small business servers is data storage. These servers act as a central location for users in need of frequently accessing stored data. Because this access [...]
How to Secure a Wireless Network
By J. D. Fencer Computer users are often so excited by the freedom they get with a wireless network that securing it is not their first priority. Some think they’re secure because the latest anti-malware and firewall software is installed on their computer. They seem unaware that, without strong router security, anyone within range could [...]
Implementing Security Systems on Mobile Devices
Securing Your Mobile Devices Information security systems for computers have been around for some time, but with the wide usage of mobile devices, we are now concerned about their security as well. Security mechanisms need to be carried out on these devices because we are using them to store more sensitive and valuable information. Some [...]
Cloud Computing: Video Explores Pros and Cons
Check out this quick video for a good overview of the "Pros and Cons of Cloud Computing" on the Manta blog. Overview "Small businesses need every advantage they can get, so many are turning to the cloud. While there are risks, cloud computing can help small companies grow bigger faster and save money. Get the [...]
Professional IT Support Can Be Crucial to Small Business Success
As a small business owner, time spent on IT support can end up taking time away from the things you need to do. You need to spend your time managing and running your business, without getting caught in an IT trap or the vicious break and fix cycle, which can drain financial resources, management time, [...]
Cloud Computing Enhances Small Business Productivity
Cloud computing is a buzzword that gets tossed around a lot, but it can offer the small business cost- and time-saving benefits. Small businesses often lack the time, IT services, personnel, and budget to devote to computing and security needs, getting by with a couple of computers and a shared hard drive instead of a [...]
What Cloud Computing Advocates Aren’t Telling You
Cloud computing is a major buzzword, and if you're a small business owner, you've probably heard about the time and cost savings this computing model can offer your business. While cloud computing may allow you to save time and cost, it's not always a perfect IT solution. Before you abandon your current technology model for [...]
Data Security for Cloud Computing and Mobile Smartphones, Tablet PCs
Smart phones and tablet computers aren't just nifty gadgets that make connecting on the go easier. They've changed the way mobile computing works--and with it, they've raised data security issues across devices. Small business owners need to consider mobile device data security and tablet PC security to keep their computer data safe. Another new computing [...]
Corporate College Catalog: Computer Maintenance & IT Tech Support
Thinking about advancing your knowledge about IT solutions such as Computer Maintenance and IT Technical Support? If you are a small to mid-sized business in the Cleveland, Ohio area, we encourage you to take a look at the Computer Repair and Maintenance & IT Support programs offered by our own local gem in small business [...]
Awarded the Best in Computer Repair & System Maintenance: 2011 Best of Avon, OH Award
Located in Avon, Ohio, Great Lakes Computer Corp. has served the Cleveland and Northeast Ohio area's needs for computer repair and system maintenance for decades. Typically working behind the scenes to keep your PCs, printers, and computer networks running smoothly, it's not often that we find ourselves in the spotlight. We are therefore very proud [...]
Cloud Computing: Get the FREE Cloud Computing EBook from Dell
If you are interested to learn more about finding IT solutions "in the cloud," we highly recommend this book from Dell as a must-have guide. Chapters include: Defining Cloud Computing and Software as a Service Benefits, concerns, privacy regarding using resources in the cloud Cloud computing security Migrating to and integrating Cloud IT Solutions and [...]
Cloud IT Solutions-Five Popular Ways Small Businesses Put Them to Use
It's 9:00 pm, you're working on a project, and you need to collaborate with a client across the country. Cloud IT solutions called "Cloud Computing" make this possible, evolving into one of the fastest growing types of computer technology for small businesses. The benefits of this type of Software as a Service (SaaS) can be [...]
Free Info Session: Cloud Computing & SaaS Software as a Service Training
Cleveland and Northeast Ohio small businesses are fortunate to have a great training resource like Corporate College. We've taken several of their courses, and believe they offer some great information on Software as a Service (SaaS), IT solutions, and network management. If you're a small business located in the Cleveland area and want to learn [...]
A Buyer’s Guide to Comparing Inkjet Printers vs. Laser Printers
Should you buy an inkjet or a laser printer? The choice can be confusing for a small business owner, but a few simple calculations can help. Differences in Print Processes Inkjet printers transfer tiny droplets of ink directly to the page. A laser printer creates an electrostatic pattern on a drum that attracts ink powder […]
Cyber Thieves Targeting Lax Data Security of Small Business
A recent article posted in the online version of the Wall Street Journal (July 21, 2011) had some very sobering news for small businesses: computer hackers and thieves aren’t targeting the data security of the big guys – they’re targeting small business instead. Just ask Joe Angelastri, the owner of a small newstand outside of […]
A False Sense of Data Security for Small Business Owners
Small businesses are often a step behind their larger industry counterparts in addressing data security, often believing they’re better protected than they really are because they don’t have in-house experts to advise them about where they really stand. Business owners of all sizes need to protect their vital data for the good of their customers, […]
Do You Really Need Anti-Virus or Anti-Malware Software?
What’s the Risk? There are about 75,000 new tier-1 pieces of malware coming out every day. Remember that number… 75,000 every day!. So your Anti-Virus software is realistically only going to be one layer of protection, no matter what the sales guy might say. That being said, AV is still a must. Remember the damage […]
Disaster Recovery: What You Need to Know About Hard Drive Failure
What can cause your hard drive to fail? A hard drive can be damaged due to firmware corruption, electronic failure, mechanical failure, a logical failure, a virus infection, or the drive developing bad sectors over time causing the data on them to be lost or unreadable. Any one or a combination of these issues can throw your […]